We talked with Lila Kee, CPO (Chief Product Officer) at GlobalSign about the confidentiality and integrity of digital authentication, digital signatures, and email communications.
1. Present your company and the services you offer in a few words.
We’re an identity provider, take the technology out of the equation. In the end, we’re trying to replicate on the network and the internet to make sure there’s trusted communication. Just like you have trusted communication when you go to a restaurant and have to show your ID, let’s say to show you’re old enough to have a cocktail, the same thing is with identities and credentials from a trusted third party.
Ever since we’ve seen all the value that can transpire over the internet, there was obviously a need to make sure that we could authenticate the endpoints. I say endpoints because this could be a web server, a person, an IoT device, or even a document.

We see more and more things go into the cloud and more e-commerce is happening. A certificate authority like GlobalSign needs to step in as a trusted third party, so those two endpoints that are having a session would both feel confident that their identity is known and oftentimes, that the transaction is confidential.
People don’t only want to make sure that they’re going to the real Amazon website and not an Amazon masqueraded website; they also want to know that when they’re putting in their credit card to purchase an item, that transaction process is encrypted. So, it’s mainly about confidentiality, authentication, and data integrity. These would be the three main and crucial pillars.
For example, if you’re exchanging a document, and you’re asking for an NDA (non-disclosure agreement) from your supplier, if they digitally sign that document, they can see it’s:
a) from the party that they thought it would be
b) no single element was changed in that document.
If there was litigation or a conflict that needed to be resolved, you can feel confident that the document was unaltered, and those were the terms.
To conclude, we offer a suite of services, ranging from traditional certificate products, whether they’re SSL, including DV (domain validation), OV (organization validation) and EV (Extended Validation) – as well as client certificates issued to users and devices such as mobile phones, desktops, and laptops. Today, we see more and more use cases where zero-trust is in the center. You want to make sure every endpoint in that enterprise or that comes into the enterprise from outside the network is trusted.
Having a digital certificate to authenticate those endpoints strongly is starting to be a real trend with zero-trust models.
With COVID and more remote work, more B2B and B2C transactions going on and everything is tucked inside the protective perimeter, it’s becoming more and more important to have a digital ID. And it’s not just for the servers, but for users too – it’s a mutual exchange of IDs.
There’s a whole portfolio of certificate services, but we’re also gravitating into more cloud services because, as we all know, that’s where things are going. People don’t want to fumble with keys and hardware security modules.
They don’t want the hardware management or deal with SLAs, etc. So, one of our biggest cloud solutions is Digital Signing Service. We have two products, one is called GMO Sign that is a document workflow, where you can exchange documents securely, but with our Digital Signing Service, you can apply digital signatures that meet most regulations around digital signatures including eIDAS (European regulation for standardizing digital IDs and signatures), to make it a legally admissible solution.

2. To what extent are casual users aware of, pay attention to trust marks such as GlobalSign Secure Site Seal and others?
With SSL, the padlock and all those symbols that used to be the element that people would focus on and say: ‘yes, I can trust this’, are now in the background or have gone away. Browsers are now insisting on SSL everywhere, so if you don’t have an SSL certificate on your website, you’re going to get a pop-up that tells you you’re not in a safe browsing environment.
If you’re the website holder, that’s not good for you because I would exit on that session as soon as I see that pop-up.
Now, browsers are taking more of a front stage when it comes to casual users’ indicators whether this is a safe browsing situation or not. The padlock may be less important as you’ll have no idea if an SSL certificate secures it. But if it’s not secured, it’s going to be a terrible experience and one that you’ll probably run away from.
When it comes to Site Seal, they can be extremely powerful, although the impact varies by region. For instance, we have some customers and partners in Latin America, and they tell us their end users have great confidence when they see a Site Seal as part of their browsing experience. In other regions, this is not necessarily the case. Still, the Site Seal might have a new life because many customers are looking for that visual cue.
For instance, many might feel more comfortable putting their credit card into a website with a Site Seal providing higher assurances that you’re interacting with a reputable site.
3. Name types of online threats that Global Sign certificates help as a form of protection, security shield, etc.
It’s a common use case, but traditional SSL, at the end of the day, wards off a MiTM (Man-in-the- Middle) attack.
You put your credit card into a website that you think it’s Walmart, but in reality, it’s not the actual Walmart website because it doesn’t have the digital certificate that’s authenticated from a third party. So, you could easily face a MiTM attack that could intercept your credit card or lead to identity theft. It’s pretty obvious, but that’s the biggest product line that GlobalSign has, offering the biggest area protection.
