We talked with Dennis Kittrell, VP Product- Ummunify 360 about hardening security in Linux, the risks of not investing in security, and some of the common trends that have emerged through the Covid pandemic.
1. Please present your company and the products/services you offer in a few words.
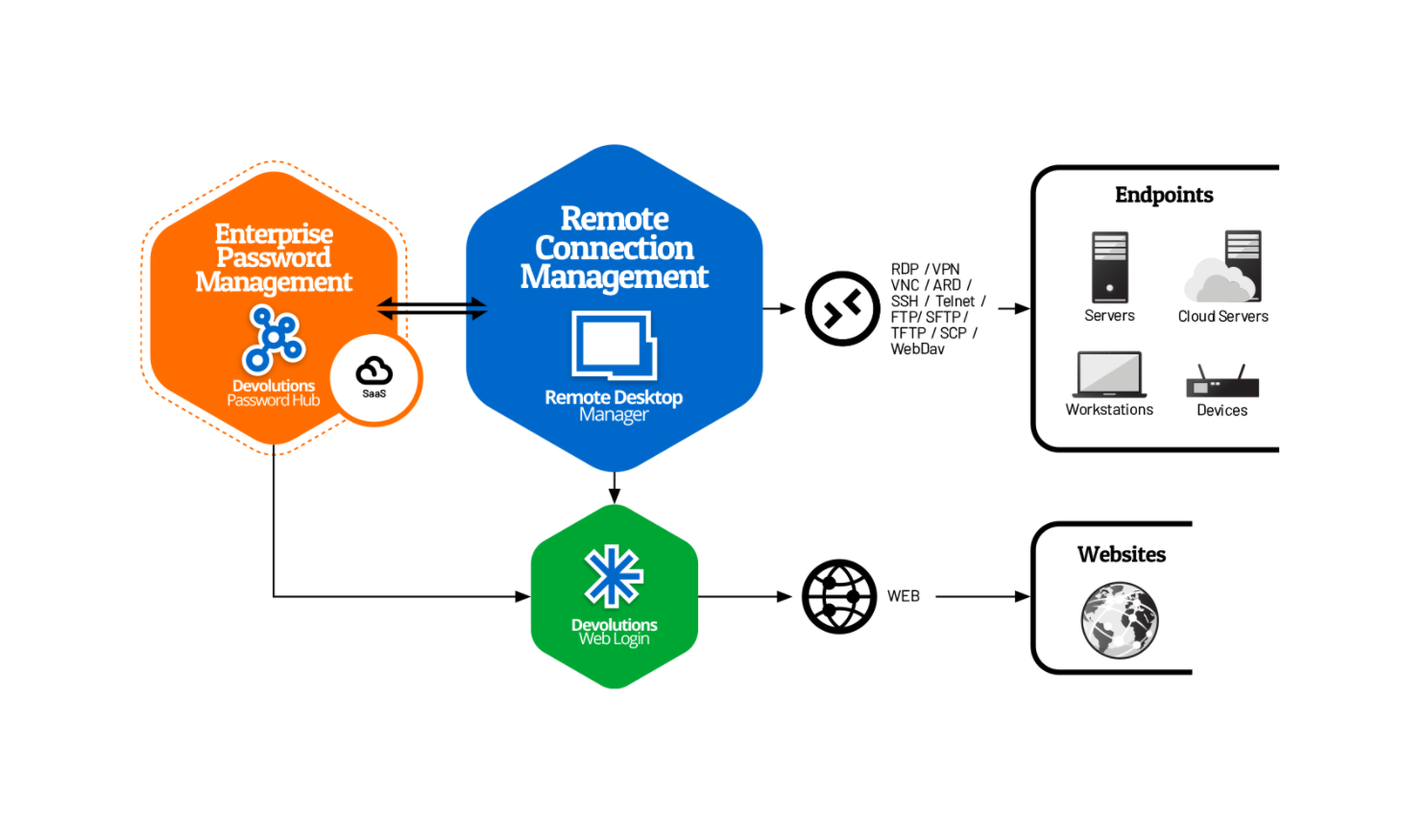
 Devolutions arms IT professionals with the tools they need to improve their productivity and provide enhanced security. Our suite of IT solutions is trusted by more than 800,000 users in over 140 countries. Geared toward small and mid-sized businesses (SMBs) – in this case, companies with under 1,000 employees – our software products include remote connection, password, and privileged access management. Each of these solutions can play a pivotal role in boosting an organization’s cybersecurity.
