How often do you see ads on blogs, videos, social media channels, mobile games, or news sites?
More often than you can count, I guess! It seems impossible to do anything online without being bugged with ads.
What if I told you that, worse, ads are the weapons cybercriminals use in a malware variant? Would you be less welcoming? Adware is one of the most common cyberthreats infecting over 50 million devices annually.
Here’s what makes adware such a lucrative business and what you can do to protect yourself.
What Is Adware and How Does It Work
Adware is short for advertisement-supported software. It originated as a way to provide freemium services to users while financially supporting the software’s developers. Its main purpose is to get you to view and even click on pop-up ads.
Developers can even program adware to collect private information, like login details, credit card information, and browsing preferences. That’s why many consider adware as a type of malware that serves unwanted and intrusive online ads – most often, within your web browser.
Adware generally hides as browser cookies or temporary internet files. That way, it runs silently in the background and serves you with ads. Since you might not check your browsers’ history and cookies, an adware infection could fester undisturbed for months at a time.
That’s why you need to pay attention to any suspicious activity. Here’s what you should look after if you suspect you have an adware infection.
How to Tell If You Have an Adware Infection
Adware is generally obnoxious because it relies on intrusive ads – the number one sign of an adware infection. That said, ads aren’t enough to correctly diagnose an adware infection. Make sure you keep an eye out for the following signs:
- Sluggish browser without doing any data-heavy activity
- Frequent browser crashes
- New ads and banners show on websites
- Changes to your homepage that you can’t seem to change back
- Malfunctioning ad-blocker which you can’t seem to fix
- Redirected traffic
- New extensions, plugins, and apps that you didn’t install appear on your browser
Is Adware Illegal?
It’s pretty murky. Adware can be a potentially unwanted program (PUP) or outright malware, but it isn’t illegal to develop one or the other. Software showing ads – annoying or not – is also not illegal.
Tricking people into downloading adware? Now, that’s illegal.
Displaying intrusive ads that have no close button? That’s also illegal in many countries like Germany, France, and Iceland.
Disguising malware as ads to record your internet traffic? You guessed it; it’s illegal.
Nowadays, developers legally need to specify their app’s purpose and the permissions it needs. It’s also a prerequisite for having your app available on the Google Play Store, App Store, PlayStation Store, or Microsoft Store.
When you install an app, you need to consent to any and all app permissions, like access to your gallery, your contacts, or your social media accounts. Malicious apps won’t ever ask for your consent, which already violates laws like the Privacy Act or General Data Protection Regulation (GDPR).
Data misuse is why many view adware as illegal.
If you’re wondering how to spot adware, let’s go through some typical adware examples.
Adware Examples
You can find hundreds of malicious adware programs that have caused havoc over the years. Here are 5 examples that show you what to look out for.
1. Fireball
A Chinese digital marketing agency developed Fireball as a browser hijacker. In 2017, Fireball infected more than 250 million computers worldwide. One-fifth of those were connected to corporate networks.
The Chinese agency designed the adware to take over your browser and change your homepage to a fake search engine called Trotux. This should be your first and most obvious sign of a Fireball infection. You can’t seem to change your homepage settings or the default search engine? That’s your second sign of infection.
Trotux collects data on the websites you viewed to profile you and send you obnoxious ads during your browsing session. Most antivirus software these days should be able to quarantine the infection if you run a scan.
2. DollarRevenue
It’s currently unclear who developed DollarRevenue and for what purpose. The IP address which hosted DollarRevenue is registered in the Netherlands, but cybersecurity research found that multiple other IPs worldwide spread the adware. The DollarRevenue developers programmed it to install a browser toolbar to track all online searches. While its main purpose was to record and siphon personal data, you could easily recognize DollarRevenue by its fake ads pop-ups. As soon as you click anywhere on the page, the adware bombards your device with ads full of typos, grammar mistakes, illogical statements, and unregistered brands.
DollarRevenue is now thankfully defunct, but in the mid-2000s it infected over 22 million PCs worldwide.
3. Gator
Gator got its name from its alligator icon in the system tray, but no one really knows who created it and for what purpose. It caused a controversy in the early 2000s. In 2003, Gator Corporation developed adware to research behavioral marketing strategies. They bundled Gator with popular free software like Kazaa and Go!Zilla. That was how the infection spread to 400,000+ devices.
Gator worked by removing legitimate ads from websites and replacing them with its ads. At one point, Gator turned into a full-fledged spyware program as it started recording people’s browsing history and financial information. Gator reached its peak with Windows XP, and luckily it’s very rare to have a Gator infection with later Windows versions.
4. DeskAd
DeskAd infections start out subtle, with the adware running silently in the background causing little to no interference. It can even take a few weeks until DeskAd completely takes complete control over your browser. It also overrides your device’s registry so that it can automatically launch on startup. After installation, DeskAd displays typical adware signs, like showing annoying pop-up ads, redirecting your searches, changing your homepage, and slowing down your browser.
