Exit Node
Exit Node Definition
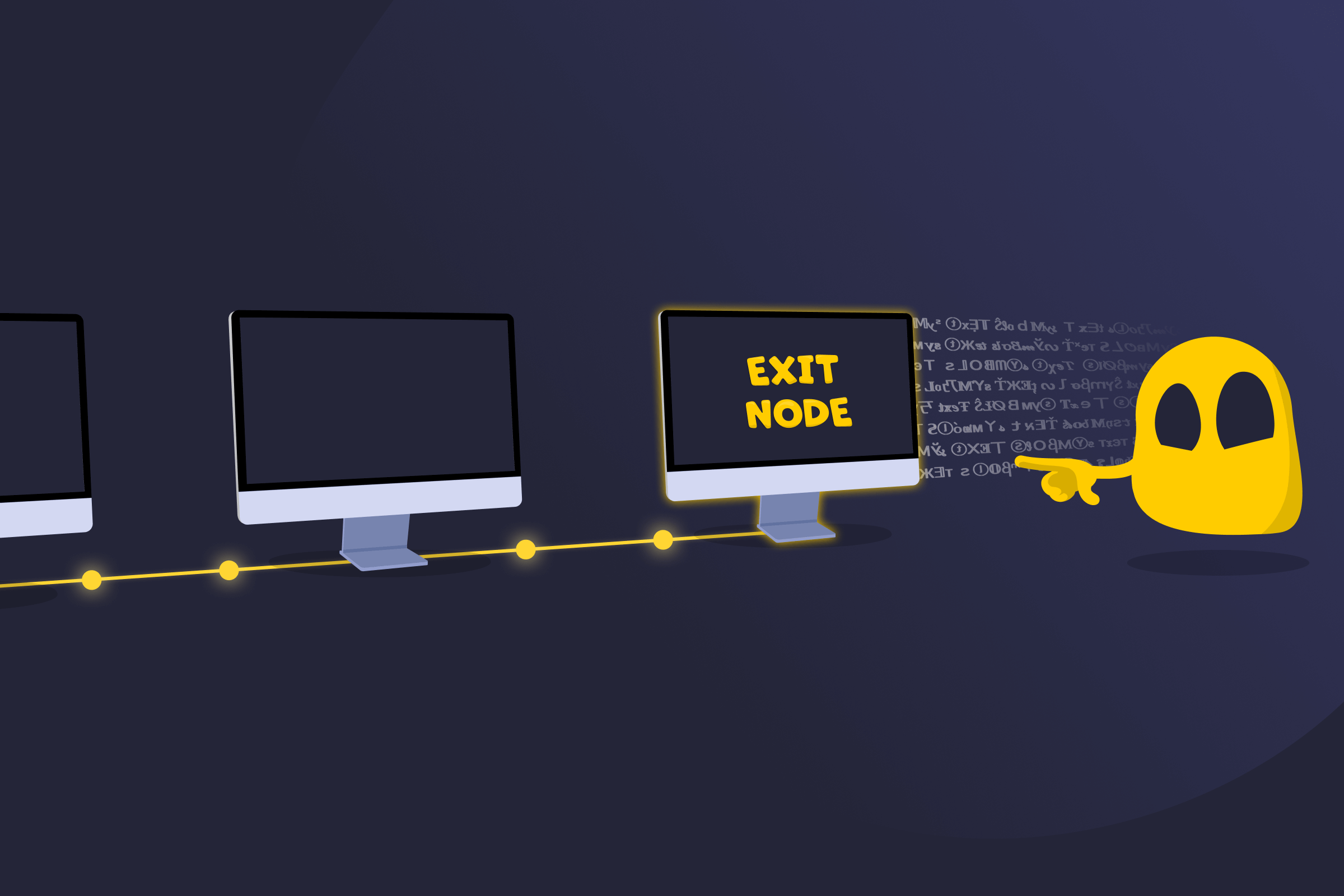
An exit node is a computer or server that helps move traffic from a private or shared network out onto the public internet. It’s most commonly used for Tor or VPN-like systems. The exit node is the final relay or gateway in the chain, where encrypted traffic leaves the private network and connects to regular websites and online services.
Because traffic appears to originate from the exit node’s IP address, it acts as the visible source of the connection. This position creates unique technical and legal responsibilities for the operator.
How an Exit Node Works
In distributed networks, data doesn’t travel directly from a user to a website. Instead, it moves through multiple volunteer-operated nodes to improve privacy and decentralization.
The exit node is the last stop in that path. Once traffic reaches it, the node forwards the request to the public internet so it can reach websites, apps, or online services. To outside services, the connection appears to come from the exit node and not the original user. This separation helps protect user identity, but it also means that any visible activity is associated with the exit node’s IP address.
Tips for Running an Exit Node Safely
Good operational practices help protect both user privacy and the operator.
- Make sure operating an exit node is legal and understand what responsibilities may apply.
- Run the node on dedicated hardware or a virtual server so it is isolated from personal files and daily activity.
- If possible, use an IP that is not tied to personal browsing or a home connection.
- Avoid routing personal internet use through the same IP address that serves as the exit node.
- Inform the internet provider in advance, as some restrict this type of activity.
- Don’t store sensitive data, like login credentials, on the node.
- Clearly identify the system as an exit node so abuse reports can be understood in context.
- If someone complains about traffic, explain that the server relays third-party connections and request proper documentation before responding further.
- Avoid keeping traffic logs to help protect user privacy and reduce the amount of sensitive information tied to the server.
Read More
FAQ
An exit node allows traffic from a private or distributed network to reach the public internet. It acts as the bridge between a private routing system and regular websites or online services.
It can be. Because all public-facing traffic appears to come from the exit node, operators may receive complaints about activity they did not personally generate. The level of risk depends on local laws, ISP policies, and how the node is managed.
Logging traffic can undermine the privacy protections that distributed networks are designed to provide. Many operators avoid storing connection data to protect users and reduce their own liability, though local regulations may vary.

 45-Day Money-Back Guarantee
45-Day Money-Back Guarantee