Ever counted how many times a day you need to prove you are who you say you are?
How often do you unlock your phone by pressing the Touch ID sensor with your finger? Maybe you have to go through a facial recognition system to enter your office building every day, after your lunch break, or when returning from a meeting. You may even sign documents or pay for your coffee using Face ID.
Proving your identity using biometric technology has become a vital part of your daily routine. True, biometrics make your life a whole lot easier. Still, despite the arguments of companies who design this technology, so far, it hasn’t shown it also makes your life more secure. What it has shown is that biometric tech’s numerous flaws put your identity and privacy at risk.
Here’s a closer look at biometric technology and its current privacy issues and concerns.
You’ll get the perspective of biometrics from 4 different angles:
-
-
-
-
- The global applications of biometric technologies
- Biometric data privacy and security failures
- The legal status of biometric data
- Biometrics used as social systems
-
-
-
Biometric Technology – All Eyes Are on You
If you were ever in a hurry and went to a store across the street in your pyjamas, apart from the store seller, chances are you’d go unnoticed. The situation would be completely different if you were living anywhere in China. Here, the entire city would know and even see everything you do outdoors.
China’s monitoring cameras are part of its social credit ranking system, with over 200,000 CCTV cameras in its major cities. The better Chinese people behave, the higher their score is. Based on a high score, the government grants Chinese citizens more social benefits from private education to vehicle purchases and others.
Chinese authorities rate wearing pyjamas outside the house as ‘uncivilized behavior’ and publicly humiliate citizens who dare to break this rule. Public shaming relies on displaying citizens’ real-time footage caught by CCTV cameras, along with their full names and ID card numbers.
That’s just one real world example of how far biometric technology goes today.
We live in a world where biometrics, the technology that allows you to identify yourself by your physical characteristics and behavior automatically, is everywhere. It’s almost impossible to avoid being identified, tagged, or caught on a screen.
Companies and services have adopted biometric technology exponentially in the last decade, mainly because it’s so handy across diverse sectors like:
-
-
-
-
- Military – for enemy/ally identification
- Border, travel, and migration control – for traveler/migrant/passenger identification
- Civil identification – citizen/resident/voter identification
- Healthcare – patient/beneficiary/healthcare professional identification
- Physical and logical access – owner/user/employee/ contractor/partner identification
- Commercial applications – consumer/customer identification
-
-
-
Sometimes, identification through biometrics happens with your consent and other times without you even knowing. When it’s done without your ‘seal of approval’ you should start worrying about your privacy and security.
Examples of Biometrics Security Failures
As it turns out, biometric technologies have had their share of mishaps. What’s important to know is what companies do to prevent biometrics failures from happening again, and notably, whether they take your data privacy and security seriously.
1. What happens to your data once the biometric system captures it? Does anyone or any system delete it after it serves its purpose?
Some companies delete your data after they process it. Others archive your data, but their systems can still access your data.
2. Where’s your data stored?
Companies often store biometric data in a database connected to the internet or in the cloud.
3. Who has access to your data, and what do companies do to protect it?
That depends on each company. You should always check companies’ privacy policies and terms and conditions. You can also always contact the company and ask them.
4. What happens if a company suffers a security breach?
Based on privacy laws, a company should inform you when this happens. The big question is how a company can replace fingerprints or iris scans if it suffers a data breach?
Sadly, very few companies that use and record your face features and body movements are entirely transparent regarding their security practices on biometric data. When you look through companies’ privacy policies, you’ll rarely (if ever) find any clear details as to what methods they enforce to protect your sensitive data.
Here are some examples of biometrics’ privacy and security blunders that show how this technology hasn’t established proper guidelines and fair practice rules just yet.
The Unexpected Privacy Issue from iPhone X
September 2017: Apple released iPhone X in 2017 with great enthusiasm. The novelty and highly awaited feature was the face ID, meant to scan and unlock your phone. The feature failed big time, though. Instead, people with similar facial attributes to yours could unlock your phone. So much for Apple’s utmost privacy and safety claims!
Interestingly, though face ID was a fail (at least in the beginning), researchers managed to determine that facial features captured on iPhone X (and on any other tool using facial recognition for that matter) could reveal an individual’s political views.
