Online payments and transactions are some of the most sensitive online activities. They may be fast, convenient, and always seem to work flawlessly, but you should always be wary of the many digital threats that could derive from them.
New types of banking Trojans are recurring with an 80% increase in 2021. Mainly targeting Android users, banking Trojans have become one of the top 3 most common types of malware.
Here’s a close look at some of the most common and dangerous banking Trojans. Uncover how they work behind the scenes, so you know how to protect yourself.
Tactics of Some of the Most Common Banking Trojans
The strategy behind a banking Trojan is to capture keystrokes, get your banking information through a transparent overlay or even through screenshots. Some are more dangerous than others and can even lead to ransomware or stealing one-time passwords you receive on SMS.
FluBot
Android users are the primary potential victims of FluBot, but occasionally, iPhone users can be affected by FluBot. This malware will specifically look to get into your phone via apps installed outside Google Play store.
And it works like this: you receive a text message informing you that you either missed a call or have a new voicemail with a link attached so that you can listen to it.
Clicking on the link will take you to a website that looks exactly like the one from an authentic brand. In Europe, for instance, cybercriminals impersonated courier services. Once on the website, you will be required to install software to hear the message. And this is the tipping point!
If you agree with the installation, the FluBot malware unleashes! Perpetrators just opened the door to your personal information, including credit card details, the possibility of intercepting SMS texts and grabbing any other information from your phone. It can even see your contact lists and target new victims.
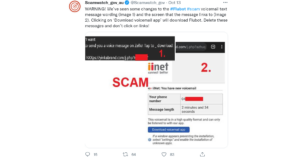
Find out more tips on how to protect yourself against SMS phishing.
Trickbot
Trickbot malware uses the oldest tricks in the book, like malicious links or file attachments. Trickbot attackers play upon invented stories related to invoices, holiday greeting cards, traffic violations, and the COVID-19 pandemic. They capture online banking credentials by sending you to a malicious and bogus webpage, namely a banking site.
Sometimes though, Trickbot gets more dangerous, as this malware can be the precursor of a ransomware attack. Also, bad actors behind Trickbot have continually changed the malware version, making it harder to spot.
Apart from credential theft, Trickbot can take the following forms:
-
-
- privilege escalation: spying on your activity to gain access to your system and network information and ultimately to your login credentials and email accounts.
- installing backdoors: accessing your system or device remotely or as part of a botnet.
- downloads of other malware: similar to a chain reaction, you get Trickbot inside your system after first installing another malware.
-
BlackRock
BlackRock has been targeting banking apps linked to financial institutions from Europe, the US, Canada, and Australia. Still, BlackRock didn’t stop at banks and further used its AMMO towards popular apps, including email service providers, online shopping sites, or social media platforms. Some examples of popular targeted brands are Gmail, Google Play, Amazon, eBay, Twitter, Skype, WhatsApp, and TikTok.
To make things worse, BlackRock perfectly hides in the background and grants itself additional permission without your knowledge.
For instance, it can send requests for admin privileges, collecting information about your device, and it will also not allow you to remove it if you suspect you’ve been a target of this malware. It automatically detects when you open antivirus apps and will redirect you to the ‘Home’ screen.
The tell-tale signs of this kind of malware are:
- device is running slow
- system settings are changed without your permission;
- new and unknown apps appear;
- data and battery usage increase a lot;
- your browser redirects you to shady websites;
- you’re bombarded with pop-up ads.
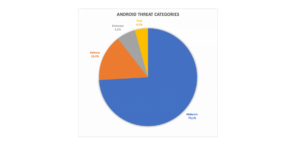
2020 Avira Malware Threat Report
How to Protect Against Banking Trojans
Banking Trojans are the kind of serious business you don’t want to ever deal with. So, here are some standard anti-social-engineering tips to ensure you stay away from banking Trojan (or any Trojan for that matter):
-
-
- Be wary and don’t jump into clicking links and email attachments: even if it’s from a known brand, maybe one where you have an account ( e.g., a regular online shopping store).
- Carefully check and look out for good reproductions of domains, spelling errors in emails and links, or unfamiliar email senders.
- Mind any “special” offers that don’t come from reliable or trustworthy sellers.
- Always download apps from legitimate and official platforms; never consider third-party downloaders.
- Keep all your software updated: this is always an important and easy step to prevent malware or any type of malicious program.
- Use a reliable antivirus: CyberGhost Security Suite covers Intego antivirus and Security Updater. You’ll stay away from online threats, detect apps that need updates, and check your outdated apps’ security impact.
-
Were you ever close to being deceived by banking malware?
Let me know in the comments section below.



Leave a comment