We receive legal requests every month. Some come from copyright groups under the DMCA. Others come from police departments and cybercrime units during investigations. They all have the same goal: to connect an IP address to a person.
That connection can’t be made on our network.
CyberGhost runs a private infrastructure built to eliminate identifying records. Servers operate on RAM and reset regularly. IP allocations rotate. We are based in Romania, where there are no mandatory data retention laws. So even when authorities try, there is nothing to extract, correlate, or hand over.
This report breaks down what arrived in Q3 2025, how those requests were categorized, and what it means for online privacy. It also includes bug bounty results and a snapshot of notable security developments from this quarter.
Legal Requests — Our Q3 Numbers
We publish this data every quarter so anyone can see exactly what kind of legal requests we receive and how we handle them. There are two types:
- DMCA complaints: Sent by copyright enforcement groups claiming one of our IP addresses was used to share copyrighted material.
- Police requests: Submitted by law enforcement asking for user data related to an IP tied to an investigation.
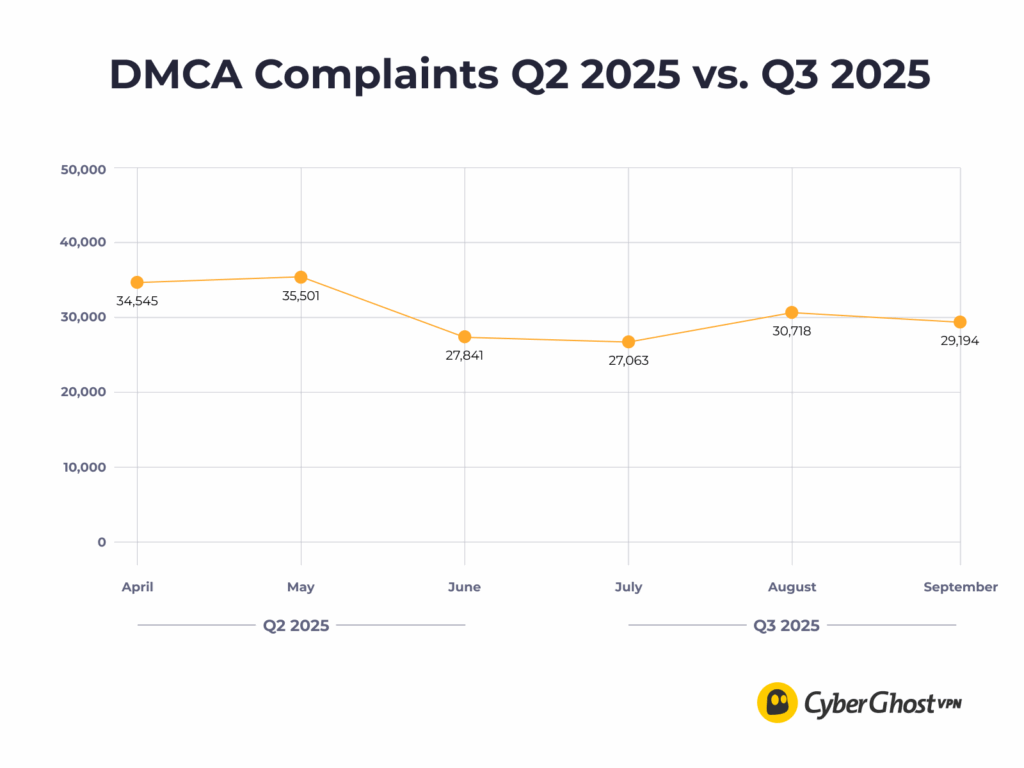
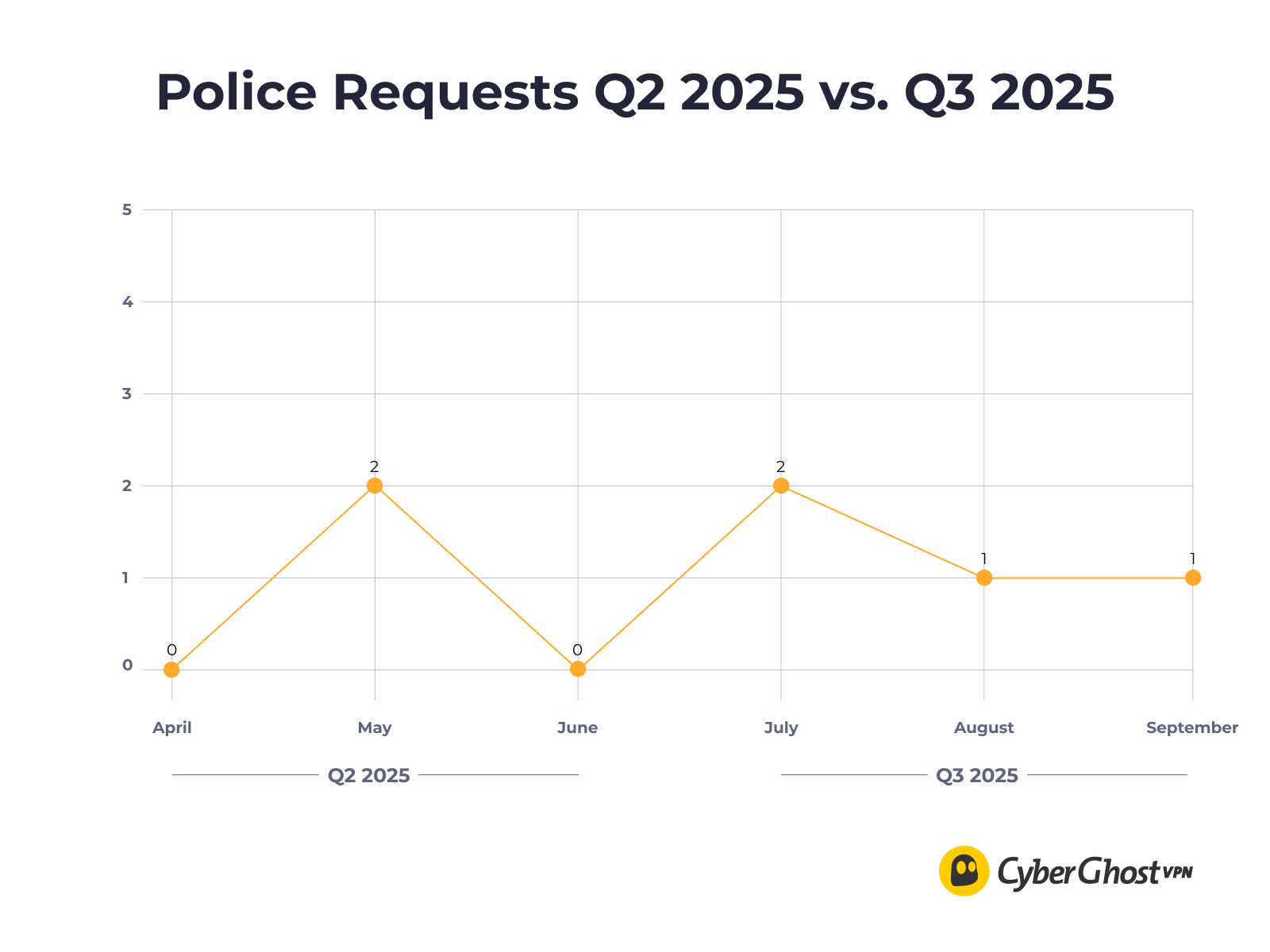
July August September DMCA Complaints 27,063 30,718 29,194 Police Requests 2 1 1 DMCA Complaints
DMCA notices made up the majority of legal requests again this quarter. The total dropped by 11% compared to Q2 (from 97,887 to 86,975). The monthly pattern stayed stable, with volume rising slightly in August before leveling out in September.
These complaints are automated attempts to associate an IP with a person. They go nowhere. Our network design prevents user identification, so there is no technical path between an activity allegation and a human identity. The notices are reviewed, processed, and closed.
Police Requests
Police requests increased slightly from 2 in Q2 to 4 in Q3. These came from law enforcement agencies in different jurisdictions investigating online activity tied to IP addresses in our network. As always, there was no user data to hand over.
Bug Bounty Review — Q3 2025
