VPN encryption scrambles your online data as it travels across the internet, making sure no one can read it except you and the recipient. Even if someone were to intercept your connection, all they’d see is a random jumble of letters, numbers, and symbols. This is important for your privacy because it makes it harder for third parties to monitor or track your online activity. Even your ISP and network admins will no longer be able to see details about what you do on the internet, including the websites you visit.
But how exactly does VPN encryption work? What are the different types, and which one should you look out for when you’re choosing a VPN? Let’s take an in-depth look, from a step-by-step guide to the encryption process, to the different encryption methods and protocols available.
CyberGhost VPN secures your internet traffic with the same encryption trusted by banks and governments: AES 256-bit encryption. It’s highly secure and practically impossible to break with today’s technology.
How Does VPN Encryption Work?
When you use the internet, your traffic travels in small units called data packets. These packets contain pieces of the information you’re sending or receiving. Unless encrypted, data packets travel through the internet as plaintext. This means if someone intercepts your traffic, they can see what you’re doing online.
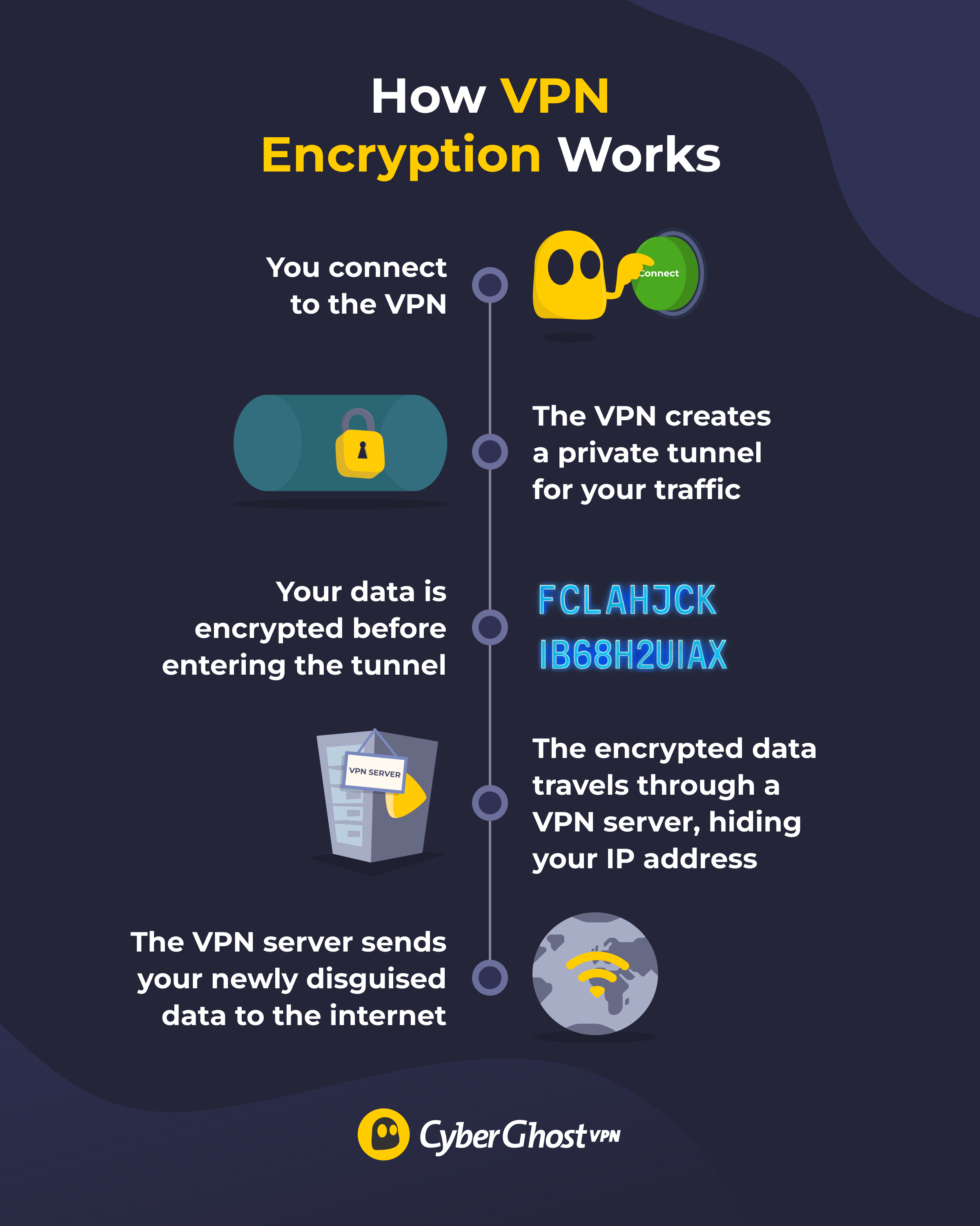
VPN encryption works by creating a secure tunnel for your connection. This is like a hidden highway that your data can use instead of traveling across the public internet. Before it enters the tunnel, your data is also scrambled into unreadable code so it can be safely sent back and forth. Lastly, your whole connection is routed through a private VPN server in a different location, hiding your real IP address behind one from the VPN’s server instead.
