The last week has been an interesting roller coaster ride in cybersecurity circles thanks to the newbie hacking group, Lapsus$. This new and obscure cybercrime syndicate claims to have hacked four major companies in the last month. That’s incredible, even by Anonymous standards. Three of the companies in question, Nvidia, Samsung, and Ubisoft, have confirmed they suffered data breaches. Vodafone has yet to confirm whether anything has been stolen.
Lapsus$ is launching major attacks, but so far these breaches haven’t severely impacted Nvidia, Samsung, or Ubisoft users. That said, these companies may still have to deal with serious consequences–including a lot of scrambling to manage any fallout that might impact Nvidia, Samsung, and Ubisoft users worldwide.
Who Is Lapsus$?
Many experts speculate the group is based somewhere in South America given their track record of targeting South American companies and Brazil’s Ministry of Health. Until December 2021, Lapsus$ was relatively non-existent in the public sphere. “So far, they appear to be somewhat amateurish, which could indicate that the individuals involved are not experienced cybercriminals,” said Brett Callow, threat analyst at Emsisoft.
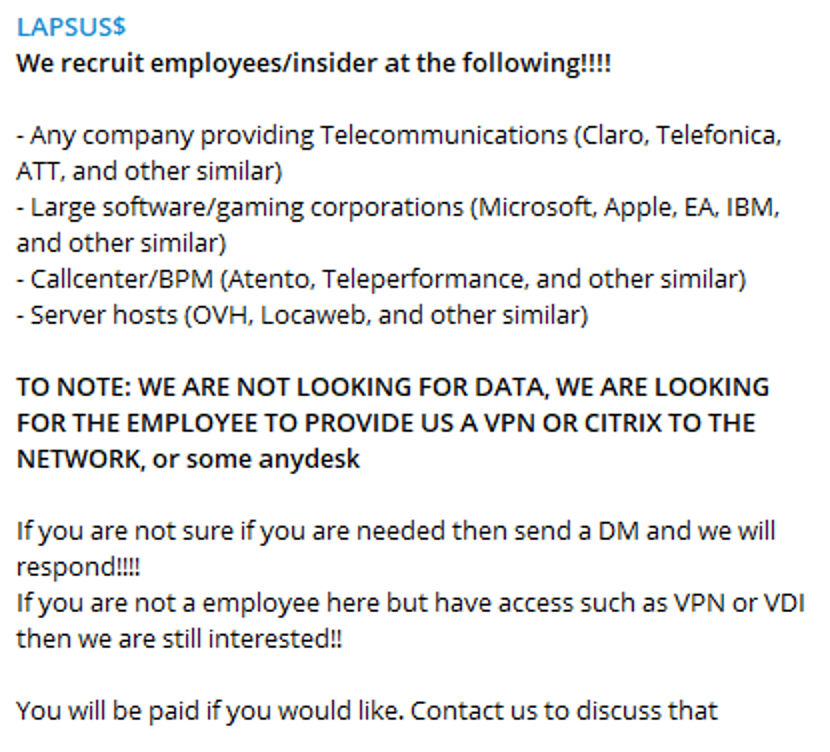
The Lapsus$ group claims to be a ransomware gang, and has so far only communicated from their Telegram channel. The group’s ambitions also appear to be expanding. On Thursday, March 10th, Lapsus$ posted an open invitation to insiders at Microsoft, Apple, EA Games, and IBM. In the invitations, the insiders were asked to provide Lapsus$ with access to internal company systems. It’s quite uncommon for a hacker ring to recruit publicly.
The Lapsus$ Data Breaches: A Quick Timeline
After emerging in December 2021, Lapsus$ went under the radar until a new string of data breaches started making news waves in March. It’s still a developing story, but here’s what we know about their recent ransomware attack spate so far.
February 2022: The Nvidia Hack
On Tuesday, March 1st, Nvidia announced they had become “aware of a cybersecurity incident which impacted IT resources” that happened on February 23rd. The company said it had no evidence of ransomware being deployed on its systems, but admitted a malicious actor had stolen employee records and NVIDIA proprietary information. Lapsus$ later claimed responsibility for the attack.
The group said they had stolen over a terabyte of data from Nvidia’s systems, including source code for drivers and firmware, hardware schematics, and silicon chip files. The group also released the email addresses and Windows password hashes of 70,000+ Nvidia employees. Some of the data had reportedly already been cracked.
Along with the announcement, Lapsus$ made an unusual demand: Nvidia had to remove the LHR limitations on its 30 series graphics cards before Friday, March 11th. Otherwise, the group would leak the company’s top trade secrets. The group later updated their demands to include that Nvidia was also to make its GPU drivers for Windows, macOS, and Linux open-source.
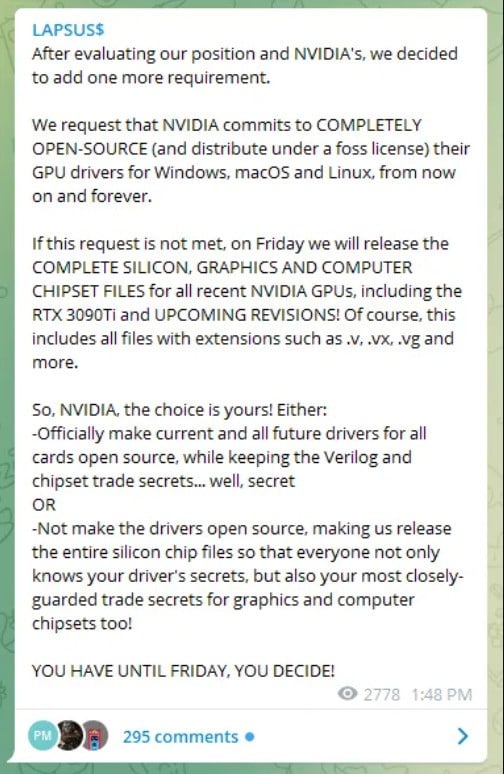
At the time of writing, Nvidia has yet to comply or release further statements about this developing situation. Lapsus$ hasn’t acted on their threat to publicly release any more Nvidia files either.
February 2022: The Samsung Hack
Less than a week after the Nvidia news hit, Lapsus$ claimed they had also hacked into Samsung’s systems and stole 190GB of code. The company admitted that biometric authentication algorithms and bootloader source code for the Galaxy series smartphones had been stolen.
In their response, Samsung stated that the stolen data didn’t include any customer or employee data. They also assured that this attack wouldn’t affect normal business activities.
On their Telegram channel, Lapsus$ said the stolen data includes source code for Samsung’s TrustZone environment. It manages core utility programs (applets) that run Samsung smartphones’ most sensitive operations, including biometric authentication. Apparently, the stolen data also includes confidential files from chipmaker Qualcomm, who creates the processors that run Samsung phones in the US and other markets.
Hackers have now leaked all 190GB of Samsung’s stolen code. While Lapsus$ claims to have stolen and leaked the data, it doesn’t appear they demanded anything from Samsung beforehand. That’s atypical of a ransomware ring that normally tries to extort victims for money (usually cryptocurrency) first.
February 2022: The Vodafone Hack
Shortly after the Samsung breach, Lapsus$ took to Telegram again to post a poll and report they had stolen 200 GB of source code files from Vodafone. These files were contained in 5,000 GitHub repositories. In February, Vodafone Portugal had suffered a cyberattack, which temporarily disrupted its services across the country. It’s unclear whether the incident is linked to Lapsus$’s data theft.

