A VPN is a common method for securing remote employees’ access to corporate networks. It encrypts traffic and routes it through a secure tunnel between the user’s device and the VPN server, allowing users to connect securely from home or on the road, which effectively extends the office network’s perimeter.
Corporate networks often rely on apps and services based in the cloud, rather than traditional local data centers. Moving these services to the cloud changes how a corporate network handles access and security. It can also make VPNs less suitable for some environments due to increased latency, gateway bottlenecks, or less precise access control.
In response to these changes, SASE emerged as a framework that combines wide-area networking with a cloud-based suite of security functions. It moves access management and user verification to the cloud rather than using a central control site, as many VPNs do. That said, SASE and VPNs can coexist, as they actually cover different use cases.
SASE vs VPN: Quick Answer
SASE integrates networking and security with cloud-delivered services, zero-trust access controls, and distributed points of presence. It’s typically a good solution for cloud-first enterprises that need better network routing and scalability for a large remote and hybrid workforce.
A VPN creates an encrypted tunnel to enable secure access to the corporate network, but granular/app-level access control usually requires additional controls beyond the tunnel itself. However, VPNs still work for businesses that have fewer remote workers and don’t need to rescale security or access control often.
Many organizations still use both SASE and a VPN. The VPN usually handles secure access to the enterprise network’s gateway, while SASE manages other security functions from the cloud.
What Is SASE?
SASE (Secure Access Service Edge) is a cloud-delivered architecture that securely connects individual users and remote sites to the corporate network’s applications and services. It relies on cloud-based resources and services instead of a centralized enterprise data center. SASE uses distributed points of presence for networking and provides important security functions from the cloud, including:
- Cloud access security broker (CASB): Monitors cloud-based applications and resources and protects against malicious behavior.
- Firewall-as-a-service (FWaaS): Inspects traffic going between the SASE cloud and the rest of the internet.
- Software-defined wide area network (SD-WAN): Optimizes traffic routing across the cloud, private networks, and open networks like public Wi-Fi. This lets users connect efficiently from anywhere.
- Secure web gateway (SWG): Filters internet traffic and protects users from dangers like malware or phishing.
- Zero Trust network access (ZTNA): Verifies user identity continuously and limits access privileges. This makes sure users can’t go beyond their authorization level.
What Is a VPN?
A VPN (Virtual Private Network) acts as a tunnel between a user’s device and a private corporate network, typically at a data center or the company’s headquarters. It creates a secure connection over a public network, such as the internet. VPNs allow remote users to access internal resources, like file servers or various applications, as if they were physically connected to the office network. Similarly, VPNs can connect separate corporate sites or networks on the same site. Typical corporate VPNs are based around these components:
- Tunneling: Establishes a secure tunnel through which the data is transmitted. The VPN uses protocols to define how it handles the data and ensures it gets to the intended destination.
- Encryption: Scrambles data while it travels through the public internet between the user’s device and the VPN server. This helps prevent anyone who intercepts the traffic from reading it.
- Centralized access point: Handles user authentication and traffic routing, often through a central hub located at the company’s data center.
