Clicked on a suspicious link and not sure what to do next? Don’t worry; acting quickly can usually stop a phishing attack from causing any harm. That phishing link might try to send you to a fake website or expose you to malware, but there are some steps you can take to avoid having your personal data or device compromised.
Let’s take a look at what phishing links are, how to spot phishing attempts, and how to protect yourself from them in the future.
What to Do If You Click on a Phishing Link: Step-by-Step
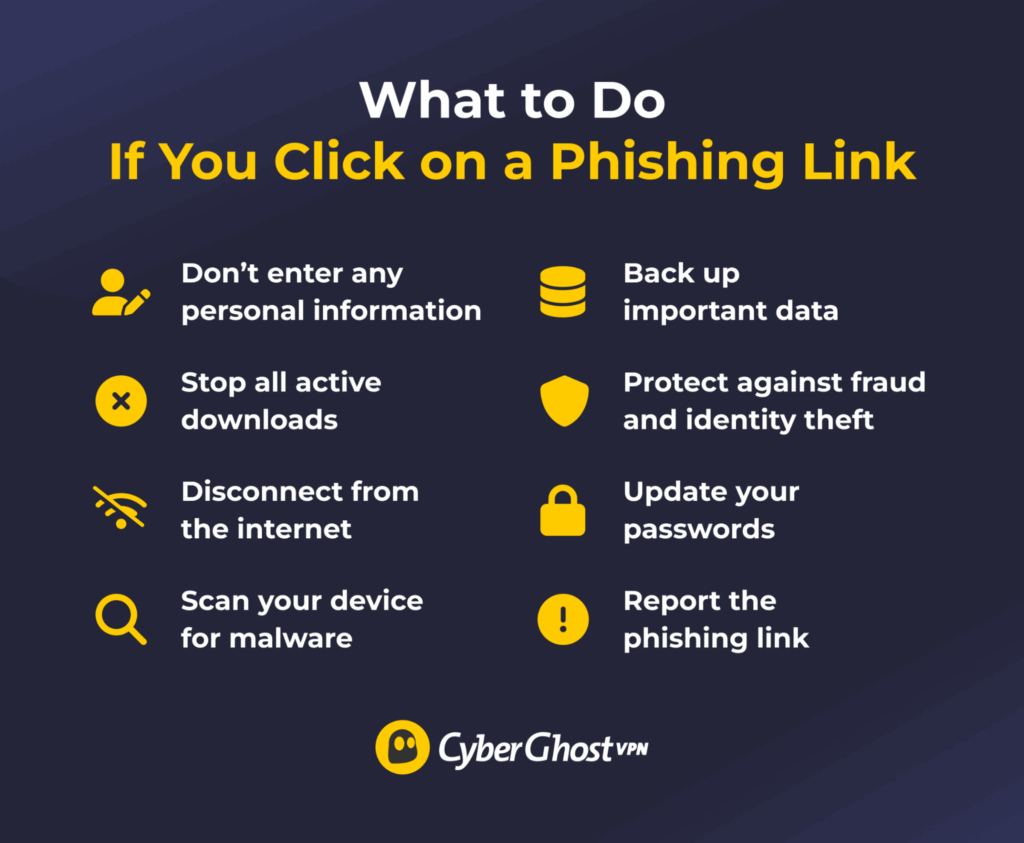
Interacting with a phishing link can be dangerous, but there are immediate steps you can take to protect your data and device. Here’s a complete checklist of what to do if you’re worried you clicked on a phishing link, even if you closed it immediately.
Don’t Enter Any Personal Information
Phishing links can redirect you to a fake website, app store, or messaging app that asks for your personal data. For example, the phishing site might resemble your bank’s login page and ask for your password. Avoid entering any information, because cybercriminals could log what you type in and use it to access your accounts.
You also shouldn’t interact with anything on the page, like buttons, other links, or cookie banners. Clicking on them could trigger a malware download that might infect your device. Instead, leave the website and close your browser window.
Stop Any Active Downloads
Clicking on a phishing link could start a malware download, so check your browser’s downloads window to see if anything is being added to your device. If you spot a download in progress, stop it immediately.
You should also check your device’s downloads folder. If you see any recent unfamiliar files, they might be malicious. Don’t try to delete or move them because it could trigger the malware to activate. Instead, use an antivirus program to run a malware scan and safely remove the files.
Disconnect from the Internet
If any malware has been downloaded, disabling your internet connection prevents the program from transmitting your data back to the attacker. It also protects against malicious remote access to your device. If you’re on a laptop or mobile, turn off its Wi-Fi or mobile data. Switching to Airplane Mode is also a good precaution because it disables all wireless channels at once.
If you’re using a wired connection, unplug the cable. That’s more effective than disabling internet access via your settings, because advanced malware can sometimes interfere and turn internet access back on.
