An L2TP VPN uses the Layer 2 Tunneling Protocol (L2TP) to create a private tunnel for your online traffic. It was widely popular in the early 2000s, but the protocol is now considered outdated. That’s because L2TP is slower than other VPN protocols, easier to block, and less secure against advanced threats.
Most providers, including CyberGhost VPN, no longer support it. Instead, many VPNs now rely on faster and more secure protocols, like WireGuard® and OpenVPN. But, if you’re curious about how an L2TP VPN works, how to set it up, and how it compares to more modern options, we’ve got you covered.
What Is L2TP?
L2TP stands for Layer 2 Tunneling Protocol. It creates a private connection between your device and a VPN server to move your traffic through a virtual tunnel. However, on its own, L2TP doesn’t encrypt your data, which means anyone with access to that virtual tunnel could still see what you’re using your connection for.
That’s why L2TP is almost always paired with IPsec (Internet Protocol Security). IPsec adds encryption, turning L2TP’s open tunnel into a secure one and protecting your activity from prying eyes. This combination is called L2TP/IPsec.
L2TP/IPsec was developed in the late 1990s to secure dial-up connections. Most of today’s major operating systems (Windows, macOS, Linux, iOS, and Android 11 and below) still support it. However, the protocol’s core parts are now considered outdated. It’s slower, less flexible, and more vulnerable than modern alternatives. If you decide to use it, you’ll need to set it up manually.
How an L2TP VPN Works
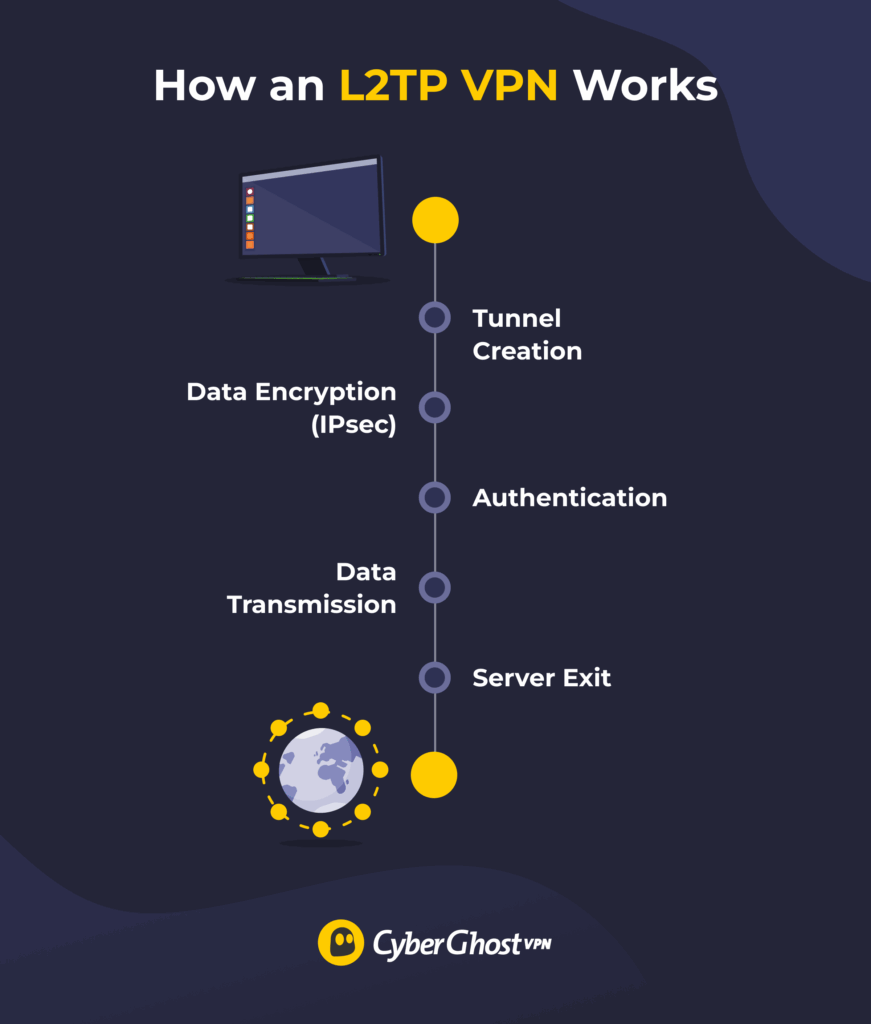
L2TP VPNs combine the L2TP protocol with IPsec to create a secure connection. Here’s how it works, step by step:
-
- Tunnel creation: L2TP creates a private tunnel between your device and the VPN server.
- Traffic encryption: IPsec wraps your internet data in encryption to keep it hidden from prying eyes.
- Connection authentication: Your device and the VPN server confirm each other’s identity.
- Data transmission: Encrypted data travels through the tunnel to the VPN server.
- Server exit: Once your data reaches the VPN, it goes out to the internet using the server’s IP address instead of yours. This makes it harder for websites to detect who and where you are.
Pros and Cons of L2TP VPNs
While L2TP is now outdated, it hasn’t vanished completely; some systems and networks still support it. Let’s check out the pros and cons.
L2TP VPN Pros
-
- Compatibility with older devices: Many legacy operating systems support L2TP/IPsec, making it a fallback if your device can’t run newer protocols.
- Native VPN setups: Desktop and mobile operating systems usually have built-in L2TP support, allowing you to manually configure it without third-party apps.
- Support for some legacy networks: L2TP/IPsec can connect in certain environments where newer VPN protocols are blocked, like older corporate networks.
L2TP VPN Cons
-
- Lack of standalone encryption: L2TP needs IPsec to create a secure VPN connection. Without it, your data is left exposed to prying eyes.
- Outdated design: Unlike modern VPN protocols, L2TP has not seen updates in many years, which makes it more vulnerable to threats.
- Slower performance: Double encapsulation (L2TP and IPsec) can slow down your connection, especially for streaming or large downloads.
- Unreliable reconnections: L2TP doesn’t support seamless reconnections, so your session can drop when you’re switching networks or lose signal.
What Is an L2TP VPN Used For?
L2TP VPNs were once common for connecting remote workers and offices, but today the protocol is mostly outdated. It’s now occasionally used in a few niche scenarios:
-
- Legacy corporate systems: Some older enterprise networks still rely on L2TP/IPsec due to existing infrastructure and compatibility requirements.
- Older device support: Hardware or operating systems that can’t run newer protocols may still support L2TP/IPsec.
- Built-in VPNs: Many operating systems offer L2TP/IPsec as an option for built-in VPNs, though most also support IKEv2, which is faster and more secure.
- Last-resort fallback: In rare cases, networks may block newer protocols and use L2TP/IPsec as a backup option.
How Does L2TP Compare to Other VPN Protocols?
Each VPN protocol has its own strengths and weaknesses. Here’s how L2TP/IPsec stacks up against the most common ones.