Comparing SASE and VPN
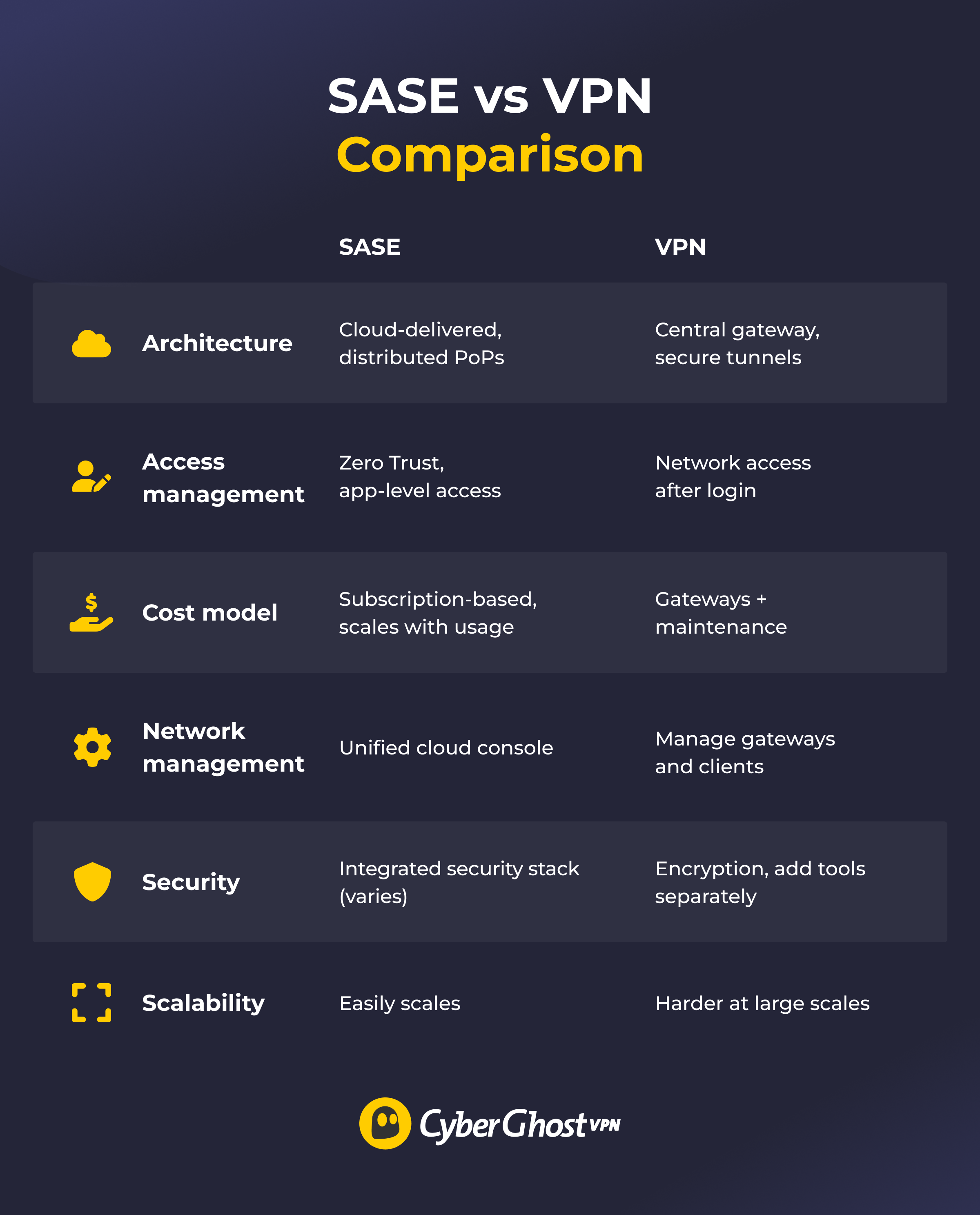
Architecture
A traditional enterprise VPN typically works on a hub-and-spoke architecture, in which the users (the spokes) connect to a central site (the hub) through encrypted tunnels. SASE is a cloud-delivered architecture connecting users directly into a distributed network. It provides services and security functions from the cloud, which reduces reliance on central hub sites, data centers, or colocation facilities.
Access Management
VPN access management usually grants broad network-level access after authenticating a user. This method is simple to implement on its own, so it’s good for organizations where all users need similar network permissions. However, implementing more granular authorization requires additional controls beyond what the VPN tunnel itself provides.
SASE uses a zero-trust model, which continuously verifies users and only grants them the minimum degree of access. This is more complex to implement, but it’s often delivered as a cloud service and ensures users stay at their authorized level.
Cost Model
A VPN’s operational costs are generally related to hardware setup and maintenance. Depending on the network’s scale, setting up a VPN could require an investment for remote sites. SASE expenses are mostly based on subscriptions to the various cloud services. These costs usually scale with the network’s current needs.
