The pandemic amplified the use of QR codes, so cybercriminals took advantage of this situation.
Posting private keys on various forums and users exchanging ideas on creating and selling fake EU green passes has already been going on for some time. Now, it seems this technique went a bit over the top.
The EU Commission is currently investigating faked COVID Certificates from several countries that seem to have valid signatures. In other words, they’re perfect QR code replicas that fool certificate validation apps.
Furthermore, the investigation’s result could lead to the re-issuing Green Passes of over 270 million EU citizens, including the perfectly legitimate ones.
Let’s uncover all the details behind the forged COVID Certificates scheme and its potential implications.
The Game Plan of the Forged COVID Certificates
This week, messaging app users (mostly Telegram) have started to see private keys for EU’s Digital COVID certificate. The certificates were fake but with a valid signature, as the signature is the one that’s supposed to protect against tampering.
Then, an Italian news agency came forward showing reports of underground sellers offering Green Passes that had stolen keys taken from the Dark Web. Similar actions took place in Poland, where COVID Certificates were sold for the price of $300.
Basically, these bad actors might have been and can still use forged certificates to trick official government apps. EU citizens use a Digital COVID certificate, many times in the form of a QR code, as an entryway in public institutions, restaurants, and is also their vaccine passport, helping them travel in other countries.
Clearly, apart from proving the security vulnerability of these Green Passes, threat actors had a sense of humor. Among the forged certificates, they created ones for Adolf Hitler, Mickey Mouse, and Sponge Bob.
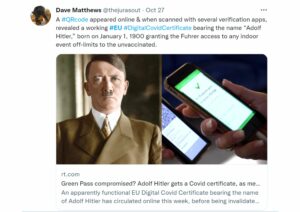
Different penetration testing companies have checked the validity of these certificates and came up with contradictory results. In some cases, the validation apps treated the QR code as valid, while in others, the apps didn’t recognize the code. This only makes the situation even more bizarre.
The more concerning aspect is this leak creates a massive mistrust in the overall security system of Green Passes. Cybercriminals managed to create forged certificates for users from several EU countries (France, Germany, Italy, Poland, and others), so this isn’t an isolated case.
The EU is currently investigating the situation, but the outcome of the certificates’ leak could impact over 270 million EU citizens. In the worst-case scenario, even legitimate COVID certificates might need to be invalidated and re-generated as fresh Green Passes.
So far, the EU Commission declared the breach didn’t compromise the cryptographic keys used to sign certificates. EU representatives also mentioned it wasn’t a technical failure that led to this incident but illegal activities.
The Conventional Process of a QR Code Attack
Attacks on QR codes are quite common and relatively easy to manipulate. Here are the main attack methods:
Malware injections
Cyber-attackers can infect your phone with malware if, just out of curiosity, you scan a QR code you receive in an email (it can perfectly seem to come from a legitimate contact) or text message. The scan sends you to an infected website that instantly prompts a malicious download.
Another way to inject malicious codes is by releasing free encoding tools on the internet to make QR codes. Scammers print the QR code on adhesive paper, place it over a legitimate one and send the malicious QR code via email.
Phishing scams
Cybercriminals trick you into going to a phishing website, so they can steal your passwords or access private information from your phone. Some phishing websites are hard to recognize, especially since they replicate similar URLs or just slightly change their spelling; other times, scammers change the domain (e.g., from ‘org’ to ‘com’). Once on the website, you’re requested your credentials, and if you log in, you’ve just been phished!
Exploiting bugs in QR code readers
As with COVID Green Passes, attackers always challenge themselves in finding security vulnerabilities and exploiting them. Their purpose can be to launch illegal activities, such as swapping legitimate QR codes with fake ones to make transactions go into their bank account. Other times, they manipulate your phone camera or sensor and, this way, capture sensitive data. They could track your location, steal your credentials and even make online posts pretending to be you.
How to Not Get Fooled by Fake QR Codes
The common problem with QR Codes is that many are curious and tempted to scan a QR code just to see what’s behind it. Let’s just say in this case, curiosity isn’t a positive attribute, and it’s best to stay alert!
Here’s what you can do so you don’t become the target of a QR code scam:
1. Don’t scan from unknown sources, even if it’s a physical place or an email from an unknown person.
2. If you can, touch the QR code and see if it has a sticker applied over it; if it does have a sticker, don’t scan it and ask for clarifications from the company that issued the QR codes.
3. Use a safe QR reader app: check its security features carefully; a highly safer app allows you to check the content of a link before clicking on it.
4. Whenever you find what you believe to be a forged or malicious QR code, report it to the business owner where you uncovered it.
Did you ever had troubles with QR codes? Or did you ever encountered a fake one?
Let me know in the comments section below.



Leave a comment
M B
Posted on 03/11/2021 at 21:53
I have an easy fix for this…….get rid of the grenn pass all together and get on with life like we have always done with other vaccinations.
Dana Vioreanu
Posted on 04/11/2021 at 15:51
Yeah, that could be an option. 🙂 Still, in most countries now, getting on with our lives requires exactly to have this Green Pass.