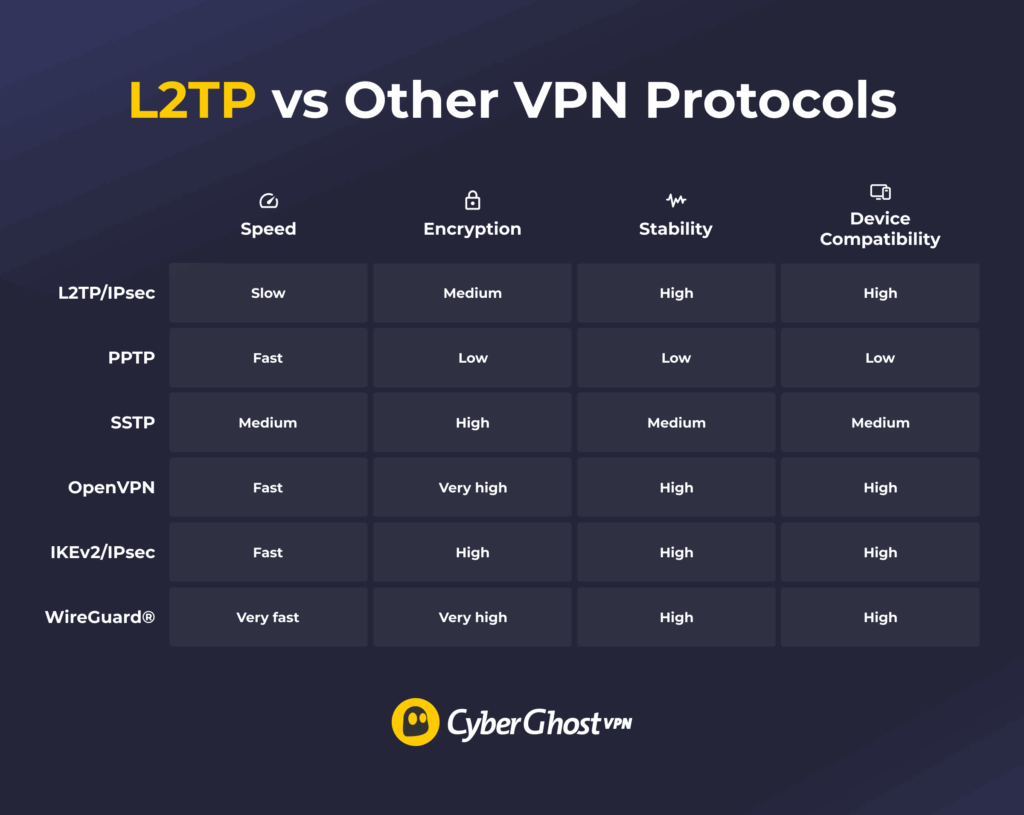
L2TP vs PPTP
PPTP is one of the oldest VPN protocols, once built into dated operating systems, like Windows XP. It’s fast but has critical security flaws, which is why it’s no longer in use. L2TP/IPsec is slower than PPTP because of extra encryption, but it’s more secure and still supported by many operating systems used today.
L2TP vs SSTP
SSTP is a VPN protocol developed by Microsoft and built into Windows. It can work on other operating systems, but only with third-party tools. SSTP uses strong encryption and can perform well on restricted networks, but it’s complex to set up on non-Windows devices. In contrast, L2TP/IPsec is built into most operating systems, making it easier to configure, but it’s not as secure or reliable as SSTP.
L2TP vs OpenVPN
OpenVPN is a modern protocol that offers stronger privacy and better performance than L2TP. It uses advanced encryption, which is more secure than the older IPsec encryption L2TP relies on. It’s also generally faster, making it a preferred choice for most activities. However, OpenVPN needs a VPN client to work, while L2TP/IPsec can be set up manually on most operating systems.
L2TP vs IKEv2/IPsec
L2TP and IKEv2 both use IPsec for encryption, but IKEv2 is newer and more advanced. It was built with mobile networks in mind and handles network changes easily, so you won’t lose your connection when switching between Wi-Fi and mobile data. That’s why IKEv2 is far more common than L2TP in today’s mobile VPN apps.
L2TP vs WireGuard®
WireGuard® is a modern, lightweight protocol that’s faster, more efficient, and more secure than L2TP/IPsec. It’s becoming the default protocol in many VPN apps. By contrast, L2TP/IPsec is older, slower, and more challenging to set up. While both protocols work on major operating systems, WireGuard® is the preferred choice, and L2TP/IPsec is often available as a backup option or not supported at all.
How to Set Up an L2TP VPN on Your Device
Some VPNs still support L2TP/IPsec as a fallback option. If your VPN includes it, you can usually select it from the protocol settings.
If your VPN app doesn’t offer L2TP directly, you can set it up manually. To do this, you’ll need an active VPN subscription. Your VPN provider must also support manual L2TP/IPsec connections. Before you begin, make sure you have:
-
- VPN server address: The web address or IP address of the VPN server you want to connect to.
- Pre-shared key (secret key): A shared password provided by your VPN for authentication.
- VPN username and password: Login details for your VPN account.
Once you have the information, you can set up an L2TP/IPsec connection directly in your device’s settings; no extra apps needed.
On Windows (10/11)
- Go to Settings > Network & Internet > VPN connections > Add VPN.
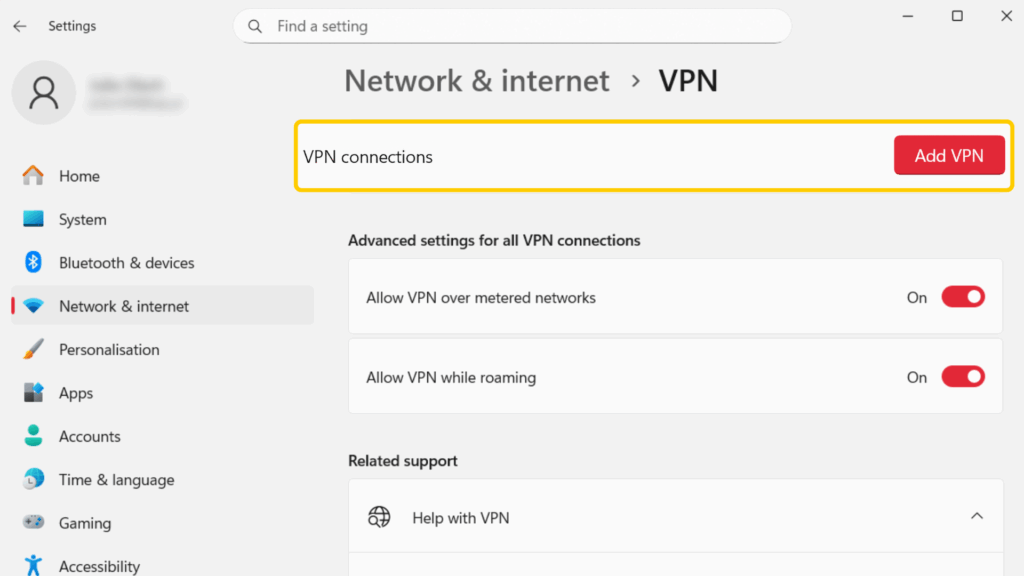
- In the Server name or address field, put the VPN server address.