A DeskAd infection is so nasty, only a full device wipe can rid you of it.
5. Appearch
No one is really sure where Appearch came from, but cybersecurity experts consider it to be the precursor of a modern browser hijacker. It was generally part of a free software bundle, which is how it managed to infect devices.
Besides throwing a lot of ads at you, Appearch takes control of your browser and redirects your traffic to appearch.info no matter what you’re trying to do online. You can also easily recognize Appearch by its permission pop-ups. The adware will occasionally inform you that access to the webpage you want to visit is limited unless you subscribe to something or give permission to notifications. As soon as you click “Allow” on the prompt, you’ll notice a significant increase in pop-up ads, and you won’t be able to change your browser settings. That allows other malware to infiltrate and infect your device. Appearch makes surfing almost impossible because of all the ads it displays.
Now that you know what to look for, you also need to know how adware spreads to avoid downloading them by mistake.
How Does Adware Spread?
Cybercriminals tend to trick you into downloading and installing adware. Check these 6 main channels they use so you don’t mistakenly tune in.
- Software you already have
- Ad pop-ups
- Social media messages
- Infected code
- Drive-by downloads (installing without your consent)
1. Email Phishing
Emails are a popular way to spread all types of malware, and adware is no different. You can receive malicious software that runs adware as an attachment. As soon as you save or install the attachment, the file would start exploiting vulnerabilities on your device to plant adware.
Phishing emails look like legitimate emails from reputable companies but they’ll include links to a fake website that mimics a download page. Yeah, you guessed it! The file you’re trying to download is adware.
2. Outdated Software
It’s time-consuming to routinely check all your apps for updates – especially those you use only once in a while. Cybercriminals know that and make it a habit to exploit vulnerabilities in older software, injecting Java scripts, abusing cross-site scripting (XSS) flaws, and exploiting software modules. Cybercrooks trick your device into loosening its security restrictions long enough for them to install adware.
3. Ad Pop-ups
Many websites have pop-ups. Some are ad pop-ups, but not all ad pop-ups are sales pitches. Some don’t redirect to a retailer but a website packed with online threats, including adware.
You might be familiar with “hoax adware”, the kind claiming that your PC is infected with a virus, or that you’re the 99,999th visitor to the website and eligible for a prize. These are the ads that try to get you to click on them so that they can install malware.
4. Instant Messages through Social Media Platforms
Now that almost everyone has a social media account, cybercriminals keep a close eye on social media profiles. To do so, they create fake social media accounts and impersonate a wide variety of people.
They could pose as a sickly lonely older person, a rich guy in a designer suit looking for a personal secretary, or even a celebrity. Cyberattackers use their newfound fake persona to lure you in. They send out instant messages or leave replies that link to malicious software. LinkedIn, Facebook, and Instagram are popular platforms for spreading adware.
5. Injecting Infected Code
Cybercriminals can exploit vulnerabilities in your app to inject infected code and malicious Java scripts. You can’t clearly spot a vulnerability unless you take a look at an app’s source code. Some apps, like Adobe, have had 400+ reported and exploited vulnerabilities.
The only way you can stay ahead is to regularly install updates and security patches whenever they’re available. Otherwise, adware can get on your device and exploit any potential security holes to infect other local files.
6. Drive-by Downloads
Drive-by downloads are common on suspicious sites where malicious parties put up software bundles infected with adware. You might be looking to install a legitimate app, like a video editor, but an installation pop-up will mention that you need to give permission to install a by-product of the video editor too. That’s a well-hidden adware script!
It seems adware is anywhere and everywhere, but you can successfully protect yourself from those malicious intruders.
How to Remove Adware?
Since adware comes in different shapes and sizes, removal isn’t a one-size-fits-all fix. Your number one defensive behavior is to install an antivirus or anti-malware app on all your devices. A good antivirus app will detect and flag the adware file before it has any time to cause damage.
Get in the habit of running routine scans. Don’t wait until something fishy happens.
That’s the best adware protection you can achieve.
Scroll down to the operating system you’re using to see how to remove adware.
Windows Adware
Windows Adware is probably the oldest type of adware out there. That means you’ll find more variety in adware variants for Windows devices. The most common ones include:
-
-
-
-
- Adware.MindSpark
- Adware.InstallCore
- Adware.SearchEncrypt
- RiskWare.BitCoinminer
- Trojan.Emotet
- Adware.IronCore
- HackTool.FilePatch
- Adware.FusionCore
- Adware.Crossrider
- Adware.Spigot
-
-
-
In most cases your antivirus will detect and quarantine an adware infection.
While rare, some adware variants do a good job of evading antivirus apps.
If you have reasons to suspect that you are dealing with a particularly persistent adware infection, your best option is to restore your device to factory settings.
