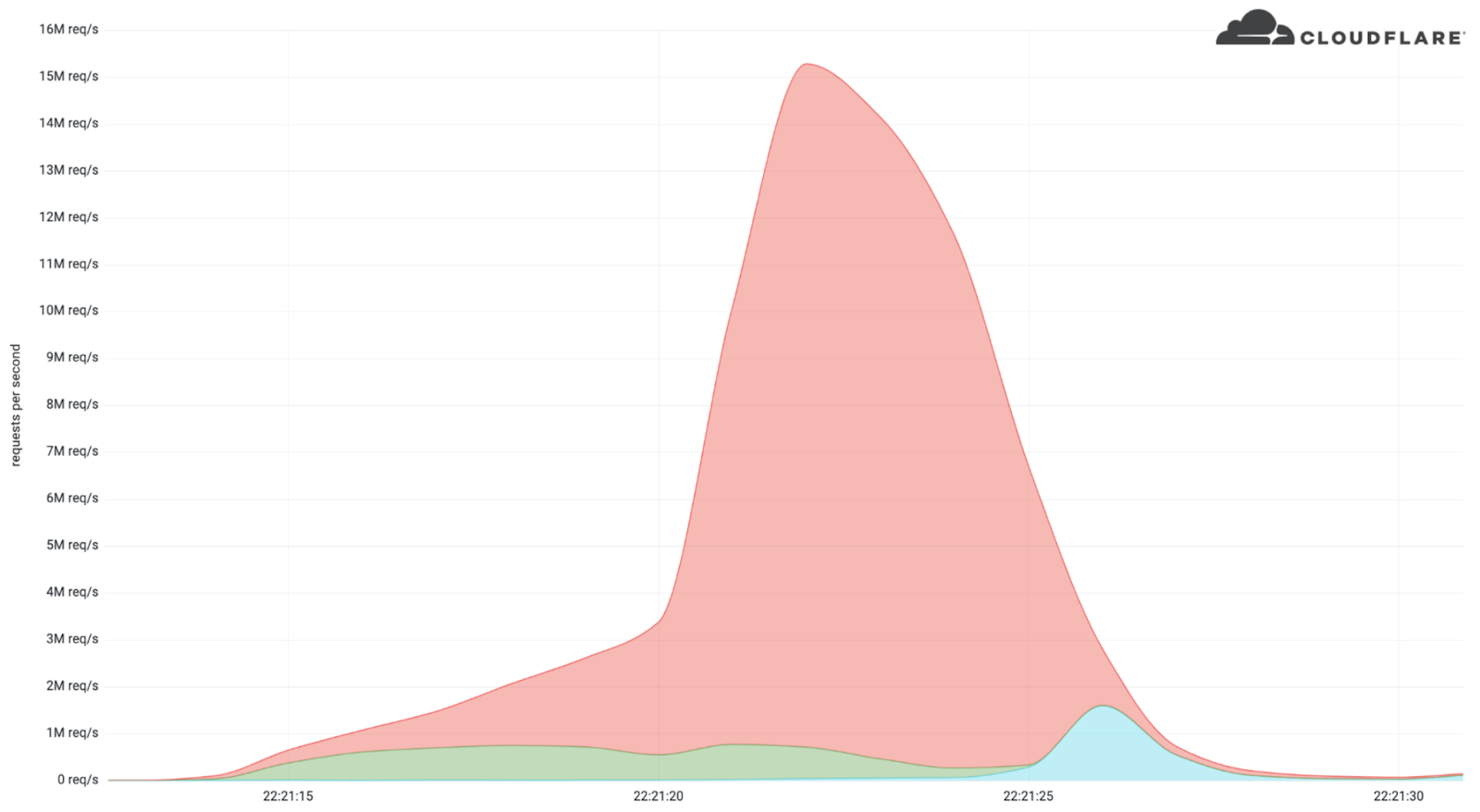
The content delivery network and DDoS mitigation company Cloudflare announced that it managed to successfully disrupt the biggest HTTPS DDoS attack in recorded history. The 15.3 million request-per-second (rps) DDoS attack lasted for 15 seconds and targeted a crypto launchpad in early April 2022.
According to Cloudflare, the attack was launched by a botnet that the company had been keeping tabs on for some time. Apparently, the botnet has launched similar HTTP attacks on other Cloudflare clients before, reaching as much as 10M rps. The reason this attack is so significant — despite Cloudflare’s success at mitigating it — is its use of HTTPS as an attack surface.
Most DDoS attacks target unencrypted HTTP protocols because they’re easier and much cheaper to manage. HTTPS is an encrypted protocol and to carry out an attack of this size requires a lot of computing power. Every request has to go through a secure, TLS encrypted connection that can’t be faked.
Despite Cloudflare being able to mitigate this massive attack, it still spells danger for the future. It’s clear that cybercriminals are steadily becoming bolder and more organized, and that they’re getting backed by serious resources.
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack is a coordinated effort to overwhelm a server or network with the aim to disrupt its services. Attackers manage this by flooding the target with a massive number of requests which slows down the service and prevents people from using it as intended.
To carry out the attack, cybercriminals gather a group of compromised devices and send connection requests from each of those devices. It can be virtually any internet-connected device, from your mobile phone to your smart dishwasher.
That grouping of devices is also known as a botnet. Cybercriminals control them in unison with the help of malware, and owners are usually unaware that their devices are being misused. Most of the time, attackers are able to compromise devices using malware and viruses or by finding unencrypted networks.