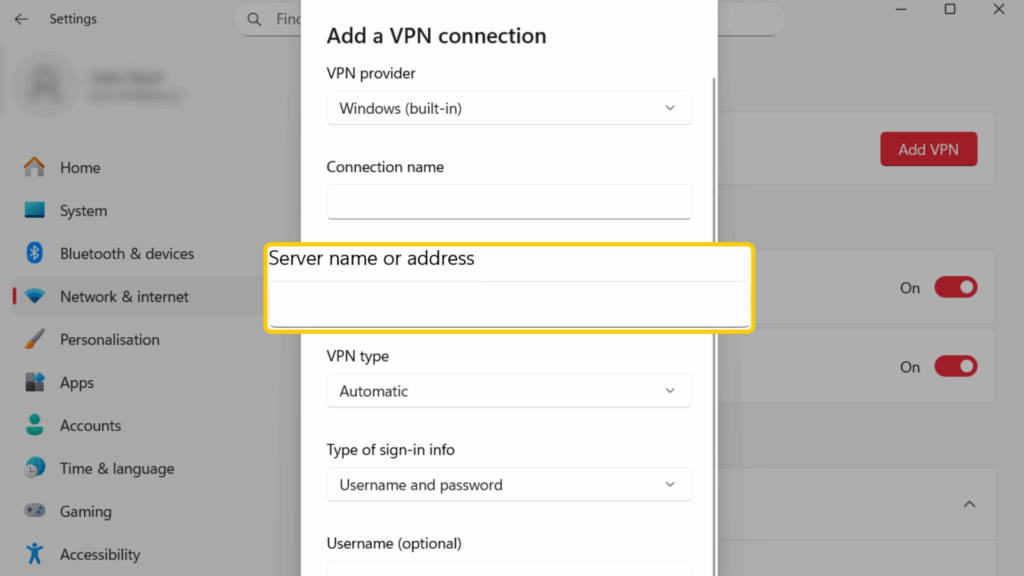
- Under VPN type, pick L2TP/IPsec with pre-shared key. Enter the shared key from your VPN provider.
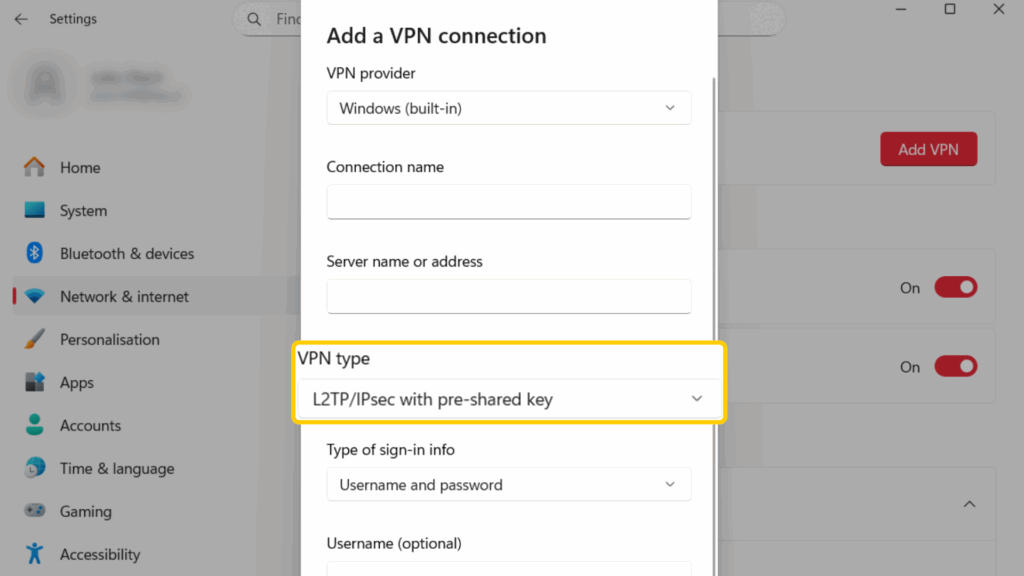
- Enter the VPN username and password you set up.
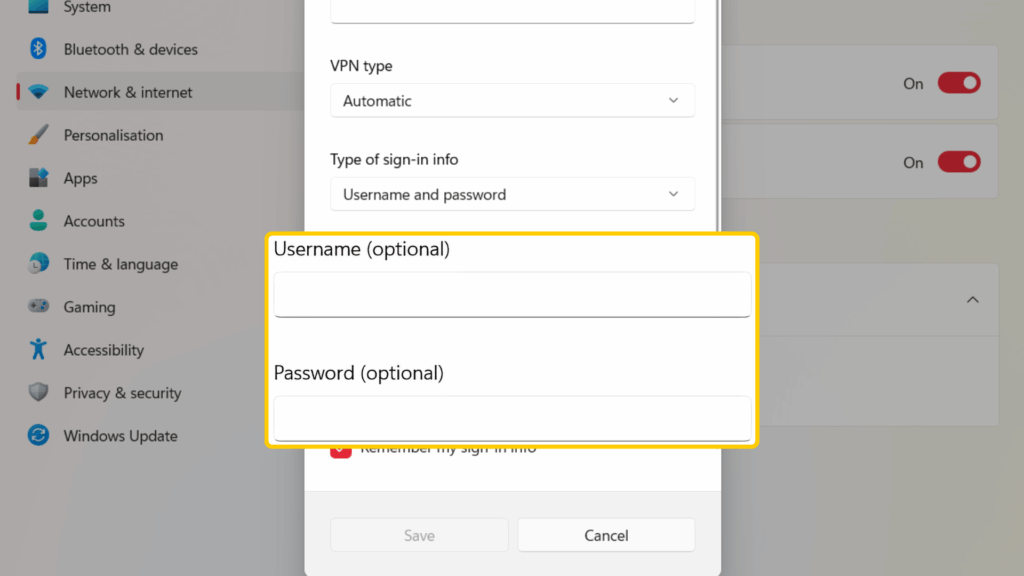
- Tick the box next to Remember my sign-in info, so you don’t have to enter your credentials each time you want to connect.