- Backup all your files and data
- Press the Windows button
- Type in ‘reset’ and select ‘Reset this PC’
- Follow the on-screen instructions
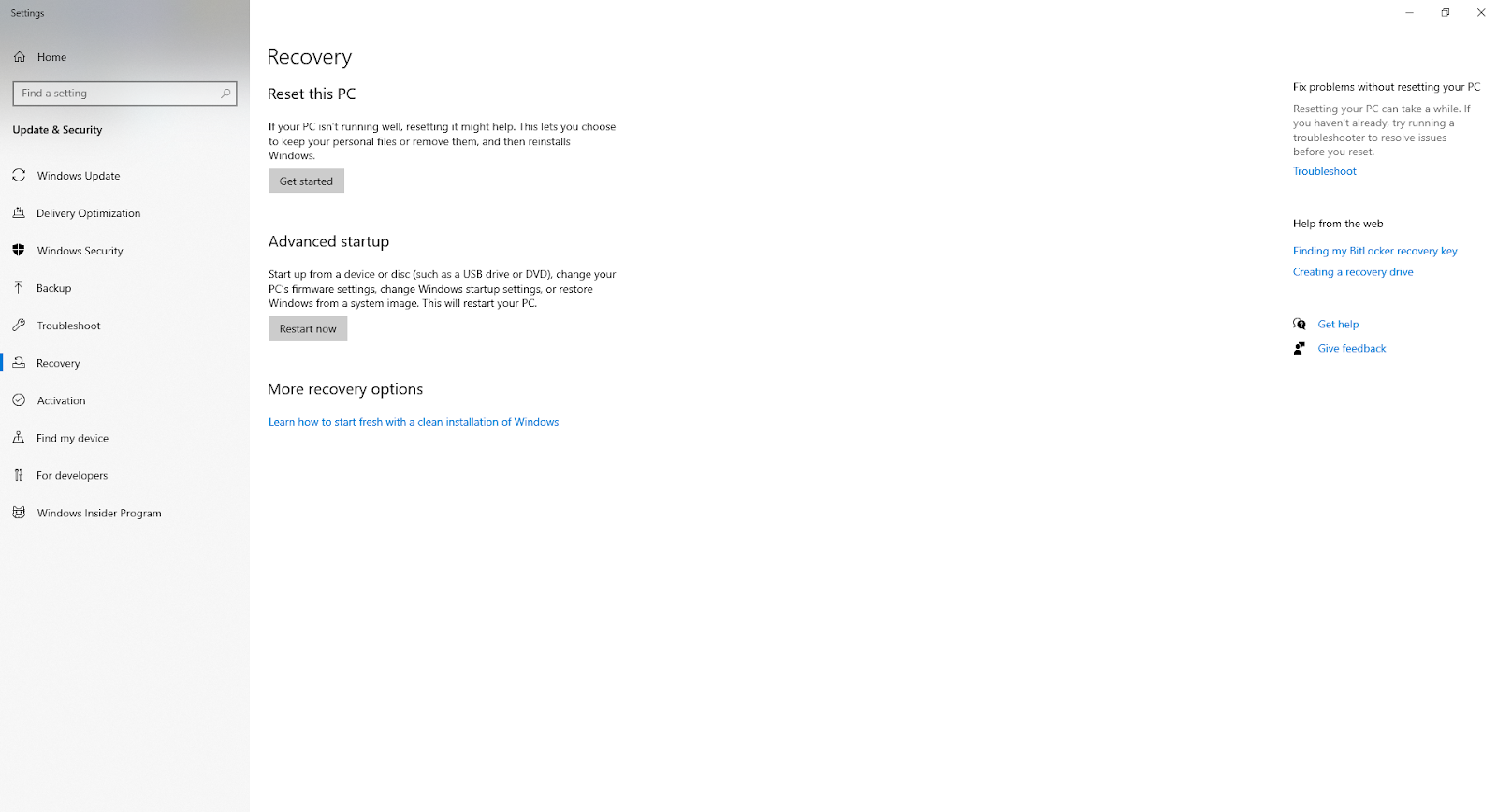
That’ll delete everything – from the adware program to all your files.
Mac Adware
If you’re a Mac fan, you’re in for some good news. When it comes to macOS, most – if not all Mac adware – target the browser with little impact on the operating system. That means it’s pretty easy to remove adware.
You can use any antivirus software to flag and quarantine any threats. You can also manually delete any suspicious files with the following steps.
- Open a Finder window
- Go to Applications
- Look for anything unusual that you don’t remember installing
- Google any file names that look weird to check their ID
- Delete all files flagged as adware
Mobile Adware
Adware is, by far, the biggest threat for mobile devices, accounting for 72% of all reported mobile malware incidents.