Here’s what the VPN does from start to finish:
- Secures the connection: Your VPN app communicates with a private server using a VPN protocol. The protocol decides which encryption cipher (algorithm for scrambling data) to use.
- Creates a shared symmetric key: The server and your VPN app generate a shared symmetric key to lock and unlock data inside the tunnel.
- Encrypts your data before it leaves your device: The VPN app splits your data into packets and scrambles each one using an encryption cipher. This turns readable data into unreadable ciphertext.
- Hides your activity from your ISP: Your encrypted data travels through your ISP’s network, but stays inside the VPN tunnel. Your ISP can see you’re connected to a VPN, but can no longer see which domains you visit.
- Changes your IP address: The VPN swaps your real IP with the VPN server’s, so your traffic looks like it comes from the server instead of your device.
- Decrypts and forwards your data at the server: Your data reaches the VPN server, where it’s decrypted by the shared key and forwarded to the internet.
- Reverses the process for incoming data: Websites you visit send data back, the VPN server encrypts it, and sends it through the tunnel to your device. Your VPN app decrypts it using the same symmetric key.
Symmetric and Asymmetric Encryption
VPNs use both symmetric and asymmetric encryption. First, they set up a secure connection using asymmetric encryption, then switch to symmetric encryption to protect your data as it travels.
Asymmetric Encryption
When your device connects to a VPN server, the VPN app starts a process called a handshake. This is a negotiation about how to secure the connection. Both your device and the server have two keys: a public key and a private key. They swap public keys and combine them with their private keys to create a one-time session key. The session key can lock and unlock data during the connection.
Even if someone intercepted the exchange and got hold of the public keys, they couldn’t recreate the session key without the private keys. Since there are two different keys (public and private), this type of encryption is called asymmetric.
Symmetric Encryption
Once the handshake is finished, symmetric encryption takes over. It uses the shared key created during the handshake to scramble your data before it travels through the VPN tunnel. That way, both your VPN app and the VPN server can encrypt and decrypt the connection for the whole session. Since it uses the same shared key, this type of encryption is called symmetric.
Perfect Forward Secrecy (PFS)
Perfect forward secrecy is an additional security feature that can be added to make encryption even safer. It creates a fresh, temporary key for every session, and sometimes updates it while you’re still connected. Even if someone managed to get one key, which is extremely unlikely, they’d only be able to decrypt a small amount of data, and couldn’t access past sessions.
Different VPN Encryption Types
Not all VPN encryption is the same. The cipher your VPN uses affects the speed and security of your connection. Here are the most common ones you’ll come across.
AES Encryption
Most reputable VPNs use AES (Advanced Encryption Standard). AES is a symmetric block cipher, which means it encrypts data in fixed chunks instead of per bit (the smallest unit of data) or byte (8 bits). This makes encryption efficient because lots of data can be encrypted at once.
AES is also very secure because it uses large keys (usually made up of 128 bits or 256 bits) that are essentially impossible to crack. 128-bit AES encryption can be faster, since the keys are smaller, so encryption and decryption are quicker. However, 256-bit encryption is much more secure. CyberGhost VPN uses 256-bit AES, as do high-security institutions like banks and governments.
Camellia
Camellia is another block cipher like AES. They were developed around the same time, but AES has since become the global standard. Most modern devices have AES support built in, but Camellia can sometimes be more efficient than AES on older systems that don’t have this integration.
ChaCha20 Encryption
ChaCha20 is a stream cipher, which means it encrypts data one byte at a time. This makes it good for activities that need low-latency connections, like streaming or video conferencing. That’s because each byte is encrypted and sent as it arrives, allowing information to travel faster in real-time.
Many trusted VPN providers support ChaCha20 because it’s lightweight, fast, and very secure. WireGuard® uses this cipher, and it works well for mobile devices or other systems with less processing power.
VPN Encryption Protocols
VPN protocols are the rules your VPN follows to secure your connection. They determine how your data is protected and sent. Here are the most common protocols:
- OpenVPN: This widely used protocol is open-source, which makes it both flexible and trustworthy. It uses AES-256 encryption and offers a good balance between speed and security.
- WireGuard®: This newer protocol is built to be lightweight. It only has about 4,000 lines of code (compared to 70,000+ in OpenVPN or 400,000+ in IPsec). It’s super fast, but it isn’t always compatible with older devices.
- IKEv2/IPSec: This stable protocol keeps your connection steady when you switch networks. That makes it a great choice for mobile devices that regularly need to switch between Wi-Fi and cell data.
CyberGhost VPN supports all 3 protocols. You’re covered if you need a secure connection, extra fast speeds, or you want to use the VPN on the go.