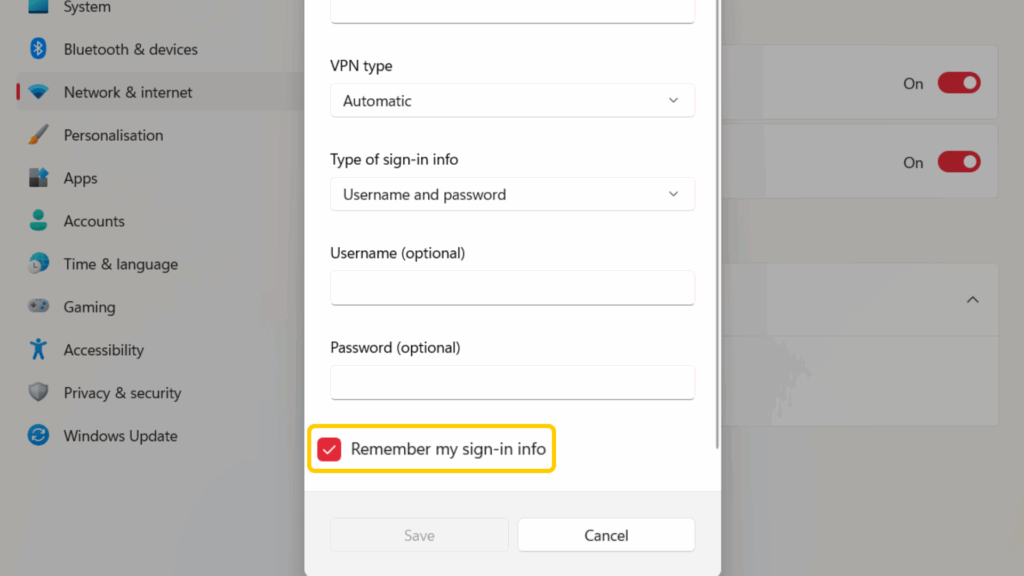
- Click Save and check if your new VPN connection works. You can do so by using an online IP checker and seeing if your details correspond to your VPN.
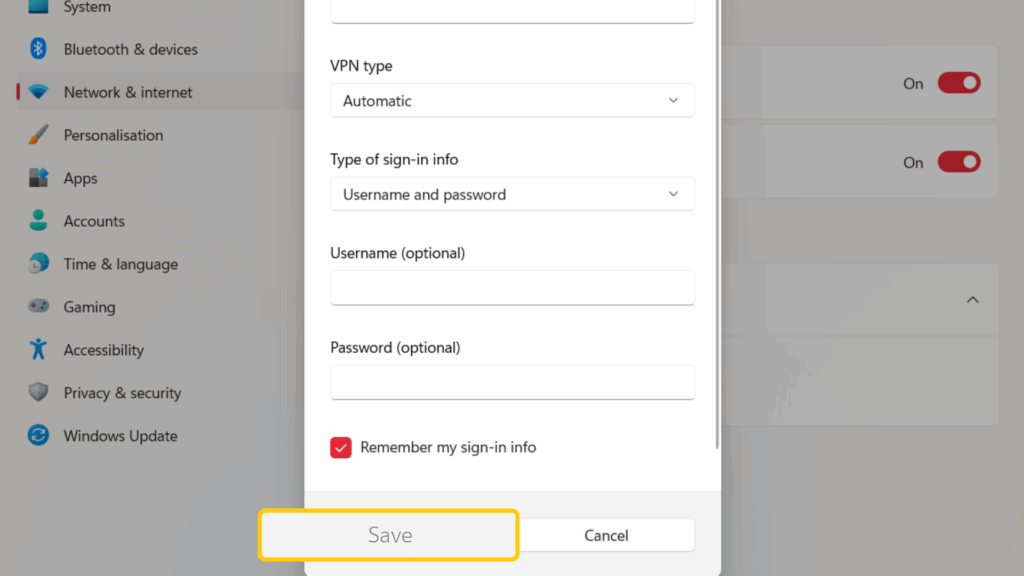
On macOS
- Go to Apple > System Settings > VPN.
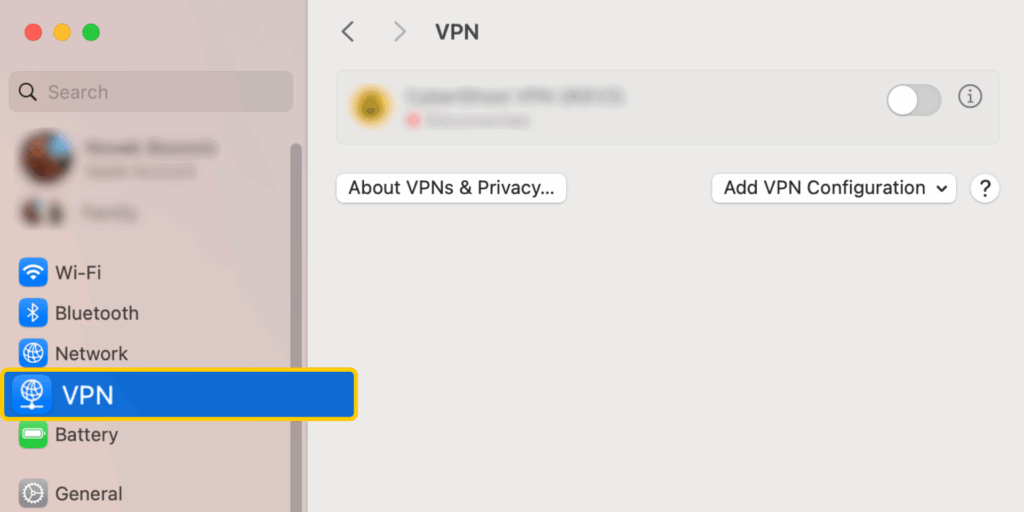
- Click Add VPN Configuration and pick L2TP over IPsec.
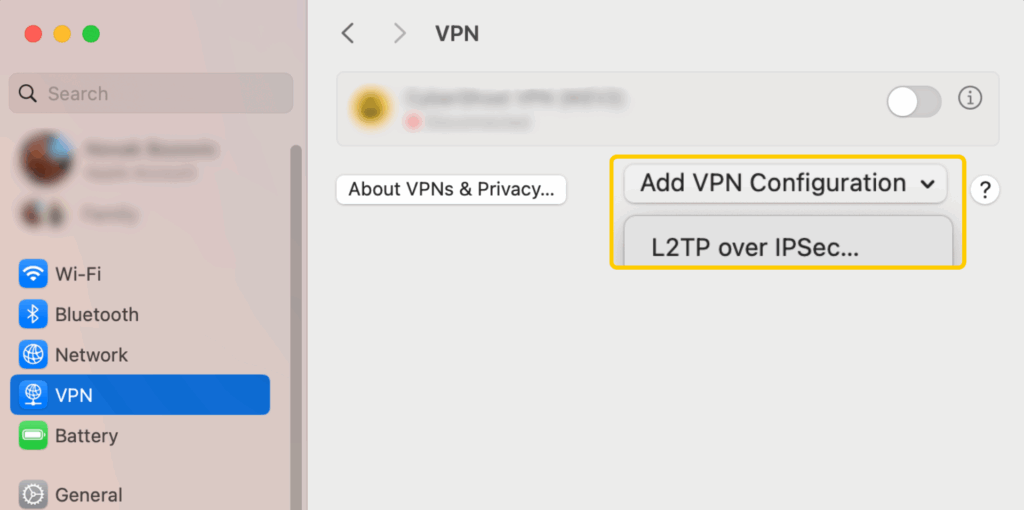
- In the Display Name field, enter a name for the connection.
