Ransomware attacks are on the rise, and you may be letting the cybercriminals in.
This is the gist of a Trojan ransomware note:
Your files are no longer accessible. No one can recover your files without our decryption service. To restore your files, you must purchase our decryption key.
You may be wondering how the attackers got access to your system. The answer is through a backdoor. Leaving the back door to your house open is an invitation to burglars. Leaving your digital back door open leaves you exposed to cyberattacks.
Your network may be vulnerable without your knowledge. If you didn’t change the default credentials on your Wi-Fi router, your digital back door is wide open. Did you change the default password to “password” or “opensesame”? That’s like leaving a key under a flowerpot – everyone checks there.
If you don’t know how backdoors work, you may unintentionally expose yourself to attack in the same way as the Trojans opened their doors for a tempting gift from the Greeks. Unlike the mythological Trojan horse, computer backdoors are very real, and they can go undetected for years.
It’s time to act. Read on to find out what a backdoor is and how you can protect yourself from this type of cyberattack.
What Are Backdoors on a Computer?
A computer backdoor allows an unauthorized user easy, high-level access to an application, network, or device. Cybercriminals can use backdoors to bypass normal security and authentication processes.
Default or weak passwords are one possible gateway for backdoor attacks. Once a cybercriminal has access to your device, they can record your keyboard input, copy sensitive information from your drives, or spy on you using your microphone and webcam.
You may come across 3 types of backdoor attacks:
1. Built-In Backdoors (the Good)
Device manufacturers or software engineers make and use these backdoors during product development. They’re also referred to as proprietary backdoors.
Built-in backdoors allow engineers easy access during the programming and bug-fixing phases. They’re not meant to ship with the final product, but they sometimes slip through.
Cybercriminals may find and abuse built-in backdoors if developers don’t remove them.
2. Trojan Backdoors (the Bad)
A Trojan is a type of malicious software that looks legitimate but can harm your data or network. When you download and run the malware, it creates a backdoor that attackers can use to take over your machine.
Trojans sometimes piggyback on legitimate software from companies you trust. Attackers can also exploit vulnerabilities such as weak passwords to gain direct access to your network and install the malware themselves.
Cybercriminals can use trojan backdoors as a stepping stone to more secure networks, to drain your resources for illegal crypto mining, or as a data-collection tool.
3. Supply Chain Backdoors (the Ugly)
Third parties can intercept devices or programs during their manufacture and insert malicious malware. Wi-Fi routers are a common target since they’re easy to compromise and cybercriminals can use them to access sensitive information.
Unless a cybersecurity expert inspects every new acquisition before it’s deployed, supply chain backdoors can slip through unnoticed. Nobody suspects that brand-new products carry such vulnerabilities.
Supply chain backdoors often attack networks and devices that carry highly sensitive information, making them particularly destructive. A backdoor attack on SolarWinds’ Orion software cost the company over $18 million.
You can’t do much to prevent built-in or supply chain backdoors other than purchasing from major retailers or having a cybersecurity expert check your product.
You can take steps to prevent Trojan backdoors. Let’s find out how they work and what you can do to avoid them.
How Do Trojan Backdoors Work?
Trojan backdoor attacks aim to:
- Bypass all security; and
- Gain root access to a system, i.e., administrator privileges.
Once a cybercriminal has access to your network or devices, they can deploy a series of more complex programs.
They may do this in a series of steps. An attacker uses a low level of access to gain more privileges and repeats the process until they have full access to your systems. This step-by-step approach helps the attacker avoid detection.

Once the backdoor is in place, cybercriminals can watch your every move and hack into your devices. They can take control of your digital life without you suspecting a thing.
Backdoor Attack Examples
Let’s take a closer look at two examples of backdoor attacks.
DarkSide Ransomware
DarkSide’s ransomware caused fuel shortages on the East Coast of the United States when it attacked a major pipeline operator in May 2021. It was one of the most destructive cyberattacks on critical infrastructure.