Network Management
Managing a VPN requires maintaining and monitoring hardware components, such as the central hub (if there is one) and hardware at other sites if the VPN is used for site-to-site connections. This can make management more difficult if the network spans many separate physical sites or has a lot of users.
SASE often has a unified management platform in the cloud for all network and security functions. It simplifies administration because the IT team can manage the entire network from anywhere through a cloud-based console.
Security
VPNs use encryption to secure data in transit between the user and the corporate network. It provides a secure tunnel for traffic, but it usually doesn’t check the traffic for threats on its own. Other security functions, like threat assessment and malware scanning, typically come from additional controls like firewalls or secure gateways.
SASE applies its security functions through the cloud to traffic inside the network. It can include features like encryption, detecting malicious behavior, protection from malware, and blocking network traffic from potentially harmful online locations.
Scalability
Scaling a traditional enterprise VPN might require physical hardware updates or applying a more complex model, like a dynamic multipoint VPN. Upscaling and managing a VPN can become harder as the number of remote users or connected sites grows.
SASE is highly scalable because it relies on subscription-based services in the cloud more than on updating hardware in physical sites. It can easily accommodate new users or remote sites, so it’s highly adaptable to an organization’s needs.
When to Use Which? SASE and VPN Use Cases
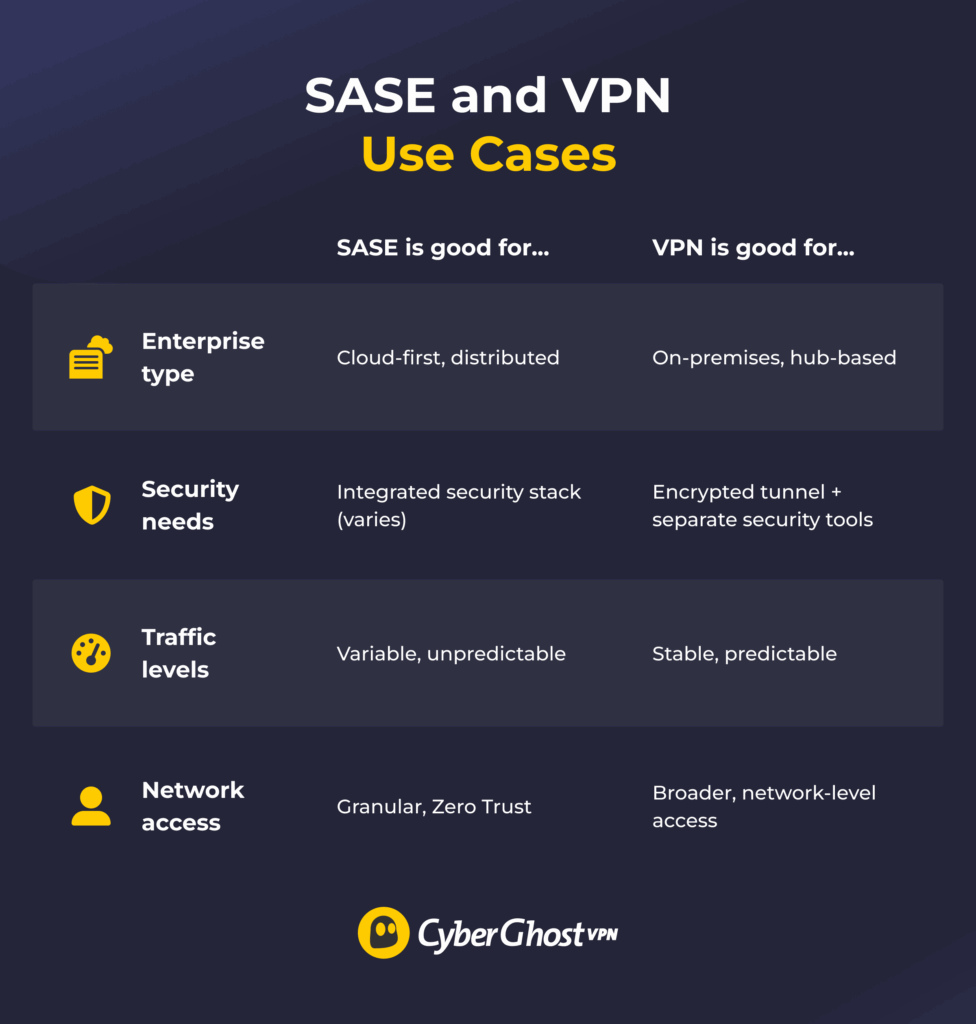
The choice between SASE and a VPN can depend on a lot of factors, such as existing network infrastructure and the number of remote users. A traditional enterprise VPN is typically more suited for organizations that don’t rely on the cloud as much or don’t need the full suite of SASE’s security features. It lets individual users securely access the corporate network, so additional security can be implemented as needed.