For some, this is sensitive and personal information that a facial recognition system could potentially exploit. The danger is even greater if the system wrongly labels you as a Neo-Nazi extremist and you end up being doxed. You could also be added to governments’ mass surveillance programs.
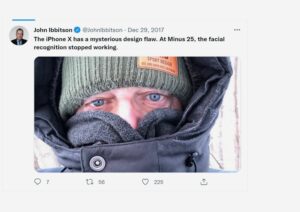
Twitter, Revealing some of iPhone X’s initial Face ID flaws
Easy Access Within Suprema Company’s Fingerprint Database
August 2019: Many businesses use biometric data for employment purposes, like fingerprint-based authorization or access systems for employees.
Security company Suprema offers this kind of service for law enforcement organizations, defense contractors, banks, and other organizations. Still, it doesn’t seem to enforce suitable data security methods.
Two Israeli researchers successfully accessed the company’s database and captured fingerprints of over 1 million people and facial recognition data of Suprema’s clients worldwide. They also managed to play around with the data, adding their fingerprints to the list of existing users.
Just imagine you’re an employee of this company. As science fiction as it sounds, someone could steal your fingerprint and use it to access your company’s unauthorized systems. Because it’s your fingerprint, you’ll be found guilty for the crime.
Amazon’s Palm Print Campaign
August 2021: Amazon released a promotion giving you $10 if you signed up using your palm print with Amazon One. Amazon One is a biometric device that makes a palm signature and links it to Amazon’s credit card and user account. The offer aimed to convince you to use Amazon One as a form of contactless payment.
The concerning element is that those who accepted to use Amazon One had their data, mainly palm signature, stored in the cloud where anyone with a few tech skills can easily access it. The possible outcome? Apart from someone using it to buy items from Amazon on your behalf, they could also use it for other services that require a palm print, like US Whole Foods stores.
The big security issue in this case is that, unlike a password, you can’t replace your palm print.
Since biometric tech is secure only up to one point, you’re probably wondering if proper regulations are in place to protect biometric data.
Biometric Data and Privacy Laws
Around 130 countries in the world have data protection laws, with almost all covering biometric data protection guidelines. At least in theory, these laws ensure biometric data isn’t used for purposes for which users don’t give their consent. Still, these laws lack the proper attention to racial bias, discrimination, or accuracy.
The EU’s GDPR (General Data Protection Regulation), for example, includes biometric data as a “special category of personal data”, forbidding anyone from processing such data. That said, the regulation accepts legal exceptions to this rule in the employment context, as long as the ‘subject has explicitly consented to the processing’.
Failing to comply with this exception could lead to a hefty fine. That’s what happened with a Dutch shoe retailer that received a fine of € 750,000 from GDPR in 2020. The company applied fingerprint authorization to control employee access to the cashier system, replacing the former personal code-based access method.
Not all employees agreed with this new procedure, stating it violates their privacy rights. They lodged a complaint with their local DPA (Data Protection Authority), ultimately the GDPR led an investigation, and concluded the Dutch company didn’t request employees’ consent for processing their fingerprints.
No Place to Hide: When Governments Adopt Biometrics
Over the last twenty years, biometric systems have become widely common in the civilian market taking the form of social and administrative systems. In many countries, governments can access your data, including your emails or phone records. The 5 Eyes Alliance is just one example.
Privacy lobbyists have raised concerns regarding a country’s possible transformation into a surveillance state the moment it also assumes control over people’s biometric data.
The following countries are known to hold intrusive administrative control over their people through biometric technology.
Malaysia – The Pioneer in Biometrics as a Social Administration
With one of the highest internet usage rates in southeast Asia, Malaysia was the world’s first country to adopt biometric identification in 2001. Its MyKad card carried an embedded chip that captured both fingerprint biometric data and photo identification. MyKad can also serve as a driver’s license, an ATM card, and an electronic purse, among other applications based on your chosen functions.
With Malaysia’s permissive data collection laws, you have no clear indication if you can control which information is public and which institutions are allowed to access it. It’s one of the reasons why Malaysia is one of the worst countries when it comes to privacy protection, ranking in the top five.
India – Home of the Largest Biometric Identification Database
Today, India has the world’s largest biometric identification database, called Aadhaar, covering about 99% of its 1.3 billion population. Aadhaar relies mainly on iris scans, digital photos, and digital fingerprints.