Cybercriminals from DarkSide used a combination of targeted phishing attacks and exploiting known vulnerabilities in operating systems to deploy their malicious software. The malware infiltrated secure systems via these backdoors, locked users’ computers, and displayed a scam message like the one below.
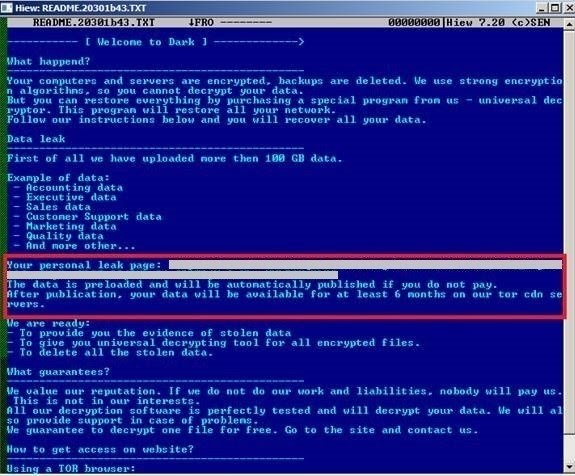
Cybercriminals rely on social engineering to get people to pay up. As well as disrupting Coastal Pipeline’s operations, Darkside threatened to publicly release proprietary information if the company didn’t pay the ransom.
Backdoor attacks from phishing and weak passwords are preventable. If an employee had used strong, unique passwords or if multi-factor authentication had been in place, the attack might never have happened.
NotPetya (Petya Family)
Like DarkSide, NotPetya denied the user access to a machine or network and displayed a ransom message. Users had to pay in cryptocurrency to get a key that unlocked their system.
The NotPetya attack took place in June 2017 and affected more than 80 companies across the US, the UK, Germany, Poland, Italy, Russia, and Ukraine. A White House assessment estimated that NotPetya caused losses exceeding $10 billion.
NotPetya’s creators hid the backdoor in a legitimate update to the Ukrainian accounting software MeDoc. The software developers at MeDoc claimed that the backdoor was delivered as a drive-by download, and they had no idea that their update contained malicious code.
When the victims updated their version of MeDoc, they unintentionally installed the malware. The ransomware quickly spread through dozens of countries and companies. As the backdoor piggybacked on a trusted piece of software, the NotPetya attack was almost impossible to prevent.
Ironically, this version of the Petya malware relied on a Windows exploit (EternalBlue) the NSA developed.
How to Protect Yourself from a Backdoor Attack
If you take one thing from this article, it’s that paying for backdoor attack protection is much cheaper than getting hacked. It’s not just malicious third parties you have to look out for. The NSA keeps tabs on you, and even the FBI is financing backdoors for surveillance purposes.

What can you do to stay safe from backdoor attacks? It’s quite easy:
-
-
-
-
- Don’t buy hardware from shady sources. Ensure everything you buy comes with a manufacturer and seller warranty.
- Don’t rely on the default login credentials. A unique password is the best protection against backdoors and malware. Use multi-factor authentication whenever possible.
- Don’t download files or install software from untrusted sources.
- Don’t access the Internet through unsecured public connections. Get CyberGhost VPN now to encrypt your connection.
- Do keep your antivirus up to date and run regular full system scans.
-
-
-
Hardware companies rarely have full control over their suppliers’ security practices. One weak link in a supply chain can result in a hidden supply chain backdoor. You can patch vulnerabilities by regularly updating the firmware, but not all manufacturers proactively tackle viruses.
Proprietary backdoors are sometimes left open to provide high-level maintenance post-purchase. Less reputable companies may have shadier motives for leaving their products unsecured.
A built-in backdoor is the easiest way for an attacker to get direct access to a secure system or network. Aside from choosing a trustworthy manufacturer, you can’t do much to protect yourself from this type of attack.
How to Detect a Backdoor Trojan
Backdoor malware isn’t always easy to detect. Cybercriminals constantly come up with new techniques to target specific users, as was the case with the NotPetya and DarkSide attacks.
Anti-malware firewalls check files, links, and processes against databases of known threats to protect you from malware. This method is effective but not foolproof.