SASE is often better suited for cloud-first companies that rely on IaaS platforms and SaaS apps. It can also be a good choice for organizations that need granular, zero-trust access control, such as in compliance-heavy industries like finance or healthcare. It provides fast scaling for companies with a large remote or hybrid workforce.
Will SASE Render VPNs Obsolete?
Enterprises are increasingly switching to SASE for security and access control for corporate networks, which might bring VPNs’ effectiveness into question. SASE is typically a better fit for cloud-first environments and distributed networks because it delivers security and access control from the cloud rather than a central gateway.
On the other hand, corporate VPNs can be a cost-effective way for organizations to secure remote users’ access. They’re typically suitable for networks with a smaller or predictable traffic volume and for enterprises that don’t rely heavily on cloud-delivered services.
While SASE can change how corporations approach security in an increasingly cloud-reliant environment, VPNs still aren’t obsolete. Many organizations use them in combination with SASE, and they can provide a standalone solution for secure access in specific use cases.
SASE vs VPN: Which One Is the Right Choice?
Choosing between SASE and VPN comes down to an organization’s individual needs. SASE is typically suitable for cloud-first businesses with a distributed workforce. It’s a cloud-delivered solution that provides integrated security and zero-trust networking control through distributed points of presence.
Even with SASE’s popularity, VPNs remain a straightforward solution for securing remote access to an on-premises or centralized network. A corporate VPN creates an encrypted tunnel to a server, typically tied to a central gateway. Many enterprises adopt a hybrid approach, using VPNs to support legacy systems through a transition to a cloud-based environment.
FAQ
What is the main difference between SASE and VPN?
The main difference is in their architecture and security scope. A traditional VPN creates a secure tunnel to a corporate network, so remote users can access their organization’s resources. In contrast, SASE is a cloud-delivered framework that integrates networking and security. It connects users directly to corporate services and resources through the cloud, rather than a central server.
Does SASE provide better security than a traditional VPN?
SASE can provide a broader, more granular security model than a VPN because its security features are usually built into the SASE cloud environment itself. On its own, a VPN uses encryption to secure the connection, while other security functions typically have to come from different tools or policies.
How does SASE reduce latency compared to VPNs?
SASE uses a global network of cloud access points to connect users, which can be a more direct and efficient path than a VPN would provide. A VPN might have higher latency because routing traffic often could create a bottleneck at high-traffic points, such as a hub site.
Can businesses use both SASE and VPN together?
Yes, they can. An organization could use SASE for its distributed workforce to secure access to cloud services while maintaining a VPN for a subset of users with simple access requirements or for specific legacy applications. The balance between the two depends on factors like existing infrastructure, cloud reliance, security requirements, and budget.
Is SASE more suitable for remote work than VPN?
It depends on various factors, including the number of remote users or remote sites and the enterprise’s security needs. SASE is generally more suited for distributed or cloud-first corporate networks. VPNs often work better for accessing on-premises or hub-based resources, especially if the network requirements are stable and predictable.


Leave a comment