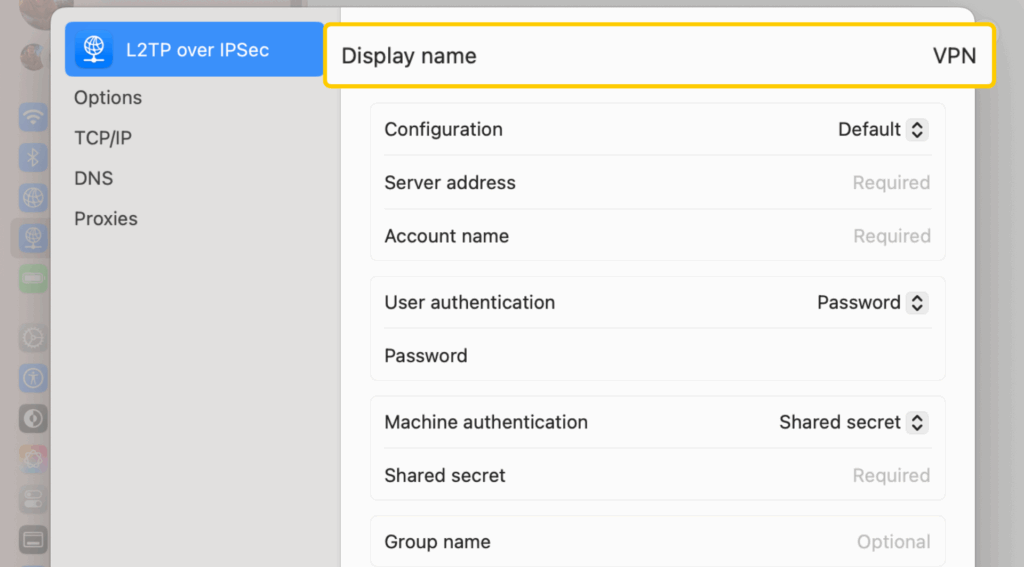
- Enter the VPN server address in the Server Address field.
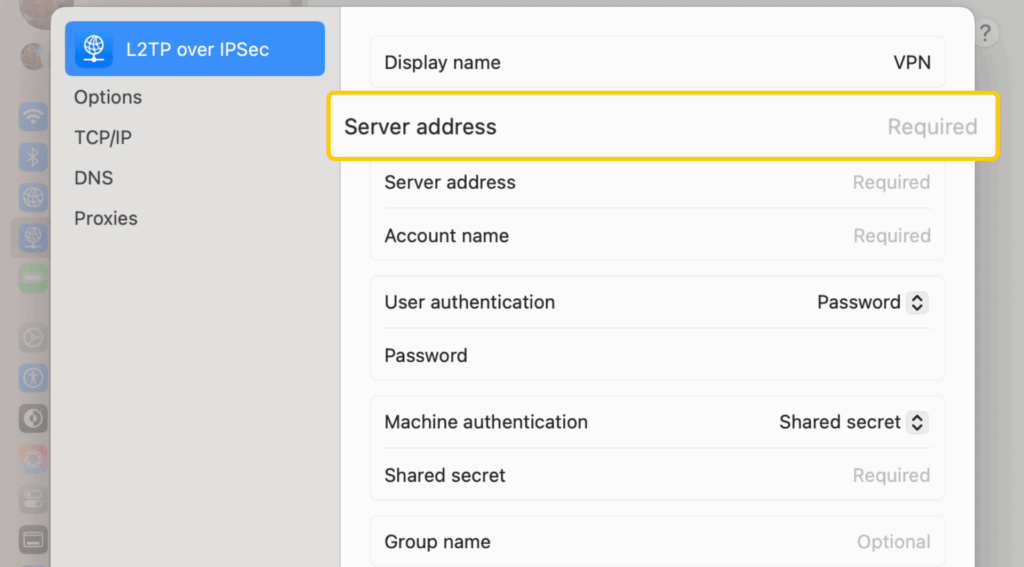
- In the Account Name and Password, enter your VPN credentials.
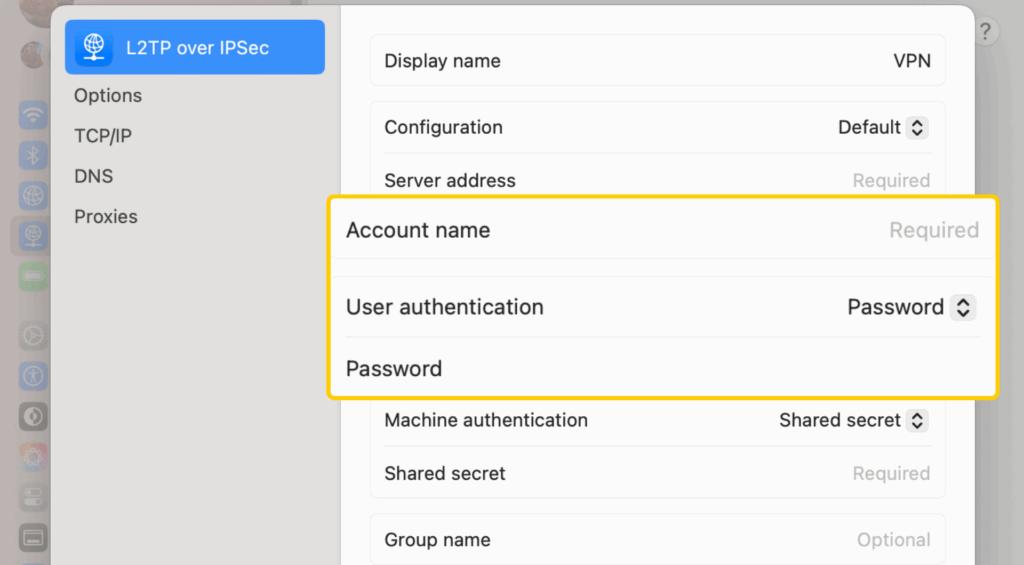
- In the Shared Secret field, copy the shared key given by your VPN.
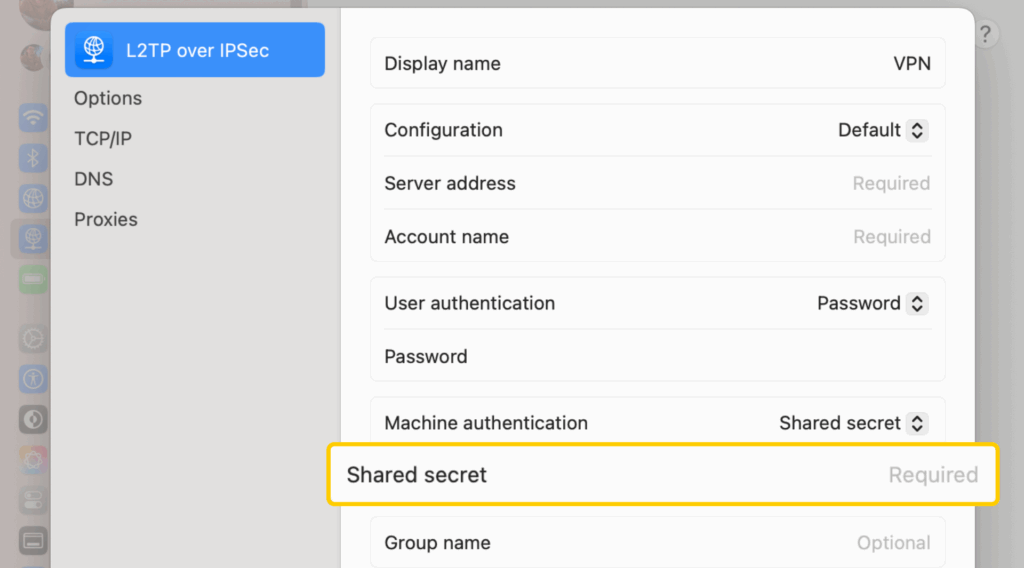
- Click Create and connect.
