If you’ve ever watched a spy movie from the last two decades, you must be familiar with the scene where characters take out the battery or turn off their phones to escape police tracking. Whether a hero or a villain, this is the classic maneuver to make sure no one hears, sees, or reads their secrets.
But in real life, police use a sophisticated tool to monitor phones even when turned off. That’s called a Stingray, and until recently, one company was the leading provider of these tracking systems. However, things are about to change since they decided to stop selling directly to law enforcement agencies.
Now a new business is about to take the lead and give a hand in catching bad guys and track your phone as well, even if you’re not under investigation.
Let’s find out more about Stingrays and what’s about to come into play.
Stop Smartphone Surveillance. Don’t let eavesdroppers get ahold of your online traffic. Become a Ghostie and encrypt all your devices. It won’t stop Stingray operations, but it will keep you safe on the internet.
How Stingrays work
Stingrays or cell-site simulators are a powerful phone surveillance tool. They’ve been around since the 1990s, but the public only started to know about them in early 2000.
Initially, Stingrays were designed for military and national security use only. But it all changed when organizations like the Federal Bureau of Investigation (FBI), the Drug Enforcement Administration (DEA), the National Security Administration (NSA), and the Department of Homeland Security started using them on a large scale.
Several UK police forces are known to use Stingrays as well.
Stingrays can catch your International Mobile Subscriber Identity (IMSI). This is the number your phone sends to the network to identify itself to connect. Think of it as a passcode to the network, opening the door to making phone calls, sending text messages, and more.
The IMSI number identifies your phone and you as the paying customer of a cell carrier. Then the cell carrier matches the IMSI number to your name, address, and phone number.
Phones automatically ping their nearest cell tower for service, and this happens even when you’re not using your device for making a call, for example.
A Stingray takes advantage of this setup by simulating a cell tower. Your phone no longer sends a signal to the legitimate cell tower but unknowingly pings the Stingray, so it gives away the IMSI number to a third party.
You might think Stingrays are OK for catching criminals, but here’s the thing.
When used to track a suspect’s cell phone, Stingrays also gather information about the phones of countless people who happen to be nearby. They can also intercept the content of all voice calls and text messages.
Stingrays are not without controversy
The legitimacy of using StingRays has been questioned from the very beginning. The tools were even kept secret at times.
Often, those using Stingrays were not allowed to disclose any information about the technology. Harris Corp., the leading vendors, even had agencies sign non-disclosure agreements. And even though police departments would sometimes find criminals this way, they rejected public records requests about Stingrays.
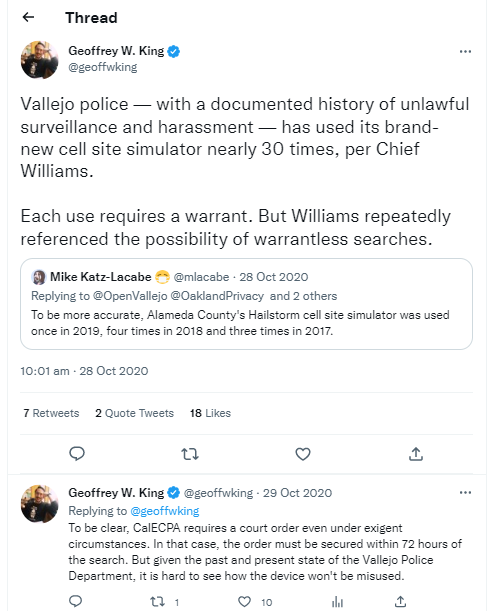
The matter even made it to court, one famous case being the United States v. Rigmaiden. Although guilty, the defendant tried to prove that, in his case, the police used Stingrays without a warrant.
During his incarceration, he spent many years trying to prove he was right.
Rigmaiden didn’t convince the judge that the Stingray’s warrantless use was unconstitutional, but he did win over the public opinion, privacy researchers, and journalists.
In the US, the legal grounds for using Stingrays were established in 2015, when a Maryland Court decided that the authorities need warrants before deploying the surveillance tools. That same year, California passed a law requiring a warrant before police can use a cell-site simulator. The state also required agencies to publish annual public disclosures about these warrants.
All hail the new Stingray provider
In the past, the authorities have mainly one provider for Stingrays: L3Harris Technologies, formerly known as Harris Corporation. But the company will no longer be offering its services to the likes of police departments by the end of 2020.
The reasoning is that 5G networks would make Stingrays obsolete.
So, law enforcement agencies have now turned to a North Carolina company named Tactical Support Equipment to supply new cell-site simulators. They’re the only vendor authorized to distribute Nyxcell hardware, software, and associated training services in the United States.