The DDoS Menace is Ramping Up
Besides its incredible size, this attack is notable because it mostly originated from data centers instead of residential Internet Service Providers (ISPs). That indicates the attacks didn’t originate from compromised home devices but from cloud computing ISPs.
Some of the data center networks that made up the botnet included the German provider Hetzner Online GmbH and OVH in France. The attackers also used a few home and small office routers. All of that totaled around 6,000 unique bots originating from 1,300+ different networks across 112 countries.
Some of the impacted countries include Indonesia (15% of the attack traffic), followed by Russia (7% of the traffic), Brazil, India, Colombia, and the United States.

Beating Back the Digital Tide
Cloudflare managed to mitigate the DDoS attack using systems that automatically detect traffic spikes and quickly filter out the sources. That was why the attack only lasted for about 15 seconds and didn’t manage to disrupt Cloudflare’s client.
The crypto launchpad that was the target of these attacks remains unnamed and it’s unclear why the botnet chose to target it. Crypto launchpads are used to launch new coins and crypto projects for potential investors.
The story might have ended well for the potential victims here, but it’s indicative of how quickly cyber attacks are evolving. HTTPS-based DDoS attacks are harder to detect and block because the protocol requires security certificates that make these requests seem legitimate. That’s also what makes the attacks more complicated and computing-intensive.
Businesses that don’t use tools to protect themselves face an almost insurmountable threat, but even those that use services like Cloudflare may still be in danger. The service was able to stem the tide this time, but it may not be able to hold the line as the threat continues to grow. Companies can only hope to lessen the impact of similar DDoS attacks in the future through a concerted effort.
Successfully Preventing DDoS Attacks
It’s important to put more protections in place for individual devices, networks, and data centers. Cybercriminals can’t create botnets ranging in the thousands (or more) if they can’t find vulnerable devices to make up their virtual army.
Strong passwords, network firewalls, two-factor authentication, and VPNs can be used to secure devices and networks from malware and viruses.
If you’re ready to keep your devices from becoming part of a future botnet, get CyberGhost VPN and encrypt your network connection. You can install our dedicated apps on up to 7 devices simultaneously or protect your entire home or office by installing CyberGhost VPN on your router.
You may be tempted by a free VPN, but most of them sell your data and some have even been used to create botnets.



Leave a comment
Sharath Blink
Posted on 03/06/2022 at 19:55
It really scares me how the present day malware attacks have become full blown cyber offences. Can’t imagine living in a world so threatening when it comes to cyber security! Thanks for giving so much info in a single blog! In a different piece online, I found that Mazebolt with Cloudfare provides efficient DDoS service protection, really would be helpful if you have an insights on this?
Ghostie
Posted on 06/06/2022 at 15:22
Thanks for taking the time to reply Sharath!
Unfortunately, I’m not very familiar with Mazebolt’s success rate, but Cloudflare has been able to defend very well against the DDoS attacks it has had to deal with so far. While that’s great, it’s still concerning that these attacks keep upping the stakes in terms of complexity and volume. Cybersecurity-oriented companies like Cloudflare have their work cut out for them if they want to keep up!