In 2021, ransomware attacks seem to be at their peak.
In fact, security experts even warn that we are just starting to enter the darkest era of ransomware. Now more sophisticated and harder to detect, ransomware attacks strike with increased efficiency, shaking up organizations.
Attackers run profitable ransomware-as-a-service schemes, so it’s high time we get familiar with their MO and do some counter defense.
Ransomware is a type of malware, also known as malicious software, that locks down a device and encrypts files with a password. In most cases, ransomware displays a message on the screen demanding payment for your system to work again.
Let’s see how this threat emerged and take a closer look at how a ransomware attack happens.
The evolution of ransomware attacks
The first documented case of ransomware was the 1989 AIDS Trojan, also known as PS Cyborg. The author of the attack was Joseph L. Popp, a Harvard-trained evolutionary biologist trained at Harvard.
Popp sent 20,000 infected diskettes (remember those?) labeled “AIDS Information – Introductory Diskettes” to the World Health Organization’s international AIDS conference participants.
The Trojan encrypted the victim’s files after they had rebooted their computer 90 times. The ransom demand came as an analog note. Victims would have to send $189 to PC Cyborg Corp., a fictitious company, at a post office box in Panama.
Dr. Popp was eventually caught as the British anti-virus industry uncovered his plot.
8 types of ransomware you should know about.
This happened before emails were popular. But, as the internet grew, cybercriminals realized they could level up their ransomware game.
Initially, ransomware targeted personal computers. But it didn’t take long before it rather focused on business users. The reason? Companies will often pay more to unlock critical systems and attempt to protect their reputation.
By the end of 2021, ransomware will hit a business every 11 seconds, with $20 billion in estimated damages.
Nowadays, ransomware schemes mean to mass exploit several organizations at the same time.
Several global high-profile, high-impact ransomware infections in the past, such as WannaCry or NotPetya, left companies’ entire global network in the dark. But those days are now long gone, and threat actors chase ever-increasing ransom pay-outs.
Ransomware deployment techniques
Most often, a ransomware attack spreads through:-
-
- Email attachments
- Messages
- Pop-ups
-
Learning about them will help you protect yourself from ransomware.
Email attachments
A common deceiving method to spread ransomware is to send an infected email attachment, aka a phishing email. Readers get tricked into opening what looks like an important document and help deploy the attack.
Messages
Sometimes, victims receive a message on social media or a messaging app carrying a file or a link. Once opened, ransomware gains access to the network and proceeds to infect other devices.
To make everything more believable, attackers could even create accounts that mimic a user’s current friends list.
Pop-ups
Less used today, this older trick involves pop-ups simulating software the victim often uses.
When the pop-up window shows up, people click on it without knowing it’s ransomware in disguise.
The six stages of a ransomware attack
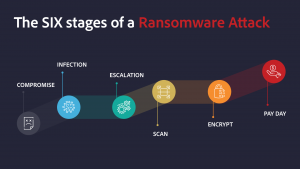
1. The initial compromise
The first stage in the kill chain is distributing installation software to potential victims.
Users are tricked or forced to download and activate malware or payload via an email, an exploit kit, or a drive-by-download. The malware will then kick off the infection.
2. The infection
Once installed, the malware starts downloading a ‘.exe’ or another camouflaged executable. Now the threat copies the malicious executable to a local directory. Once the malicious script ends its task, the malicious payload is executed.
At this stage, cybercriminals establish additional remote access routes to the victim’s environment.
3. Privilege escalation
After they’re inside the victim’s device, attackers use several privilege techniques to gain access to desired files.
The most common methods involve:
-
-
- Moving to new folders, then dissolving them
- Deleting shadow copies of files
- Checking the local configuration, credentials, and registry keys for various rights
- Looking for proxy settings, user privileges, accessibility, and others.
-
The point here is to compromise the device fully.
And to make sure the malicious code stays on the victim’s device, attackers often try to secure additional persistent backdoors or abuse legitimate remote access solutions. They can do so by:
-
-
- Installing internet remote desktop software
- Deleting shadow copies of files
- Getting web shells on internet-facing victim web servers
- Using compromised credentials to abuse remote desktop apps.
-
4. Internal reconnaissance
Now, threat actors perform a full inspection of the victim’s system to maximize the ransomware’s scheme effects, preparing to take files hostage.
Attackers use network scanning and domain enumeration tools to discover:
-
-
- Corporate networks
- Active Directory domains
-
As hackers map out large corporate networks, investigating the scan results can take minutes to hours, depending on the amount of analyzed information.
It is during this scanning stage that security experts have their first real shot at interrupting the ransomware kill chain.
5. File encryption
Before encryption, nothing potentially irreversible has happened. The ransomware simply unpacked itself and infiltrated the system.
But now, cybercriminals are in complete control of the situation. The ransomware begins to encrypt all files it discovered while scanning. Then, it uploads the newly encrypted versions and deletes the originals. The most common method of ransomware deployment is the abuse of corporate group policy and unrestricted file shares.
Attackers move laterally to network segments and systems of interest using stolen credentials and remote execution tools.
The larger the organization is, the more likely security professionals are to stop an infection before the encryption process is complete. That’s thanks to the amount of scanning and encryption taking place before attackers can demand a ransom.
6. Payday

When the encryption is complete, the victim receives instructions on how to recover their data. A common way to do this is to show a ransom note that includes payment instructions, usually in Bitcoins.
Ransomware attacks increased as cryptocurrency payments got more popular.
At this point, hackers wait to receive the ransom.
Some ransomware types are pre-configured to have timeout thresholds where the ransom price increases or the software begins to delete encrypted files.
In case the ransom is paid, victims hope they’ll get a link to download a key or decryption program. But that’s not always the case.
Some attacks install malware on the computer system even after the ransom is paid, and hackers still disclose stolen data.
Tips on how to prevent ransomware
Here are some of the things you can do to make sure you don’t end up getting ransomware or minimize the effects of an attack:
-
-
- Check and double-check every attachment that gets send to you or any suspicious link. Don’t take any chances.
- Keep your operating system patched and up-to-date. This way, you have fewer vulnerabilities attackers can exploit.
- Don’t install unknown software or apps.
- Install antivirus software. Not only can it detect malicious programs like ransomware, but it can also prevent unauthorized apps from launching in the first place.
- Use a VPN. Add a safe layer of encryption to your connection and protect your essential information.
- Enable two-factor authentication (2FA) to prevent unauthorized access to your accounts.
- Always back up your files. This won’t stop a ransomware attack, but the damage caused by one will be much less significant.
-
Have you ever been the target of a ransomware attack? Or what do you do to make sure you don’t end up in such a situation?
Let me know in the comments below.



Leave a comment
lecointre
Posted on 18/03/2021 at 19:10
I read your publication with greatinterest but it shoud be better for me in french if possible
thanks
christian lecointre
Dana Vioreanu
Posted on 19/03/2021 at 08:59
Bonjour Christian!
Thank you for reading and your interest in Privacy Hub.
I recommend an online translation tool, like DeepL: https://www.deepl.com/translator