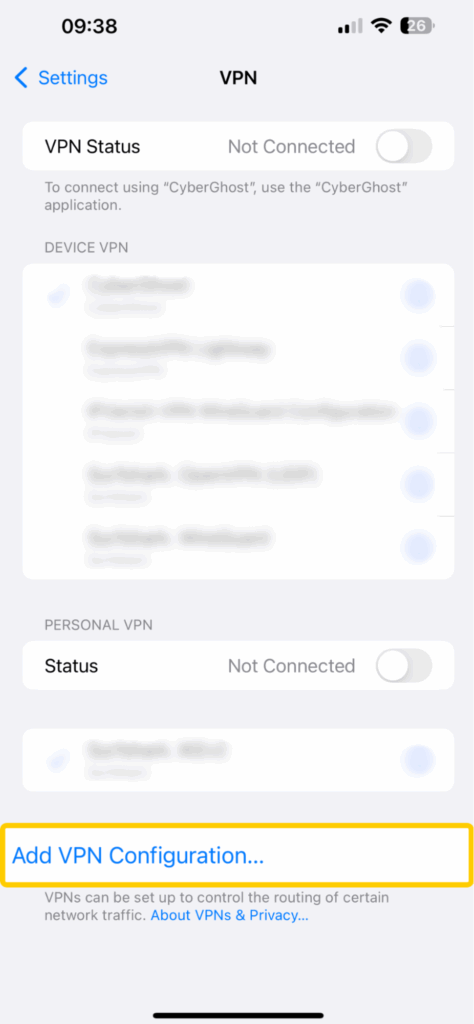
On iPhone/iPad
- Go to Settings > VPN > Add VPN Configuration.
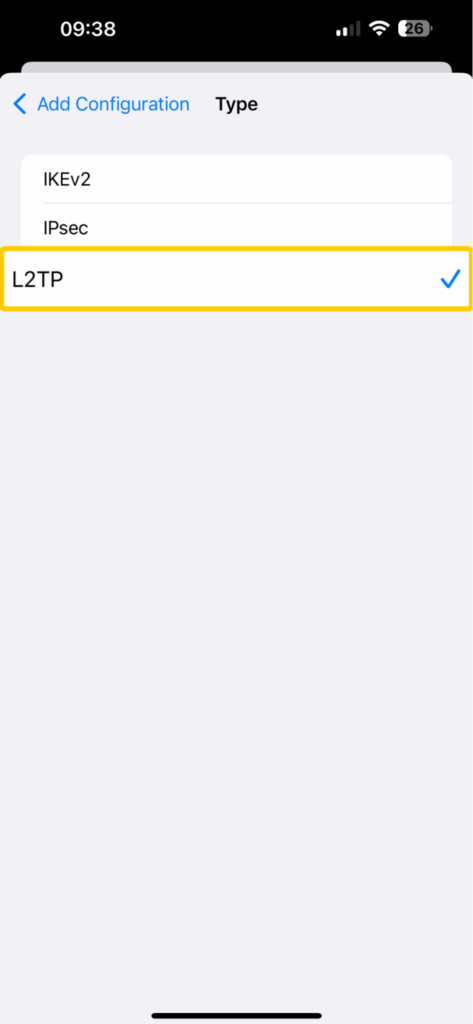
- Tap on Type and select L2TP.
- In the Description field, enter a name for your connection.
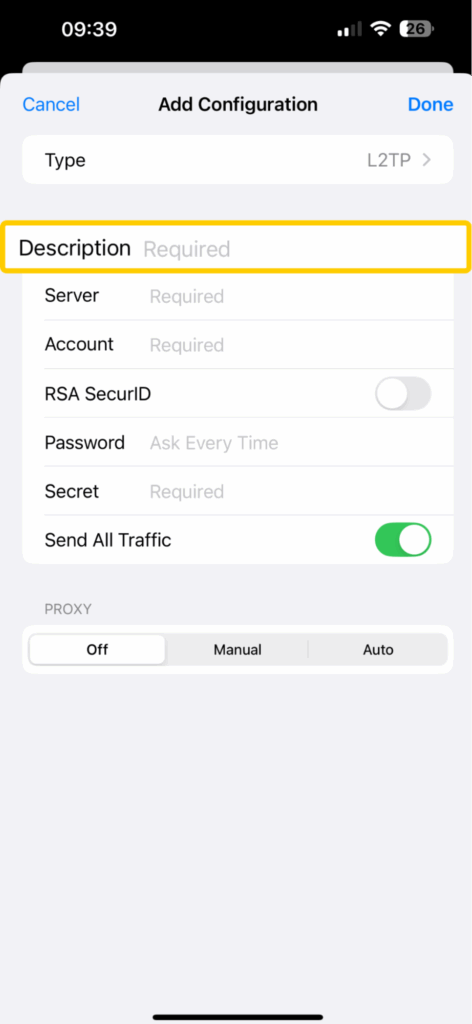
- Copy the VPN server address into the Server field.
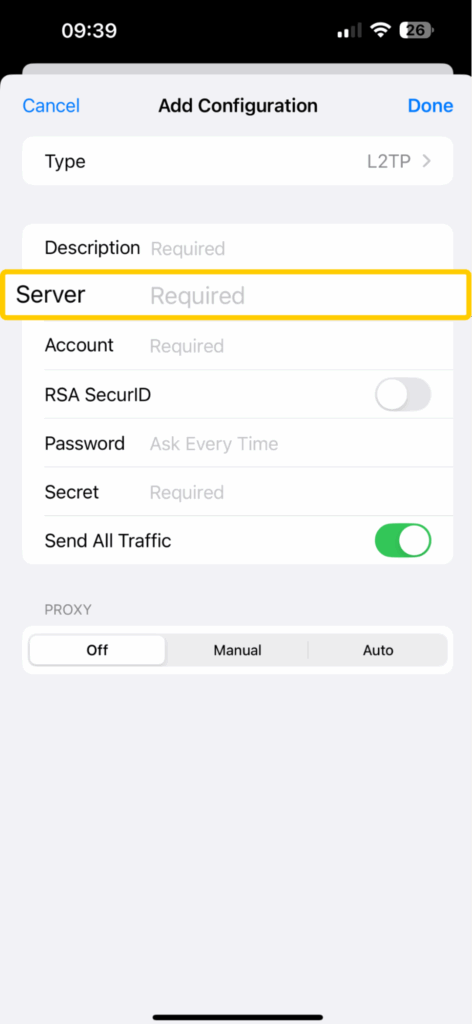
- In the Account and Password fields, enter your username and password.