Other VPN Protocols
| Protocol | Description |
| L2TP/IPSec | L2TP doesn’t encrypt data on its own, so it’s paired with IPSec for security. It’s safe but slower than newer options and often gets blocked by firewalls. Today, it’s mainly a backup when better protocols aren’t available. |
| SSTP | SSTP supports 256-bit AES encryption, but it’s slower and less efficient than newer protocols. It’s good at bypassing firewalls, though, so it’s often used as a backup for particularly restrictive networks. |
| PPTP | PPTP is an obsolete protocol that’s no longer recommended because it’s considered insecure. |
Why Use a VPN to Encrypt Your Traffic?

1. Avoid ISP tracking: Your ISP can see some details about what you do online, including the sites you access. VPN encryption hides this information inside the VPN’s secure tunnel. Your ISP can see you’re using a VPN, but they can’t see the domain names you visit.
2. Stay safe on public Wi-Fi: Open hotspots are often unsecured, so anyone can join. This makes them vulnerable to cybercriminals, who might try to hijack your connection. If you’re connected to a VPN, the encryption makes sure any potential snoops only see scrambled data instead of sensitive information.
3. Prevent ISP throttling: ISPs sometimes slow down (throttle) your internet connection during data-heavy activities like streaming or throttling to preserve bandwidth. They use a few methods to detect your activity, including checking the site you’re using. VPNs can’t help with every kind of detection, but they can stop your ISP from throttling you whenever you visit a streaming site, for example.
4. Overcoming network blocks: Schools and workplaces may block access to certain websites to promote productivity. Since it sends all your traffic through an encrypted tunnel, a VPN stops local networks from seeing which sites you’re accessing, so they can’t block you.
Encrypt Your Internet Connection
VPN encryption gives you enhanced security and privacy online. It wards off snoops who might try to track and monitor your internet activity, and it adds protection from cybercriminals who might want to steal your data.
That said, you also need to choose a VPN that offers strong encryption and the safest protocols. CyberGhost VPN uses 256-bit AES encryption to secure every connection. It also supports fast, safe protocols, including OpenVPN and WireGuard®. Test it out for yourself risk-free with the 45-day money-back guarantee.
FAQ
How does VPN encryption work?
VPN encryption scrambles data from your device into unreadable code (called ciphertext) before sending it to the internet. Only the VPN server and your device can decrypt it using a shared encryption key. Most VPNs use both asymmetric and symmetric encryption to create a safe pathway for your data to travel.
What is the best encryption for VPN?
AES 256-bit is the strongest VPN encryption available; it uses large encryption keys that can’t be cracked by modern computers. Banks, governments, and top VPN providers use it to protect data.
Can a VPN see encrypted data?
Once your data enters the encrypted tunnel, even the VPN can’t see it. That said, some VPNs (especially free ones) can look at your data before or after it’s encrypted. Always choose a service that follows a strict no-logs policy. This means the VPN won’t track or store data about your online activity, or share it with third parties.
Does a free VPN encrypt data?
Not all VPNs encrypt data. Some free VPNs only use basic or outdated encryption. Disreputable free providers also log your activity and user data to sell for profit. It’s usually safer to choose a premium VPN with strong encryption and a no-logs policy.
How do I check if my VPN is encrypted?
You can use a third-party tool like Wireshark to check that the data packets being sent over your connection are actually encrypted. Also, make sure your VPN supports tested and reliable encryption protocols.
What are VPN encryption protocols?
VPN protocols are sets of rules that determine how your data is secured. While some focus on speed, others prioritize security. Secure protocols include OpenVPN, IKEv2, and WireGuard®.
Are there VPNs without encryption?
Encryption is central to how a VPN works. Some proxies market themselves as VPNs, but if it doesn’t have encryption, it’s not a real VPN. Always check encryption standards before signing up for a service.
Is VPN encryption end-to-end?
Not exactly. VPN encryption protects your data between your device and the VPN server. Once your traffic leaves the VPN server, it’s only as secure as the website or service you connect to. You can check website security by looking for “https” and/or a locked padlock in your browser’s address bar. That means a site is encrypting traffic between its servers and your browser.
Can government agencies break VPN encryption?
In most cases, government agencies can’t break modern VPN encryption. VPNs use powerful encryption methods like AES 256, which is nearly impossible to crack without a key. However, it’s a good idea to check that your VPN has a no-logs policy. That means it doesn’t keep records of what you do while connected, so it can’t be forced to hand over any information about you to authorities.
Does a VPN encrypt your IP?
No, a VPN doesn’t encrypt your IP address. Instead, it replaces your IP address with one from the VPN server you connect to. This hides your real IP and actual location, making it harder to trace your activity back to you.
Can police decrypt a VPN?
No, police can’t decrypt your VPN without a special key, which only your device and the VPN server have. With a court order, they can ask your internet provider to confirm that you connected to a VPN and see that you’re using a VPN, but not what sites you visit.
What is the best VPN encryption?
The best VPN encryption uses AES 256, a strong standard that banks and governments also rely on. CyberGhost VPN uses AES 256, along with best-in-class VPN protocols, to keep your personal information secure.


Leave a comment