Devolutions arms IT professionals with the tools they need to improve their productivity and provide enhanced security. Our suite of IT solutions is trusted by more than 800,000 users in over 140 countries. Geared toward small and mid-sized businesses (SMBs) – in this case, companies with under 1,000 employees – our software products include remote connection, password, and privileged access management. Each of these solutions can play a pivotal role in boosting an organization’s cybersecurity.
2. What are some common beliefs or myths that instill companies a false sense of security? What are your arguments against these myths?
If you go back 10 years, SMBs weren’t the main targets for hackers and cyber threats. Back then, hackers didn’t have the same tools or the same hacking power – and it was easier to try to target larger organizations.
Today, with ransomware and phishing emails, hackers can target very wide and broad types of organizations, including SMBs. Now everyone can be a target of malicious campaigns, and businesses of all sizes need to adjust their cybersecurity strategies to reflect that reality.
We recently conducted a cybersecurity survey, which polled nearly 500 IT professionals from around the globe. One of the takeaways was that IT professionals are doing a very good job providing password management solutions to their employees, which is a good first step in implementing a good cybersecurity policy.
But hackers are looking for those passwords to get access to the ‘keys of the kingdom’ by accessing privileged accounts. They can then resell the data or install ransomware and ask for a ransom to access that data.
Our survey revealed that while 3 out of 4 SMBs have a password management solution in place, only 13% of the respondents said they have a privileged access management (PAM) solution in place. So, they do a good job managing end users through password management, but not a good job managing higher privileged accounts, which provide the keys to the kingdom.
In terms of PAM solutions on the market, most are high-end solutions that aren’t crafted for the needs of SMBs. That’s one of the reasons why we at Devolutions have been successful, as our PAM solution provides core features to SMBs but at a much lower price point and it’s also much easier to deploy.
3. As one of your reports mentions, some organizations have no idea they’ve been the target of an attack. Why does that happen, and what are the solutions for these organizations?
Hackers will often get into your business from the ground up – meaning they’ll try to get into your infrastructure using a password or an end-user’s credentials, then try to make their way up the ladder, up to where they can access those privileged accounts. After they get access to those privileged accounts, they can release some major damage to your business. And they won’t reveal themselves until they have access to those accounts.
That’s why cybersecurity audits twice a year are recommended. That’s what we tell our users as a best practice. At least twice a year, you need to take a look at your infrastructure security to see if there’s any flaw or malicious behaviors, so you can catch those hackers that are hiding in plain sight.
According to our cybersecurity survey, only 50% of the respondents said they were auditing their business twice a year, so 1 out of 2 companies. There’s still a lot of effort to be made in terms of cybersecurity, especially for SMBs.
4. Define and explain the difference between privilege access management (PAM) and the principle of least privilege (POLP).
PAM solutions are a set of tools that let you manage privileged accounts. This principle says that every user, application, server, tool, or client in your network only needs to have minimum access to the infrastructure up to where they need to do their job. For example, if I work in marketing, I should only have access to the tools and the security rights that let me accomplish my daily tasks. If I need to log into the CRM database, I have to ask permission to do this.
POLP (Principle of Least Privilege) means that end users only get the access they need to carry out their day-to-day activities. If elevated privileges are necessary for a specific project or activity, these should be temporarily granted, and then removed immediately once they are no longer required. POLP also works hand-in-hand with a PAM solution to limit, govern, and monitor the use of privileged accounts.
Some of the most important features to look for in a PAM solution are ease-of-deployment and management, account brokering, account discovery, automated password reset upon check-in, and more.
5. As many research studies showed, password security is still an issue for many companies. Do you believe this security practice should be easier to apply?
There’s a lot of passwordless strategies; we hear a lot about how passwordless will take over the need for passwords. We heard about this same kind of thinking 10 years ago; people were saying that in 2020 there won’t be any passwords. The reality is we have twice the number of passwords now than we had in 2010.
