Rogue Security Software
Rogue Security Software Definition
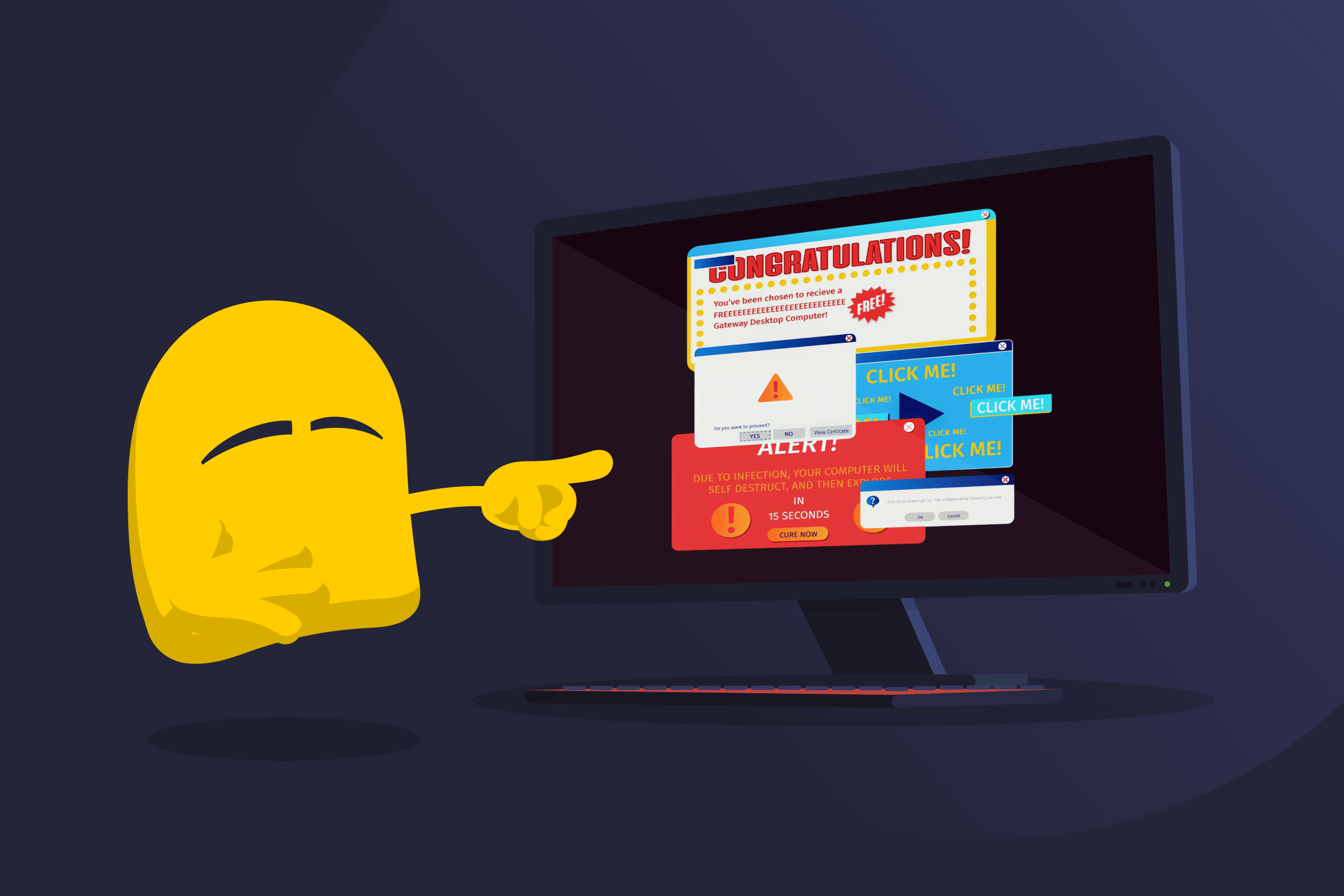
Rogue security software is malware that pretends to be antivirus or security protection. It shows fake scan results and scary warnings to create urgency. It often pressures people into paying for a “removal tool” or clicking prompts that may install more malware. It doesn’t provide real protection.
How Rogue Security Software Works
Rogue security software begins by presenting convincing but false security warnings. These may appear as scans, pop-ups, or notifications that report severe malware infections or system problems, even without an actual scan taking place.
The alerts are designed to create urgency by warning about data loss, system damage, or privacy threats. They often imitate the appearance and language of real antivirus software to appear trustworthy.
When users respond to these warnings, the software prompts them to pay for a fake removal tool or full protection. However, paying doesn’t resolve any issues. The software may continue displaying alerts, interfere with system operations, gather payment details, or install additional malware.
Risks of Rogue Security Software
- Financial loss: Users may lose money by paying for fake security software or services.
- Data theft: Personal, login, or payment information can be collected and misused.
- Additional malware: The software may install more malicious programs on the device.
- System disruption: Normal device performance and functionality can be negatively affected.
- Further cyber threats: Compromised devices may be exposed to more attacks or scams.
How to Stay Safe from Rogue Security Software
- Install security software only from well-known, trusted companies.
- Ignore unexpected pop-ups and warnings that try to rush people into clicking or paying.
- Keep devices and apps up to date to fix security holes scammers rely on.
- Download apps only from official websites or trusted app stores.
- Avoid emails, ads, and websites that claim an infection and push an urgent “clean-up” or “protection” download.
Read More
FAQ
Rogue security software usually gets on a device because someone is tricked into installing it. It often comes from fake security pop-ups, sketchy ads, or download buttons that claim the device is infected. It can also arrive through phishing emails, fake updates, or bundled installers.
Rogue security software is a specific kind of malware. It pretends to be an antivirus and uses fake alerts to push people into paying or handing over information.
Yes. It can be harder to remove if it blocks settings, disables security tools, or keeps showing pop-ups. A trusted antivirus or anti-malware tool is usually the safest way to remove it, and in some cases, you may need a few extra cleanup steps to stop it from returning.

 45-Day Money-Back Guarantee
45-Day Money-Back Guarantee