Other protection methods take things to the next level. CyberGhost’s Security Suite includes Intego’s world-class antivirus software. This uses advanced behavior analysis to spot malware not yet flagged in cybersecurity databases.
Some backdoors can penetrate even the most sophisticated cybersecurity protocols. These backdoors are complex to develop, and they usually target corporate networks and systems.
Cybersecurity experts can manually detect and purge them, but it’s resource intensive.
In a nutshell, cybersecurity teams:
-
-
-
-
- Deploy firewalls.
- Closely monitor all the running processes, communication requests (often monitoring individual ports), and file modifications.
- Locate the malware through an iterative process of discovery and analysis.
-
-
-
On the plus side, detection isn’t a problem with ransomware. When you get a ransom message pop up, you know you’re in trouble.
How to Remove a Backdoor Virus
It’s challenging to detect backdoor trojans, but at least removing them is easy, right? I wish.
Your best bet is to choose an antivirus that has automatic removal tools. CyberGhost VPN has a built-in backdoor detection and removal tool that’s constantly updated.
If you’re dealing with a run-of-the-mill trojan backdoor, you can try to remove it with your antivirus. Here’s how:
- Install the antivirus on the infected machine. If the antivirus was already installed when the machine got infected, choose a different one.
- Check that the application and virus definitions are up to date.
- Disconnect your computer from the internet. Turn off the network adapter and physically disconnect the cable. If you suspect router malware, also turn off the router and/or modem.
- Reboot your computer in safe mode and run a full system scan.
- Reboot your computer and run a second full system scan. Make sure you include any network devices.
- Restore your computer to an earlier date to get rid of any file modifications made by the backdoor program.
- Repeat these steps for all devices using the network. Backdoor viruses have worm-like replicating abilities, so check the entire network before stepping down from red alert.
For more sophisticated backdoors, you need to do a complete system wipe. It’s a safe, affordable solution to ensure all infected files are detected, quarantined, and deleted.
In this situation, don’t use any backups that you’ve stored on your machine.
Even a full system wipe is powerless against supply chain attacks and hardware backdoors. In a best-case scenario, you’ll need to install a version of the firmware that isn’t vulnerable to the backdoor. If that doesn’t work, you’ll have to get rid of the infected hardware.
Fortunately, operating systems have become a lot less vulnerable to backdoors. I can’t remember how many times I had to reinstall Windows XP because one of my friends clicked on the wrong pop-up.
Do you have any personal experience with stubborn trojans? Let me know in the comments below.
FAQ
A backdoor is a hidden way of accessing an application, machine, or network that bypasses regular security measures. They have a legitimate use in software development, but companies should remove them before shipping products.
A Trojan is a malicious piece of software that tricks the user into downloading it by appearing legitimate. Trojans are often disguised as a Word or PDF document, an mp3, or an executable (exe) file. If you’ve ever had a pop-up claim you can download and install more RAM or an email from an unknown address titled “URGENT REQUEST”, you’ve probably come across a Trojan.
Developers create proprietary backdoors during software development. They don’t usually ship with the final product, but mistakes happen. Cybercriminals can take advantage of these backdoors to attack machines and networks.
Malicious third parties, like hackers or cybercriminals (sometimes working on behalf of intelligence agencies) create backdoors to bypass security protocols. They can use backdoors to gather intelligence, take control of systems, or physically damage networks.
Backdoors also occur when people don’t follow best security practices, for example, using a weak password to protect sensitive information or skipping two-factor authentication. Cybercriminals can exploit these unintentional security vulnerabilities to access networks and devices.
Computer backdoors were initially called trapdoors. Today, the term “trapdoor” is linked to trapdoor functions, which are part of the inner workings of encryption algorithms.
A trapdoor function is a mathematical operation that’s easy to perform in one direction but very difficult to compute in reverse unless you have special information (the trapdoor). If the trapdoor function were a padlock, the trapdoor is the key.
“Backdoors” are now associated with covert system access, while “trapdoors” are the stuff of cryptography.