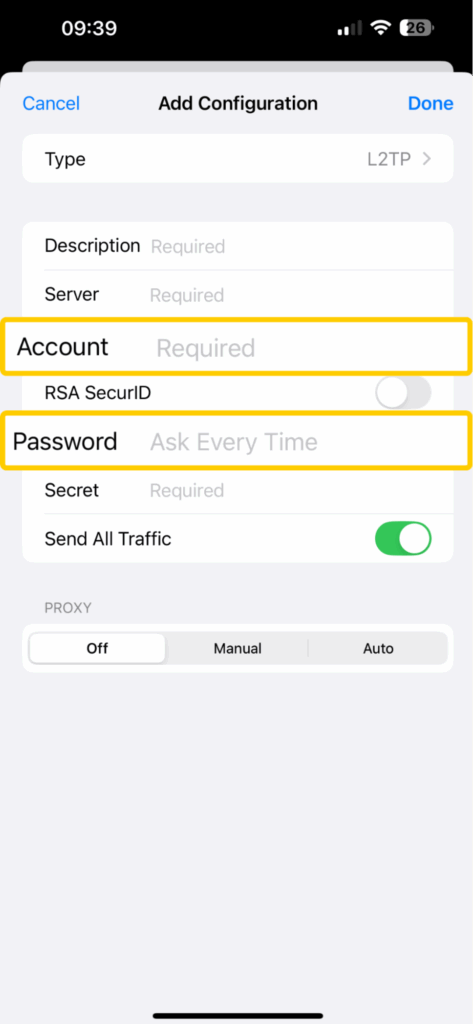
- Copy the pre-shared key given by your VPN into the Secret field.
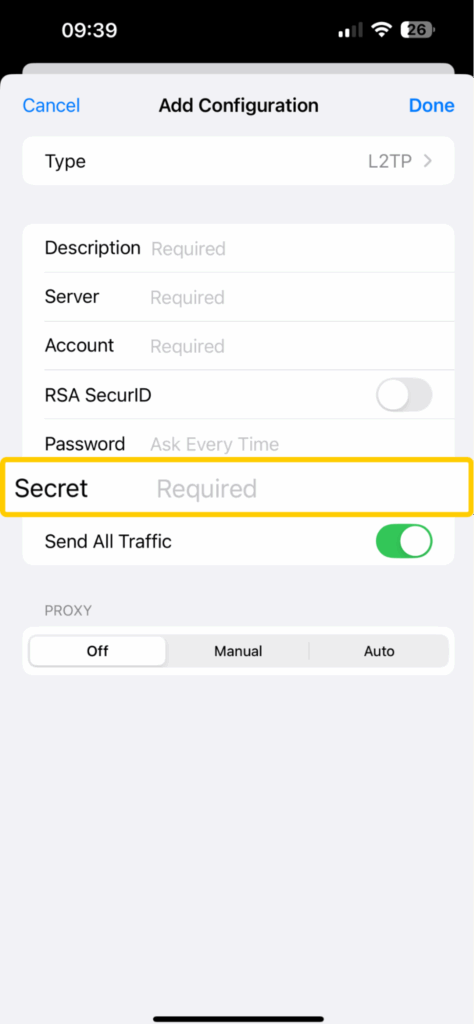
- Tap on Done to return to the previous screen, where you can toggle the VPN on to connect.
On Android (11 or older)
- Go to Settings > Network & Internet/Connections > VPN (or More connection settings/Advanced on certain versions of Android).
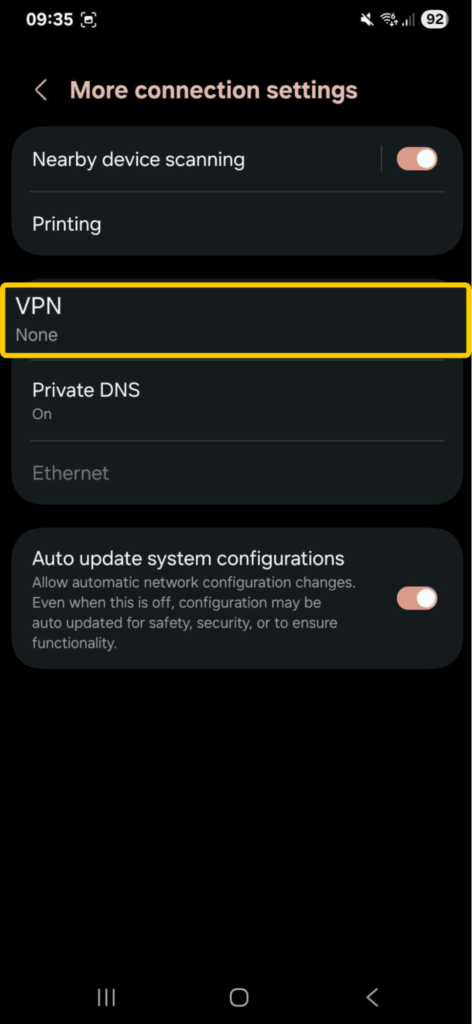
- Tap on the three dots in the top right corner and choose Add VPN profile.
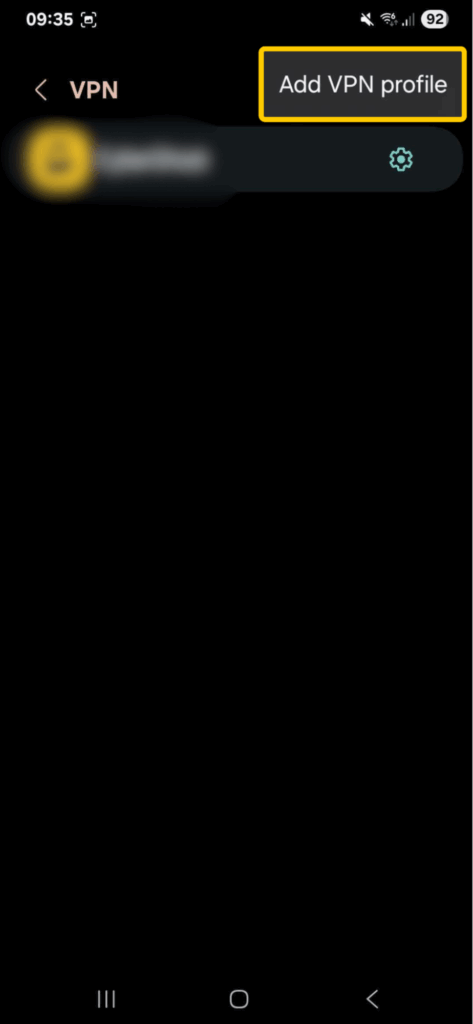
- Select Type and pick L2TP/IPsec PSK.