Security improves through constant testing, which is why our bug bounty program runs all year. In Q3, researchers submitted 60 reports. Eleven described potential new issues, and three of those were verified as real vulnerabilities. The rest were duplicates, out of scope, or informational findings that didn’t represent actual risk.
Metric Number Total submissions 60 Unique findings 11 Valid vulnerabilities 3 Invalid/duplicates/spam/out of scope 57 All three confirmed issues were fixed. None affected user privacy or service integrity. Each report, valid or not, helps us stress-test our assumptions and strengthen the layers that protect our users every day.
What Defined Online Security in Q3 2025
Identity sat at the center of this quarter’s security stories. Verification vendors handled sensitive documents. Mobile carriers remained a single point of failure for account recovery. Cheap AI tooling turned small crews into high-volume operators.
Identity verification under strain
A breach at an age-verification provider used by Discord exposed about 70,000 government ID photos from appeal submissions. The case shows that there’s a clear tradeoff where platforms collect sensitive documents to prove age, then shift the risk to outside vendors. Every extra database becomes another target, and every target attracts specialists who know how to monetize personal records.
SIM-swapping rises across mobile networks
Police in the UK reported a continuing rise in SIM-swap fraud, with national figures doubling across 2023 and 2024 and 2,797 incidents recorded last year. The technique remains brutally effective. Once a number is reassigned, attackers intercept one-time codes, reset passwords, and walk through account recovery flows that were designed for convenience rather than resilience.
AI turns fraud into a subscription
Security teams tracked phishing kits that bundle everything a crew needs: multilingual templates, cloned portals, and scripted lures that plug straight into messaging platforms. Microsoft researchers detailed late-September campaigns using AI-generated code inside SVG attachments to hide payloads, while commercial kits pushed MFA-interception at scale. With AI handling the busywork, small groups can run operations that look like enterprise software releases.

Leave a comment