Scan Your Device for Malware
Once you’re offline, use an antivirus program to scan, quarantine, and remove any malicious files. Most operating systems offer basic built-in antivirus tools, but you can also use a reliable third-party antivirus for extra peace of mind. If your antivirus only runs a quick scan, make sure to run a full scan, too. That’s because a quick scan checks processes, memory, and certain folders, but a full scan checks your entire computer for malware, including its system files. Keep real-time protection enabled to continuously scan for and warn you about threats, including suspicious links.
Bear in mind that, while there are antivirus apps for Windows, macOS, and Android, they don’t work in the same way on iOS. That’s because Apple isolates apps from one another (a feature called “sandboxing”). This is designed to prevent malware from spreading, but it also stops antivirus apps from running malware scans on your iPhone or iPad.
If you clicked on a phishing link on an iPhone, you should automatically be protected against malware downloads because iOS blocks unauthorized installations. However, if you were redirected to a site or app and entered any credentials, you still need to change your passwords and secure your accounts.
Back Up Important Files
Once you’re sure your device is malware-free, back up your data. This preserves important files and helps you restore them if another malware attack happens in the future. Use an external storage device, like a USB stick, so the backup stays isolated. If there’s another malware infection, it won’t reach the saved files.
Prevent Fraud and Identity Theft
If a phishing link tricked you into entering personal or financial information, the attacker could assume your identity and take out credit in your name. To prevent this, cancel your credit card and place a fraud alert or a freeze on your credit report with your local credit bureau, like Experian, Equifax, or TransUnion in the US or UK. In addition, contact your bank or any other relevant organizations, and inform them that your personal information has been stolen.
Change Your Passwords
Your accounts might still be at risk even if you clicked a phishing link and didn’t type in anything. Interacting with a malicious link could trigger a spyware infection that might compromise your logins. Start with passwords for the most at-risk accounts, like your email, bank, and social media.
Make sure to create a strong password that’s different for each account. Ideally, you should also update your passwords on a different device, not the one that might have been compromised. This is just a precaution in case malware is still being used to track what you do on that device.
Report the Phishing Link
Once you secure your data and device, report the phishing attempt. If you received the phishing link via email or social media, report the message as spam and block the sender. You can also report a malicious or phishing page to Google or report the attack to the relevant authorities:
What Can Happen If You Click on a Phishing Link?
Clicking on a phishing link exposes you to different threats that can compromise your device and personal data. The risks you might face include:
-
- Spoofed websites: A phishing link might take you to a fake copy of a legitimate website or online service. If you type anything on the page (like your password for the service the fake site is mimicking), the attacker could record and steal that information.
- Malware infections: Interacting with a phishing link can trigger a drive-by download that infects your device with malware. Modern browsers and operating systems usually warn you before installing unknown software, but malware can disguise itself as a legitimate download. If it gets onto your device, it can steal personal data, allow remote access, silently monitor your activities, or lock access to important files until you pay a ransom.
- Session hijacking: Clicking on a phishing link can allow malicious hackers to steal session cookies (small pieces of data that sites use to identify you). Attackers can use these stolen cookies to impersonate you and access your accounts, even if they don’t know your passwords.
- Compromised networks: If your network has any security vulnerabilities, some types of malware can spread from one device across your entire home network, compromising other connected devices.
How to Recognize Phishing Links

Some malicious links are easy to spot, while others look convincing and are packaged with trustworthy emails or messages. The most common signs of a phishing attempt are:
-
- Sense of urgency: Scammers often use urgent phrases to make you impulsively click phishing links. They might use phrases like “immediate action,” “account closure,” “unsuccessful payment,” “wanted for questioning,” or “limited-time offer.” Always contact the organization the message claims to represent to see if the message is legitimate.
- Incorrect email address: Unknown senders are often associated with phishing emails, but attackers can also impersonate real businesses and institutions. However, their email addresses won’t be an exact match. For example, a scammer who claims to represent CyberGhost VPN may have a random Gmail address. The attacker’s email could also contain spelling errors, like “@cybergh0stvpn.com.”
- Generic greeting: Most services personalize their messages, often with the user’s real name. Scammers usually don’t have that information, so they use generic greetings like “Hello,” “Dear Customer,” or “Dear User.”
- Spelling or grammar errors: Messages from real businesses don’t normally include spelling or grammar errors. Cybercriminals, on the other hand, might not spell-check their phishing messages.
- Suspicious links: Phishing links generally lead to an incorrect website address. For instance, “cyd3rgh0stvpn.com” instead of “cyberghostvpn.com.” A fake site’s address also often starts with “http” instead of “https,” indicating a lack of security. Scammers can even shorten phishing links to hide the actual destination. Instead of a normal-looking link, you might see something like “https://tinyurl.com/yc8e8yc5.”
How to Protect Yourself from Phishing Scams
The following measures should help you stay safe from phishing links:
-
- Take your time: If you receive an urgent message from an unknown sender, take a minute to assess if it’s legitimate. Check if the link looks suspicious, look for poor spelling or grammar, and verify the sender’s address.
- Preview the link: Hover your cursor over a link on desktop or long-press the link on mobile to see the actual link destination. You can also use a phishing link checker, which is an online tool that tells you if links are malicious.