Vodafone has only replied that it’s still investigating whether its systems were compromised. “We are investigating the claim together with law enforcement. At this point, we cannot comment on the claim’s credibility. However, what we can say is that generally, the types of repositories referenced in the claim contain proprietary source code, not customer data, ”a Vodafone spokesperson told CNBC.
Lapsus$ has threatened to leak the stolen Vodafone source code, but they have yet to follow through on that promise.
March 2022: The Ubisoft Hack
Ubisoft is the latest major company to have allegedly fallen victim to Lapsus$. Ubisoft confirmed they had suffered a cyber attack in early March, which disrupted some of their games and services. The publisher released a short statement to reassure the public that none of its players’ personal information was compromised. In response, Ubisoft has initiated a company-wide password reset.
Shortly after the news broke, Lapsus$ shared a news story link about the Ubisoft hack on its Telegram channel, followed by an emoji. The group hasn’t shared any more details yet, so their involvement is still speculation. Ubisoft has also not yet released any further information about what the cyberattack entailed.

Bluffing Big or Truly Skilled?
A few days after the Nvidia breach in February, Lapsus$ took to its Telegram channel again to post this bit of news in all caps.
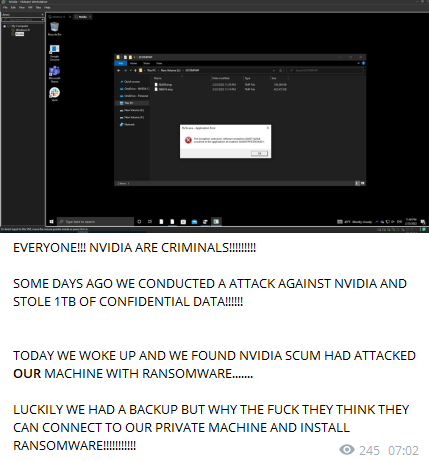
It’s still unclear whether Nvidia actually did ‘hack the hackers back’. At this point, the validity of all Lapsus$’s claims is up for speculation. The group seems to be struggling to find its feet, so to speak. According to Forbes, when the group first popped up in June 2021, they were trying to claim responsibility for an Electronic Arts leak that a different actor had already shared elsewhere.
“Based on their public behavior, the actor does not look very mature and experienced. That’s especially true considering the miscommunication and even public clashes happening between group members, who aren’t agreeing on how to leak Nvidia’s data,” dark web threat hunter KELA also told Forbes. The group’s obscure demands, along with their reluctance (or inability) to follow through on threats highlight their amateurish nature and delusions of grandeur.
That said, someone has definitely hacked Nvidia, Samsung, and Ubisoft. Important data was stolen from them, too. We’re even seeing some fall out because of this. Other cybercriminals have already started creating malware using expired Nvidia security certificates released by Lapsus$.
Secure Your Accounts and Devices

What does all of this mean for you? Nvidia’s security certificates being used for malware shows that users will be indirectly affected by the attack. Cybercriminals will be better able to find exploits and create more believable malware using the stolen data. That proves users may still face consequences, even if their personal information hasn’t been leaked.
These events remind us how important it is to stay vigilant. Scrutinize the apps and services you use, activate privacy features, and look out for malware. Always use robust security tools, like good antivirus and antimalware programs. You should also get CyberGhost VPN to protect your devices and connection from outside malicious actors. Cybercriminals won’t be able to break through our secure 256-bit AES encryption to worm their way into your PC or Android phone.
Lapsus$ seems to be sticking to large corporations for now. That said, small and medium businesses aren’t safe. They’re often more vulnerable to cyber attacks. CyberGhost VPN offers a secure dedicated IP solution to help companies secure their employees’ network connections. This gives you the opportunity to let employees access the company intranet securely without struggling with authentication issues based on changing IP addresses.



Leave a comment