When it comes to documents, we already saw the acceleration of digitization of documents; but COVID just added a whole new level of self-management, where everybody is remote, but they still have a lot of paperwork, whether it’s internal or external, that needs to have signatures, either due to policies or for regulations.
The nice thing is that we have digital signature legislation. Now, people feel a lot more comfortable exchanging contracts online through digital versions, because they know there’s a legal foundation that they could use to support it or challenge it if it’s the case.
With the GlobalSign Digital Signing Service, we’re providing an easy implementation, as we’re no longer asking people to put their keys on USB tokens or hardware security modules. We’re doing all that confusing key management process and all the bits and pieces. To construct a good digital signature and put it into a PDF, you need to get it right and make sure that the whole hierarchy and the chain, the revocation check, the timestamp are there, etc. You want it not to just make it a valid signature for now, but you want it to be long term validated well after the certificate expires.
That’s what GlobalSign does, and that’s one of the biggest protections for users because you want to be able to sign an agreement. It’s faster, it’s more practical, but you also want to feel it has the same legal admissibility as a written signature.
Also, we’ve seen phishing attacks which now have become the prerequisite of ransomware. 90% of ransomware attacks are because somebody got a phishing email. So, we also have in place several secure email solutions that provide email protection using globally trusted digital signatures: the recipient of a digitally signed and/or encrypted email message that used a publicly trusted Secure email certificate (S/MIME) can feel confident that it did come from a trusted identified party, and that’s because we’re a public CA (Certificate Authority).
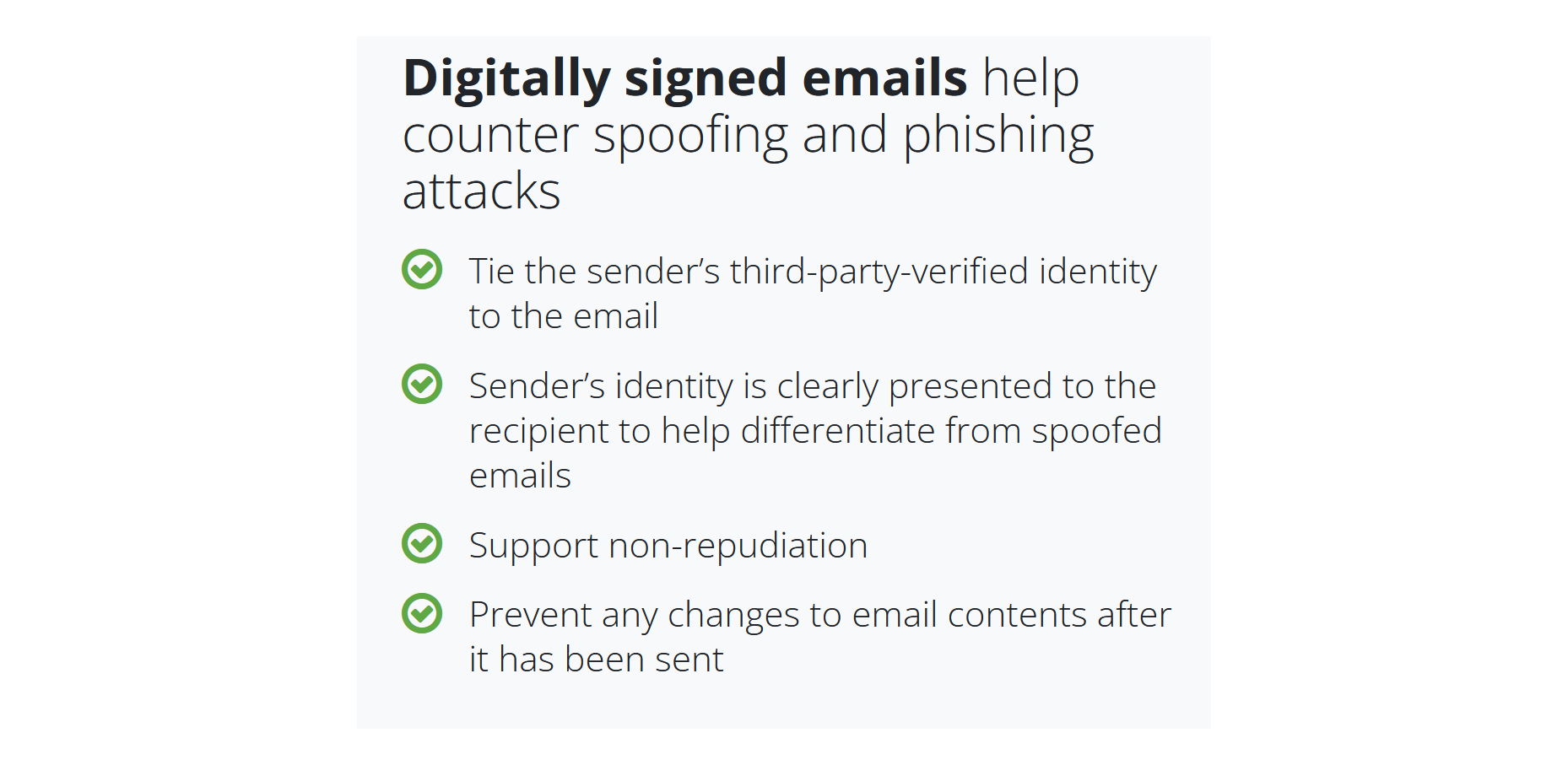
GlobalSign secure email certificates work with all popular email clients, like Google Gmail, Microsoft Outlook, or Apple Safari because our Root certificates are in all major root stores. Suppose we issue a certificate to an end-user who needs to digitally sign their email. In that case, they will render a trust message with a symbol that tells the recipient to feel confident, knowing that a certain email is from who they think it is. They can safely click on the link in the email and not install malware. That is definitely good protection.