Passwords are nowhere close to being extinct from the workplace. While passwordless is a good strategy for end users to log into a computer, for IT professionals, you cannot support those technologies. It’ll take at least another 10 or 15 years to implement those passwordless strategies in IT departments.
Even though we’re trending to a passwordless future, we need to take action right now. Those passwords are the weakest link to your infrastructure; you need to put in place strategies like password management, PAM management, and privileged zero-trust principles in your organization.
The key point is even if you’re working in a small team, there are solutions on the market that can help you achieve that at a price point that actually makes sense to your organization. You don’t need to take a look at the ‘Ferrari’ of password management solutions to secure your environment.
In the last 2-3 years, more and more organizations, including SMBs, have realized that they need to take cybersecurity seriously. Today we are in this stage where organizations look for those quick-win solutions to enforce cybersecurity practices. That’s what we believe they can achieve, whether using our products or other products on the market.
Passwords are here to stay, but human interactions with passwords need to go away. Humans have to be taken out of the equation of password management. We cannot rely on a human to remember 50 passwords or work with hundreds of passwords in their organizations to different accounts and shared accounts with their co-workers. We need to rely on password managers to hide passwords from the user.

Our vision is to do account brokering; we strongly believe that copy-pasting a password isn’t the right solution. You have PAM solutions or password managers that can inject the password on your behalf, so you never get access to the actual password. We use our own solutions, and I log into dozens of different tools and websites every day. I never have to enter a single password; I don’t even have access to those passwords. The IT department manages those passwords on my behalf, using our solutions. Account brokering is the best way we feel businesses should work with passwords; no more copy-pasting or actually viewing those passwords, that’s not the way to go.
If we make it so hard for people to use those tools, they’ll write down those passwords on a sticky note or try to find another workaround. We need to make sure that these tools are easy to use and user-friendly, so it’s a no-brainer to use them.
You can put 10 locks on your door, and every time it’ll take 10 minutes to find the right key and the right lock on your door to get to your house. It doesn’t make sense; at some point, you’re going to want to get in through the backdoor because it’s easier. It’s the same thing in business. If it’s so difficult for someone to do their work, they’re going to find a workaround not to use your solution.
Some notable stats from our second Annual Cybersecurity Report:
-
-
-
-
- 72% of respondents are more concerned about cybersecurity now compared to last year.
- Top 3 cyber threats: ransomware, phishing, and malware
- 42% of respondents said they’ve faced one cyberattack in the last year – and 80% said they’re likely to be targeted by hackers now or in the near future.
-
-
-
In terms of budget, the majority of SMBs are spending the same or more on cybersecurity this year compared to last year. We can see that trend moving forward, where people are more aware and deploying more resources and solutions. In one or two years, I believe that we’ll see major improvements in terms of best practices.
6. Can you name two or three best security practices for remote workers?
Remote workers need to make sure that the remote technology they’re using to access their office infrastructure is secure. That is the first thing.
Second, IT professionals need to have visibility into who from outside the office is accessing their network. A best practice to put in place, besides password management and PAM, is to make sure that employees are aware of and educated about scams.
For instance, phishing campaigns in companies with remote workers is currently the number one vector in cyberattacks. Make sure that workers know about phishing scams and show them examples of phishing emails.
7. How do you see the cybersecurity challenges in the next two-three years?
IT professionals need to deploy the kind of solutions that stick, meaning their employees will use them daily and don’t find workarounds.
There are a lot of cybersecurity projects that are put on a shelf because they’re not usable on a daily basis. IT professionals need to be aware of that reality before doing a deep dive into a major cybersecurity project for their organization. Hackers have more capabilities – and are able to do personalized campaigns – so it’s important to know who’s trying to connect to your system.
Even here, at Devolutions, we get phishing emails on a regular basis, and they’re more and more targeted. These phishing campaigns are more personalized and fine-tuned, which is kind of scary. Passwords and end users are usually the weakest link to your cybersecurity policies. With hackers being more and more efficient at what they’re doing, they’ll probably be able to hack more and more users with their campaigns.



Leave a comment