Cybercriminals can install malware using easy-to-break login credentials, phishing attacks, drive-by downloads, keyloggers, trojans, vulnerable networks, or through physical access to the machine itself. Backdoors are one way that cybercriminals can access your devices to install malware.



Leave a comment
Kechia Foregger
Posted on 01/01/2023 at 20:24
Have been a victim of Very Terrible/Very Real Cyberstalking & Stalking for months, possibly, the last 3-4 years. Until today, have been unable to pinpoint a “resolution” or even, to find black and white,written acknowledgement of the crime- much less being able to Explain,Prove, Report… It is 24/7 neverending Torment. Have read your article- seems as if there could be a light at the end of the tunnel. Truly ,not tech savvy-know only that there is definitely audio/video surveillance (pos. Smart TV) It is in my home, at my work, etc… I am not exaggerating, nor unhinged. What would you suggest? Any advice would be Golden, you’ve really touched up on the exact nerve of my problem.
Sincerely, kf
Ghostie
Posted on 14/02/2023 at 18:43
Hi, Kechia,
If you suspect you’re a victim of cyberstalking, you should definitely contact the local authorities. Cyberstalking is a crime under US law, as well as in most jurisdictions across the world.
For US citizens, the National Center for Victims of Crime has a Stalking Resource Center that likely has all the information you’re looking for, including what to do if you believe you’re being stalked at work.
Wishing you all the best and please stay safe!
Jefferson goodrich
Posted on 01/12/2022 at 17:42
I’ve been wiped out completely, my phones all the same, I don’t have no money left, how do I get the hackers out of my life?? Factory reset does no good. Please
Ghostie
Posted on 02/12/2022 at 16:48
Hi, Jefferson
It sounds like you’re experiencing a comprehensive targetted hack. If you can’t shake a virus infection, the only safe choice is to stop using all your current devices until you can get a cybersecurity expert to vet each and every one of them.
Stay safe
Lisa Boehm
Posted on 05/10/2022 at 08:53
My neighbors have access to my Android phone. I even had Norton security installed and it has not stopped. They have way too much personal information on me. I do not interact with any neighbors to know my personal information. Any suggestions.
Vlad Melnic
Posted on 06/10/2022 at 09:25
Hi, Lisa
That sounds like a serious breach of your security. Although a last-resort solution, a full factory reset of your Android phone is the safest way to go. Usually, there are tell-tale signs that your phone is hacked. It would also be really helpful for you to determine how this happened in the first place – whether it was through an app or if your phone’s security was the issue.
Stay safe!
Dume Ekundayo
Posted on 27/01/2022 at 08:21
My laptop is getting hacked by a neighbour and hr has access to all aspects of my device. He can detect whenever I switch on my PC and can see the websites and web pages I’m viewing at any time. I installed CyberGhost VPN and Bitdefender Antivirs. Intego immediately found and quarantined the trojan virus called TR\Patched\Ren.Gen. The neighbour continued to transmit the virus after making small changes to the code. So far Intego has detected 23 versions of this bug but he still able to access by computer and view whatever I’m watching on the internet.
Currently my we-fi on my router is disabled as I only access the internet via the Ethernet cable. This has made no difference.
I d0n’t access my email or other accounts from home as I fear he is recording my keystrokes to steal my passwords. This has happeed in the past when I have been locked out of my email and Ebay accounts. I was changing my email passwords on a weekly basis and had to open a new Ebay account as it was suspended because of suspicious activity.
Vlad Melnic
Posted on 02/02/2022 at 12:25
@Dume Ekundayo, that sounds horrible. I’m sorry you have to deal with that.
I would suggest saving crucial information on a cloud service or on a USB and completely formating all your devices. Some things can only be solved with a clean sweep.
For your router, a factory reset should get rid of most malware. Before resetting it to its default state, make sure you write down any custom settings, like PPoE logins. Once the reset is done, update it to latest firmware to prevent re-infection.
If you happen to do a clean sweep, make sure CyberGhost + Intego are one of the first things you install once the OS is set up. Once they’re installed, connect to the internet so the virus definitions are updated and run a thorough scan.
Hope this helps! All the best,