According to the government, the Aadhaar card has enabled millions of marginalized Indians to take advantage of identity-based services, like receiving food rations, opening bank accounts, applying for loans, and even having cooking gas delivered.
Still, laborers working with their hands and, as a result, suffering some damage to their fingerprint, exposed Aadhaar’s inaccuracy. The biometric framework didn’t recognize their fingerprints, and they were eventually being denied access to necessities like food and water.
China’s Advanced Surveillance Capabilities
China is an unsettling example of how far and deep biometrics technology can go in monitoring individuals. Golden Shield is the Chinese government’s program with a database that includes household registration, travel information, and the criminal history of 96% of the country’s 1.35 billion people.
Additionally, Safe Cities monitor traffic, and public safety, backed by Skynet – a sweeping facial recognition network of 200,000 public and private surveillance cameras.
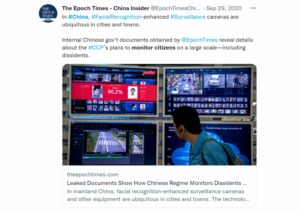
Twitter, China’s monitoring system through CCTV cameras extends
Skynet can do a clean sweep of the entire Chinese population, identifying individuals with 99.8% accuracy in one second, though some experts feel this may be an exaggeration.
Still, the country’s widespread surveillance tools are just another form of authoritarianism and censorship to which citizens (sadly) can’t evade.
Future Privacy Concerns with Biometrics
Biometrics isn’t going away anytime soon. New and terrifying possibilities in biometrics are creeping up, often with insufficient tests before their release. For instance, in the future, you may not be allowed to enter a restaurant or a store without an iris scan.
Sometimes, biometrics tech can accurately identify what happens in a video, but they can’t integrate it with the actual context. Surveillance cameras can tell if a person is hiding, but they can’t say if the person is playing a hide and seek game or doesn’t want to be found by the police.
The gender bias still lingers with most AI (artificial intelligence) systems using biometrics. Most categorize women in photos as smiling and looking pretty while labeling men as serious business leaders. Unless companies make rapid strides towards a privacy and security-oriented global regulatory body, we may be moving into a ‘Minority Report’ kind of world.
The more informed you are, the better you know how to avert this technology’s potential risks or seize its potential benefits.
1. Avoid being tracked on your devices
Keeping your emails and phone messages private is an uphill battle, but there are still a few tweaks that will help you boost digital privacy.
2. Consider using a more private messaging app
Some messaging apps are more private than others. Yes, there are plenty of options to replace WhatsApp if you don’t want to share your personal messages with Facebook.
3. Check useful tips on how to better understand a privacy policy
If you want the inside details of how a company protects and secures your personal data, read the fine prints of their privacy policy. There, you’ll get a better idea of how much they uphold their privacy claims.
FAQ
What are biometrics?
Biometrics refers to physical or behavioral human characteristics. They are used to digitally identify people to grant access to systems, devices, or data. Biometric technology is mainly employed to distinguish between humans and robots. Biometric data includes fingerprints, palm prints, facial features, or retina scans.
What are the most used biometric technologies?
The most common biometric systems include facial recognition, voice recognition, fingerprint scanning, and heart-rate sensors. Biometric technology can also analyze behavioral characteristics like typing rhythm, walking speed, heartbeat pattern, keystroke, or signature.
How can I protect my biometric data?
For personal devices, you can do one simple thing; use two-factor authorization. Adding a layer of authentication, like a token or security code you receive on your phone or email, secures your device, and access to your biometric data will be harder to crack.
What are some of the most dangerous risks with biometric data?
You have three main categories of privacy concerns with biometrics.
- Unintended functional scope: the authentication goes one or more steps further; like, discovering an eye health problem while scanning the retina.
- Unintended application scope: the authentication process correctly identifies a person even if that person didn’t wish to be identified.
- Covert identification: a person is identified without seeking identification or authentication, like when a subject’s face is identified in a crowd.
What’s your opinion on biometric technologies? Do you believe it’s possible to reach a compromise to enforce these tools while respecting people’s right to privacy?
Let me know in the comments below.



Leave a comment