Many apps come with embedded adware. They’re often free gaming, photo, or lifestyle apps that appear normal at first glance. They’ll start spamming you with ads like most free mobile apps do. Mobile adware can take it a step further and bombard you with pop-ups even outside the app. That way, it gets hard for you to tell where the ads are coming from.
People don’t commonly install antivirus apps on their phones, so you might want to take care of that ASAP.
Sometimes, you can find the adware files in your phone’s download directories. The exact location depends on your phone’s manufacturer. Here are some examples of what you should look for:
-
-
-
-
- com.ngocph.masterfree
- com.mghstudio.ringtonemaker
- com.hunghh.instadownloader
- com.chungit.tank1990
- com.video.downloadmasterfree
- com.massapp.instadownloader
- com.chungit.tankbattle
- com.chungit.basketball
- com.applecat.worldchampion2018
- org.minigamehouse.photoalbum
- com.mngh.tuanvn.fbvideodownloader
- com.v2social.socialdownloader
- com.hikeforig.hashtag
- com.chungit.heroesjump
- com.mp4.video.downloader
- com.videotomp4.downloader
- Boxs.puzzles.Puzzlebox
-
-
-
If you find one of these files, delete it immediately. That should get rid of the adware infection, but if you keep seeing ads pop up out of the blue, your best bet is to reset your phone to factory settings. Again, make sure you backup all your important data first.
After going through the hassle of finding and deleting adware, let’s discuss how you can prevent adware from infecting your devices.
How to Protect Your Devices against Adware – 8 Tips
As with most online threats, practicing good cyber hygiene is the best adware protection. If you’re not sure where to start, here are 8 tips to keep adware at bay.
- Use a VPN like CyberGhost to add another protection layer to all your connections.
- Use an adblocker. That’ll prevent you from accidentally clicking on shady ads.
- Use an antivirus that quickly detects and quarantines any malicious programs.
- Avoid HTTP sites and never download anything when using them.
- Don’t download apps or software from third-party websites.
- Run scans on all email attachments.
- Don’t click on suspicious links you receive through emails or direct messages.
- Update your OS and apps regularly to ensure you get the latest security patches.
The Bottom Line
Adware is still very much a threat today, but it has evolved a lot since the mid 2000’s. The prevalence of ad blockers and App Store or Google Play Store’s regulations of in-app ads made it more difficult to spread adware like Fireball or Gator.
Instead, cybercriminals attach adware to trojans, viruses, and other malware. The reasoning is that you would quickly get your antivirus to catch and quarantine the initial infection, while you’re more likely to ignore the adware running silently in the background.
That’s why you need to take matters into your own hands to protect your devices from malware. Learn 8 tips to stay safe online, how to create a complex password, protect yourself from identity theft, and recognize dangerous malware, like spyware.
Stay safe and secure!
FAQ
Some adware variants act like spyware. Besides monitoring your browser activity and serving you annoying ads, they steal your personal information like your passwords. Since adware monitors your browser activity, cybercriminals can see your username and password when you login. That’s why you need to recognize adware or spyware infections as soon as possible to mitigate the risk.
For everything else, make sure to build an impenetrable password and practice good cyber hygiene to protect your accounts.
Adware is more common than you’d think. Avast’s Threat Lab experts found that adware accounts for 72% of all malware infection on mobile devices, and the cybersecurity firm Malwarebytes ranked adware as the number one threat to consumers in 2018.
As opposed to ransomware which targets businesses and organizations, adware targets individuals, so many incidents go unreported. The fact that Fireball infected more than 250 million PCs could be a conservative estimate.
PUP stands for potentially unwanted program, and PUA for potentially unwanted application. To put it simply, they refer to an app or program installed alongside your desired software. A PUP can be anything from a minor inconvenience, to adware, to actual spyware. Adware, on the other hand, is a type of malware that displays invasive pop-up and banner ads without any real option to disable them.
It’s highly unlikely that you’ll get a virus from YouTube ads. YouTube is usually careful with its advertisers and its algorithm flags any suspicious URL redirects and keywords. Sometimes, cybercriminals get creative and manage to bypass the algorithm even if for a short while. Be wary of ads promising you anything free or illegal, like hacking software, weapons, or game mods. If you come across those, don’t click on them, and make sure to report them to Google: report the ad to Google: https://support.google.com/ads/troubleshooter/4578507?hl=en
Google has a policy that rejects ads ridden with malware or otherwise unwanted content. That said, cybercriminals always try to work around Google’s policy. They use misleading ad content, advertise phone numbers instead of malicious links, or redirect you to a phony website to make it seem like a legitimate business. Pay attention to mismatched logos and typos in the URL to spot a phony Google ad. If you find anything suspicious, don’t download anything and don’t enter any personal details. Instead report the ad to Google: https://support.google.com/ads/troubleshooter/4578507?hl=en



Leave a comment