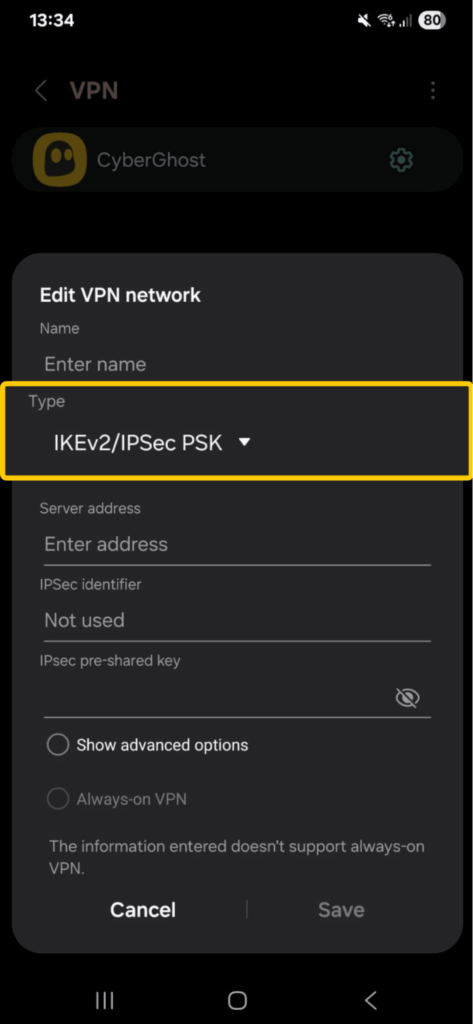
- Enter the server address and the IPsec pre-shared key, both of which are given by your VPN provider. Give the profile a name and save.
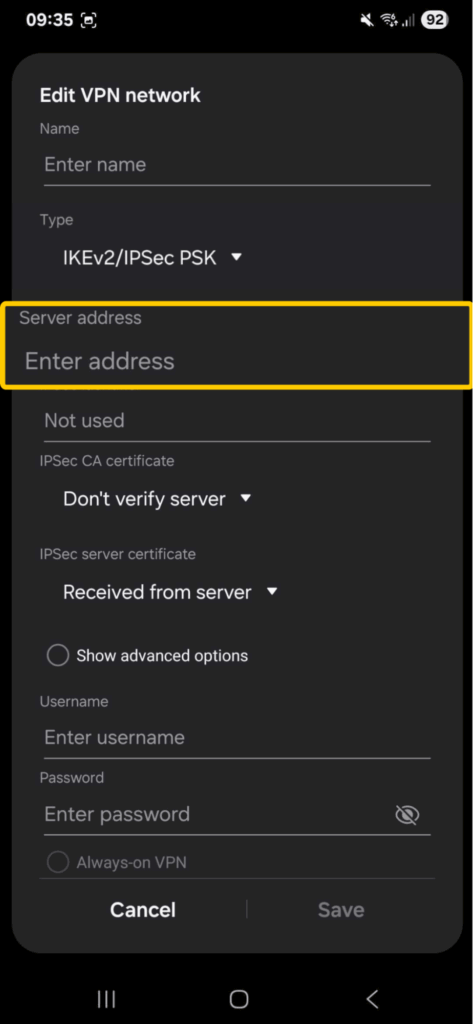
- Add your VPN username and password.
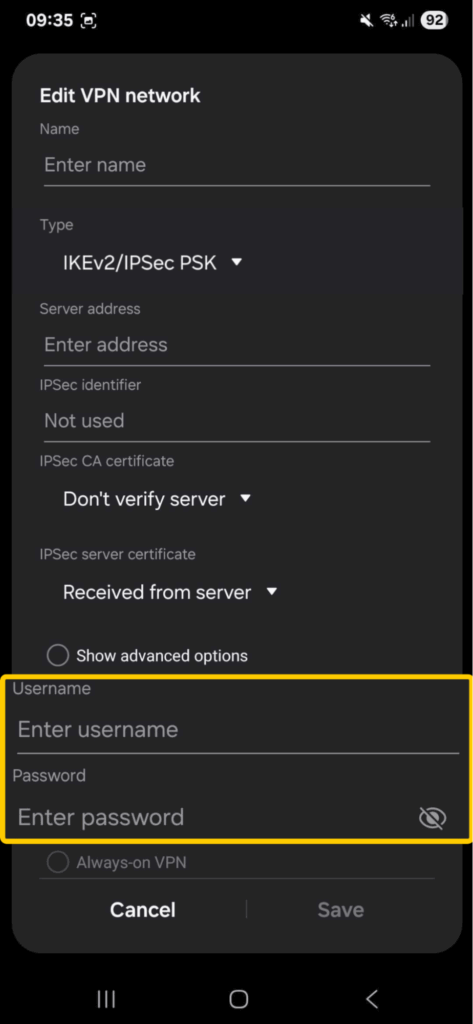
- Tap on Save to create your new VPN connection. You can now connect and check if everything works properly.
Choosing L2TP/IPsec VPNs May Not Be the Best Idea
While L2TP can be made more secure by pairing it with IPsec, it’s no match for modern VPN protocols. It’s slower, less secure, and less reliable than today’s alternatives, making it less than ideal for activities like streaming or online gaming. Instead, consider choosing safer and more reliable options, like IKEv2 or WireGuard®.
CyberGhost VPN supports modern, fast, and ultra-secure protocols: WireGuard®, OpenVPN, and IKEv2. You also get user-friendly apps for major operating systems, making it simple to connect. There’s a 45-day money-back guarantee if you choose a long-term plan, giving you plenty of time to test-drive all the VPN’s features.
FAQ
What is L2TP in a VPN?
L2TP (Layer 2 Tunneling Protocol) is a VPN protocol that creates a connection between your device and a VPN server. On its own, it doesn’t encrypt your data. That’s why it’s almost always paired with IPsec, a separate protocol that handles encryption. Together, L2TP/IPsec offers basic security and privacy, but it’s not as reliable as other modern VPN protocols.
How to connect to an L2TP VPN server?
Some VPN apps still let you choose L2TP/IPsec, but most no longer support it. If your VPN does, you can set it up manually by entering the VPN server address, your account credentials, and a shared secret key. You can do this on Windows PCs, Macs, iPhones, Android phones, and even older routers. Note that you still need a VPN subscription to connect to servers.
Is L2TP still used?
Yes, but not as much. L2TP was popular in the early 2000s because it was more secure than other protocols at the time. Today, it’s outdated and mainly used as a backup option if newer protocols aren’t supported on a network or device. Most people use faster and more reliable alternatives like WireGuard® and OpenVPN.
Should I enable L2TP?
Only if you have no other option. L2TP is an older protocol that lacks the advanced reliability of alternatives like WireGuard® and OpenVPN. It can work as a backup in rare cases, but it’s not recommended for everyday use.
What does L2TP use for encryption?
L2TP itself doesn’t use encryption. It encrypts your traffic only when it’s combined with IPsec in a process called double encapsulation. This makes L2TP/IPsec slower than modern protocols, which combine tunneling and encryption into a single process.
What port does L2TP use?
L2TP uses UDP port 1701 to create a tunnel between your device and the VPN server. With IPsec, it also uses UDP port 500, and sometimes UDP port 4500 if your device is behind a router or firewall. If an L2TP/IPsec connection doesn’t work on your device, check if any of those ports are closed. You can do that using an online tool like CanYouSeeMe.org.


Leave a comment