Popular social media forum Reddit was compromised by an unknown attacker. The malicious actor was able to trick an employee into giving away their credentials through a spear phishing attack. The employee soon realized what was happening and alerted Reddit security, who promptly shut down the attacker’s access to its systems.
Despite this, the attacker was still able to root around in Reddit’s underbelly for a few hours, giving them access to various business systems. For now, the company says no user data has been compromised and that it hasn’t found evidence of any stolen information being sold on the web. It’s still early days though.
The most interesting part of this news, however, might be in what Reddit isn’t explicitly saying: how it managed to be targeted by another social engineering attack in the span of 5 years, despite the lessons it apparently forgot to learn the last time.
Malicious Hackers Stole Some Reddit Documents and Code
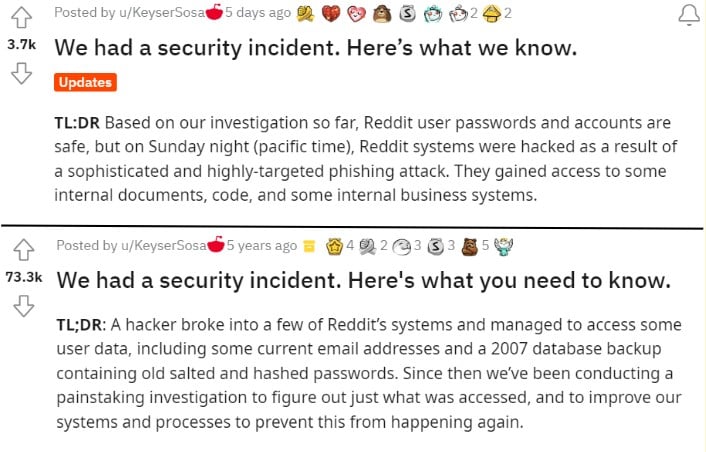
Reddit announced the incident on February 9 in a post on the r/reddit sub, notifying its users about a successful social engineering attack against one of its employees. According to Reddit Chief Technical Officer Chris “KeyserSosa” Slowe, the attackers managed to convince the employee to click on a link in an email which led them to a cloned website of Reddit employees’ intranet gateway.
The announcement mentions the malicious party managed to trick the employee so they could “steal credentials and second-factor tokens”.
After gaining access to Reddit’s employee intranet via the compromised credentials, the cybercriminals quickly combed through Reddit’s systems. Apparently, they were able to get into some of the company’s internal documents, dashboards, and business systems. They were also able to access some of Reddit’s code.
The social media company maintains no user data has been compromised (so far) and that its primary production systems (that run Reddit and store the majority of its data) weren’t accessed. The attackers were able to pilfer limited contact information for hundreds of Reddit employees, though, along with some advertiser information. Reddit says it’s still investigating the incident and has learned some valuable lessons.
That last part is particularly interesting, as Slowe brings up the security incident in 2018 in which it suffered much bigger data losses, including user credentials. Slowe feels the company was successful in learning from its mistakes back then, which has helped mitigate the severity of this attack. This might be true, as evidence suggests attackers have made away with much less (and perhaps less sensitive) information this time around.
Yet, one of the key takeaways from the attack in 2018 was the limitations of two-factor authentication as a proper security measure. This is because two-factor authentication can be circumvented using attack methods like SIM-swapping and social engineering. For this reason, cybersecurity experts now recommend using multi-factor authentication to properly secure accounts, especially business accounts.
What is Multi-Factor Authentication?
Two-factor authentication (2FA) offers an additional security check when you try to log into your account. This often comes in the form of a one-time pin (OTP) sent to your device via SMS, email, or an authenticator app. Security experts don’t recommend this method anymore because cybercriminals have found ways to circumvent authentication, like SIM swapping.
Multi-factor authentication has become the industry standard in the last 5 years, and is also supported by the industry standard known as FIDO (Fast Identity Online). Multi-factor authentication adds a third authentication method (and even a fourth), like a physical piece of hardware which has to be near the device logging in to the account. Or a facial scan or fingerprint authentication.
When Reddit was breached 5 years ago, Slowe mentioned the attackers accessed its systems by intercepting an employee’s SMS OTP. He emphasized the company had learned from this lesson and wouldn’t rely on this 2FA method anymore, hinting at its switch to token-based 2FA. Yet, by that time (and especially in the years since) the cybersecurity industry has switched to supporting multi-factor authentication since it’s much more secure.
It would have made sense, given Reddit’s history of being targeted by sophisticated attacks which bypass 2FA, to make the switch to multi-factor authentication instead. It seems the company didn’t learn its lesson as well as it claimed, or maybe would have hoped.
All things considered, it seems like Reddit managed to not pay dearly for the mistake this time, although the investigation hasn’t completed its findings yet.
Two-Factor Authentication is Still Better Than No Authentication
While having two-factor authentication is still much better than having no authentication at all, experts recommend enabling multiple authentication methods where possible. Many services still don’t offer multiple authentication options, which makes it hard to implement, especially for your personal accounts. Businesses do have options, however, and should ask vendors whether they apply security standards like FIDO before signing up for their services.
Even though multi-factor is a better option, your personal accounts are generally still safe with 2FA. Business accounts are much bigger targets for cybercriminals.
Either way, this incident can serve as not just another important lesson for Reddit’s team, but also for everyone else. You need to keep up with cybersecurity trends and review and then strengthen your security measures regularly. Whether it’s business or your personal accounts.
In addition to enabling multi-factor authentication (or at least 2FA), stay on top of the latest phishing scams, use a good antivirus, and protect your connection with a premium VPN.
CyberGhost VPN routes your internet traffic through a secure tunnel using 256-bit AES encryption, the strongest encryption standard available today. This prevents a variety of cyberattacks and keeps snoopers off your trail.



Leave a comment