Octasic is the Canadian firm that manufactures the new Nyxcell V800 Stingray. This model can gather information on smartphones and older GSM devices. What’s more, it can target eight frequency bands, including 2G, 3G, and 4G.
The Nyxcell stimulators seem to include a mobile workstation able to display and render maps that reveal accurate real-time locations of the target cellular device.
So far, reporters and researchers could not find further details of the cell-site simulators’ capabilities, and Octasic refused to comment.
Yet, the question is why law enforcement and police agencies choose this new Stingray provider? Some specialists have indicated that the reason is due to its technological effectiveness.
While that sounds like a standard approach, it could also mean the Stingray is more invasive and puts people’s privacy at a greater risk.
Protecting your privacy is up to you
Usually, you’d have an expectation of privacy when using your devices. But with hackers, providers, and the authorities always looking over your shoulder, that’s no longer the case.
And without proper regulations, it only looks like this situation will continue.
So, it’s time to understand how surveillance alliances work and the political struggles for getting more surveillance back on the menu. Then you’ll be compelled to practice good cyber hygiene and hide your digital footprint with a VPN.
Install CyberGhost VPN and take matters into your own hands. What’s your take on Stingrays? Do you fear them? Do you think the authorities should have a warrant before using them?
Let me know in the comments below.



Leave a comment
Craig
Posted on 10/04/2022 at 10:48
Hi there. I am using a VPN on my mobile in New Zealand, were the police also use Stingrays. I assumed that my VPN would be hiding my location but I am not sure now. Does a VPN hide one’s location?
Ghostie
Posted on 11/04/2022 at 13:07
A VPN hides your location when you go online by masking your IP address, rerouting your DNS requests, and encrypting your online traffic. This helps keep advertisers, government authorities, and cybercriminals away from your private data.
Stingrays use your phone’s International Mobile Subscriber Identity (IMSI), which is given to you by your mobile carrier. It operates even without an internet connection, interacts directly with your SIM card, and can be used to locate you in the event of emergencies by 111 operators.
Ed
Posted on 12/12/2020 at 06:32
I need further information because ive been in front of one of these machines so i need to know how they function in a high detail.
What kind of malware they install and how?
Dana Vioreanu
Posted on 14/12/2020 at 14:22
Hi Ed!
It is hard to say in many details how StingRays work. I don’t believe they install a malware. It is more similar to the way websites would track your online activity, only in a much more invasive way;they basically intercept all your communications, phone conversations, text messages, and very possible, online communication, such as emails or the apps you use. StingRays are advanced tracking tools and since mostly law enforcement is allowed to use them, the rest of us don’t have the knowledge of their exact operation techniques. Even now StingRays usage and procedure it is usually kept secret. So, we can only answer partly to your question because few people know exactly how they stand.
Jeff
Posted on 06/12/2020 at 06:53
The inferred remark at the end of this article is that VPN can hide a phone from Stingray, this is wrong and I think you would know that. There is no software which can hide your phone from the carrier’s phone connection only it’s internet functionality.
Dana Vioreanu
Posted on 07/12/2020 at 09:22
Hi Jeff!
This is the general advice we give to our users, because a VPN helps you keep your online data private. It is true that no privacy tool is 100% foolproof. However, it makes it harder for anyone who uses StingRays or other similar tools with the intention to hack your data – to capture your information and put all of the puzzle pieces together in order to identify who you are and what you do. Remember that a VPN spoofs your IP address and you can change your location. That certainly helps.
pedpeds
Posted on 04/12/2020 at 23:00
would you know which countries Stingray has been sold to?
Dana Vioreanu
Posted on 07/12/2020 at 09:14
Hi there!
From what it was revealed so far, law enforcement and police in the US and the UK use StingRays. Other than that, we don’t know where else they are used.
Ginger
Posted on 02/12/2020 at 06:24
We should have more rights to privacy. Being woke is not enough to protect ourselves in these times.
Dana Vioreanu
Posted on 02/12/2020 at 12:28
Hi Ginger! I couldn’t agree more. Unfortunately, most times, achieving these rights can be very difficult. Becoming aware of the many methods our privacy is infringed is the first step. Our goal with Privacy Hub is to inform more people about these things. CyberGhost VPN provides a solution to achieve online privacy. But of course, overall, organizations and governments worldwide should propose solutions, services and laws that would give people more rights. Given the current times, not sure if that is about to happen soon but let’s hope we’ll get to live it at one point!