If you’re just a small business or an individual, you come to our website, we have a nice GUI, you pick the signage certificate you need, and install it and configure it in your email.
Larger enterprises don’t want to do it that way, though. The main thing now is certificate life-cycle management and automation. If you have over 500 users, you’ll say: ‘I already have these users in Active Directory, I’ve got some of my policies controlled, I want to integrate directly with my CA. So, any new user who gets onboarded will automatically get a certificate signed and installed.’
End-users don’t want to go through that experience; it’s too complicated. They just want it to work, not configure a certificate. That’s another area of protection we offer.
4. What security measures do you enforce to keep certificates invincible?
People go to trusted CAs who run cloud services for many reasons, namely it’s not most organization’s core competency. Further, Google, Apple, Microsoft, and Mozilla will likely continue to keep shortening the certificate validity period. That means they’ll also want those issuing CA’s to be shorter. Those days when you’d have a 30 years or 20 years old issued CA are gone. CAs running cloud services are well equipped to handle these types of changes with minimum disruption.
The longer the keys remain valid, the more vulnerable they are, and the easier they are to be compromised. You may have forgotten to revoke them, or the person who issued them left the company, for instance. So, there’s just the best practices to move to shorter validities. And for not just the end-entity certificate but also the issuing CA. If you are managing your own internal CA, that is a lot to deal with and keep up with.
One of the things that we, GlobalSign, as a CA, do well is to make sure that we’re staying on top of the trend to keep certificate validity shorter; that’s what we do. We know how to turn those CAs around and make them seamless.
It’s important to keep a revocation up to date and make it available for applications to rely on fast, with low latency, without much performance degradation.
5. Name some of the challenges in security certification today and in the future.
I think the challenges are keeping up with the modern-day threats, as there are always new threats. Also, there’s always new regulation that comes up. Our industry self-regulated group, which is called the CA/B Forum, is looking at code signing, and also looking at secure email certificates, and they’re making decisions on the validity or check revocation or how authentication is done. And the biggest challenge is just keeping up with these constant changes.
So, yes, we’re looking at the threat landscape; that always changes. We have our CA best practices, we want to protect the internet, and, of course, we have competition; but we’re all in it together at some level to make sure that we uniformly have a minimum baseline requirement.
Our compliance team always monitors changes and stays on top of everything. But probably the biggest online threat is quantum computing. We’re paying attention to it, and we’re watching it to make sure we meet that challenge. Make no mistake, it’s the biggest looming threat, I think we’re years away from it, but years away will come quickly. We’re definitely paying attention to NIST (US National Institute of Standards and Technology) and other groups that are just marking that threat. We’ll have to figure out how we’ll adjust our crypto processes to deal with them. Yet, our roadmap is prepared to allocate the right resources to address those issues.
6. How do you feel online security and online privacy will evolve in the future?
I think both privacy and security will get stronger and for the right reason. There’s just been a lot of misuse of personal data. I think the penalties will be higher. You see breach after breach, and even these large organizations that should have huge IT departments, and tons of security professionals, still continue to have breaches.
I think the government is losing their patience, and they’ll put some teeth into those regulations. The critical infrastructure is vital in anything, energy or healthcare, you name it because the stakes are too high.
I think we have really good regulation and oversight, but we need to, and I believe we’ll see an increase in government controls in the future.



Leave a comment