- Turn on spam filters: Most email clients and text messaging apps have spam filters that block malicious messages and senders.
- Use an antivirus: Enable your device’s built-in antivirus settings or get a reputable third-party antivirus service. Keep the antivirus program’s real-time protection on, and run a full system scan at least once or twice per month.
- Keep your software updated: This includes your operating system, web browser, security software, and any web-connected apps you use. Software updates usually fix vulnerabilities that cybercriminals could exploit after you click on a phishing link.
- Use an ad-blocker: Use software that stops ads from loading, including malicious ads that could lead to phishing pages. CyberGhost VPN offers a Content Blocker feature that can block phishing links in addition to ads and third-party trackers.
- Enable 2FA or MFA: Two-factor authentication and multi-factor authentication add extra steps to the login process. In addition to your password, you also need to verify your login attempt with an app-generated code, email code, or a biometric scan. This doesn’t directly protect against phishing scams, but it prevents malicious actors from taking over your accounts.
- Use a password manager: This is a security service that stores your logins in an encrypted password vault and lets you generate strong passwords. It also auto-fills login credentials on trusted sites. Spoofed websites don’t trigger an auto-fill, alerting you to a phishing scam.
Bottom Line: Phishing Links Shouldn’t Be Taken Lightly
Interacting with a phishing link is scary because it can put your data and device at risk. But don’t worry, you can take steps to keep your accounts and finances safe using the tips in this guide. By acting quickly, you can shut down phishing threats like malware or fake websites that want to steal your information.
To help prevent scares in the future, it’s a good idea to learn how to identify phishing links and protect your device with cybersecurity apps that can ward off threats in advance. CyberGhost VPN automatically blocks ads, trackers, and malicious links so you don’t have to worry about them. It also masks your real IP address and keeps your online activity private, shielding you from more than just phishing. Better yet, it comes with a money-back guarantee, so you can check out its protective features completely risk-free.
FAQ
What is phishing?
Phishing is a type of cybercrime where attackers target victims with fake messages and emails claiming to be from legitimate businesses or trusted people. The end goal is to trick the victim into sharing sensitive information or interacting with a malicious link or file.
What should I do immediately after clicking on a phishing link?
First, make sure you don’t type anything on the page you’re on. Next, stop any active downloads you see in your browser, disconnect the device from the internet, and run a malware scan. After that, back up any sensitive data on your device and update your passwords for important accounts.
Can simply clicking on a phishing link infect my device?
Yes, interacting with a phishing link can cause a malware infection via a drive-by download. This is when malicious software is automatically downloaded on your device. Modern browsers and devices often protect against drive-by malware, but if it happens, disconnect the device from the internet and run a malware scan.
What if I entered my login or personal information after clicking the link?
Getting hold of your credentials can allow attackers to take over your account for the service they’re spoofing. They could also access other accounts if you use the same password. If you’ve entered login details to a fake site or app, you should update your passwords immediately. If you entered credit card or bank account details, make sure to cancel your credit card and notify your bank about the attack.
Should I change my passwords after clicking a phishing link?
Yes, especially if you entered your login credentials on a spoofed website. In rare cases, phishing links can also allow attackers to hijack your session if you’re logged in to a website. Changing your passwords for important accounts usually ends all current website sessions, which should lock the attacker out of your account.
How do I report a phishing attack or suspicious link?
You can report phishing attacks to your country’s anti-fraud government organization, for example, the FTC in the US or the Canadian Anti-Fraud Center in Canada. You can also report phishing pages and malicious links to Google.
Can phishing links install malware or spyware?
Yes, phishing links can expose your device to malware via automatic downloads that trigger when you land on the page. This could infect your device with spyware or other malware, including ransomware, trojans, adware, stealth viruses, or keyloggers.
Should I scan my device for viruses after clicking a phishing link?
Yes, it’s a good idea in case the link was hiding a virus. Use your device’s built-in antivirus settings or a third-party antivirus to run a scan. Antivirus software can safely remove viruses or malware and repair infected files.
How do I check if my accounts have been compromised?
You might get security alerts from the service provider or emails about password changes. Look for suspicious account activity like missing personal data, messages sent without your consent, or unusual transactions. If you notice any of these signs and still have access to your account, update your password and enable two-factor or multi-factor authentication immediately.
Is it safe to use my device after clicking a phishing link?
Yes, but first you need to take several precautions. Stop any active downloads in your browser, disconnect from the internet, and use an antivirus to scan your device for malware. Once you know your device is malware-free, you should back up your data. You can then reconnect to the internet and start using your device, but make sure to keep your antivirus enabled.
How can I protect myself from phishing attacks in the future?
If you suspect that you’ve received a phishing link, don’t click it. Instead, report the attempt and then delete the phishing message. You should also set up email and text message spam filters and use an antivirus with real-time protection. Enable two-factor or multi-factor authentication on your accounts, and use a password manager to make it even harder for attackers to access your accounts.


Leave a comment