If you own a medium or large business with a growing number of remote employees, you may have heard of VPN concentrators. These devices (or software solutions) let your employees connect securely to the company network and work as if they were in the office. However, site-to-site VPNs and IPsec VPNs have a similar purpose, so when should you actually invest in a VPN concentrator?
The short answer is that it depends on the scale. If you need to manage hundreds of remote users connecting to internal business networks, a concentrator can be a good option. Keep reading to find out how VPN concentrators work, their pros and cons, and what alternatives might be better suited for your business.
What Is a VPN Concentrator?
A VPN concentrator is a network device that establishes and manages a large number of VPN connections. It’s usually deployed at a company’s main office or data center. Its aim is to allow remote users, branch offices, vendors, or clients a safe way to access internal resources.
The key advantage of a VPN concentrator is the scale it operates on. Unlike a standard VPN router, it can support hundreds or thousands of simultaneous VPN tunnels without compromising security or performance. This makes it a solid option for enterprises managing remote employees and offices.
VPN concentrators can be used as hardware or software. Hardware concentrators can handle higher amounts of traffic and are easier to certify and audit, making them best-suited for industries with strict compliance standards, like healthcare or finance. Software concentrators are easier to scale and more cost-effective for mid-sized businesses, since they don’t need their hardware replaced when it’s time to upgrade.
Many companies today don’t use standalone VPN concentrators but instead rely on integrated solutions. There are alternatives that bundle concentrator functionality with other security tools, including antivirus protection and content filtering. There are even enterprise-grade routers or hardware firewalls that can act as VPN concentrators, too.
How Does a VPN Concentrator Work?
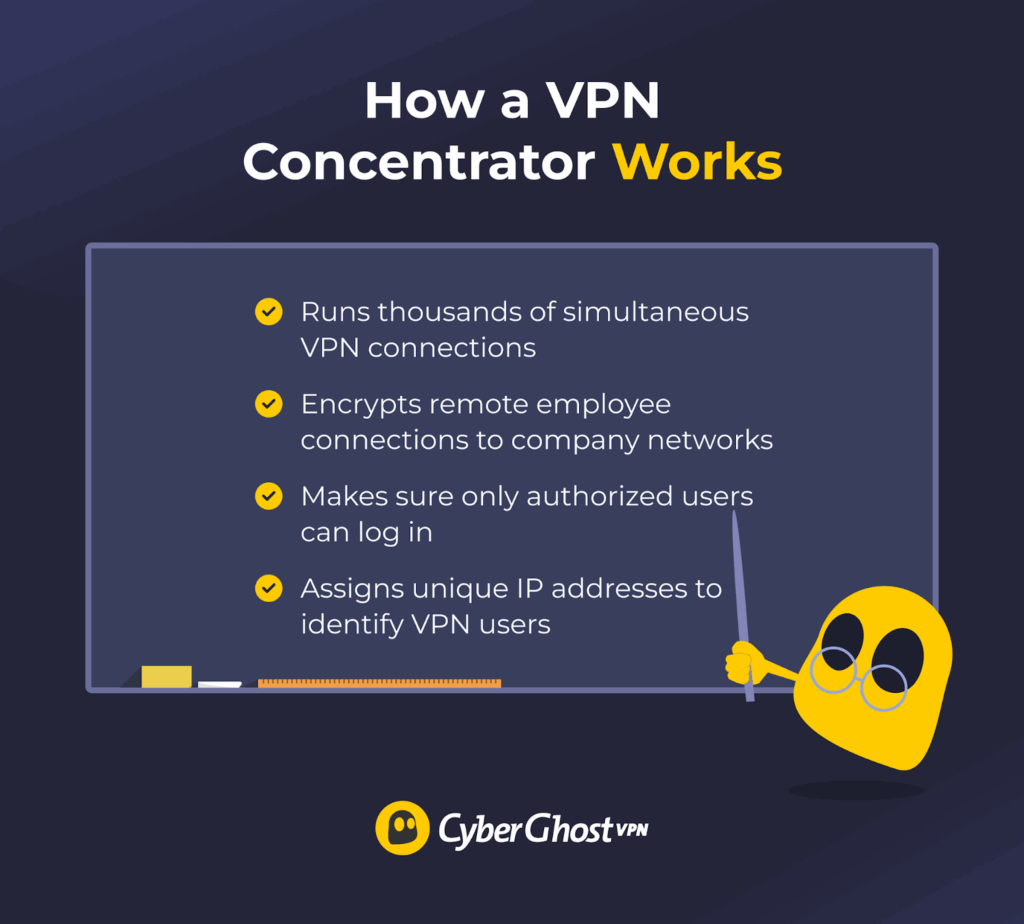
A VPN concentrator creates and manages private, encrypted tunnels between remote users and the company network. All traffic traveling through these tunnels is protected with VPN protocols, which encrypt and decrypt the data to keep it secure from interception. The concentrator can handle hundreds or thousands of encrypted connections simultaneously while ensuring that traffic is routed to the correct destination inside the network.
Before granting access, the concentrator authenticates remote users through a VPN client or a web portal. It then manages which resources or areas of the network the user can access based on rules set by the admin. The concentrator also assigns a unique IP address to each connection, making it easier to tell them apart on the network and manage and track users.
VPN Concentrator Protocols
VPN concentrators use VPN protocols to establish secure connections. Which protocol is used depends on the company’s security policies, what security standard it needs to comply with, and which protocol the concentrator is compatible with. The most common options include:
- IPsec: Works at a deeper level than other protocols, securing all traffic from a device or network, instead of just an app. It’s the most common protocol for VPN concentrators, but it can be technically complex to set up and manage.
- TLS/SSL: Uses the same encryption standard as HTTPS, the protocol used by secure websites. Often used in browser-based VPNs, where remote users connect through a web portal. However, this can sometimes mean that only browser activity is secured.
- OpenVPN: Provides flexibility because it’s open-source and highly customizable. Frequently used in software VPN concentrators, but it requires third-party software because it’s not built into operating systems.
- SSTP: Works well with firewalls because traffic looks like a regular internet connection, making it more difficult to block. However, it was designed by Microsoft for Windows, so cross-platform support is very limited.
- WireGuard®: Offers fast speeds thanks to its lightweight design, so it’s ideal for bandwidth-heavy tasks (like video calls or file transfers). It’s rare in enterprise-grade hardware concentrators but increasingly supported by some software concentrators.
Most VPN concentrators don’t support older protocols, like PPTP. That’s because PPTP’s encryption is weak, making it susceptible to cyberattacks, like man-in-the-middle (MITM) attacks. It’s no longer considered secure enough to safeguard private connections.
Advantages and Disadvantages of VPN Concentrators
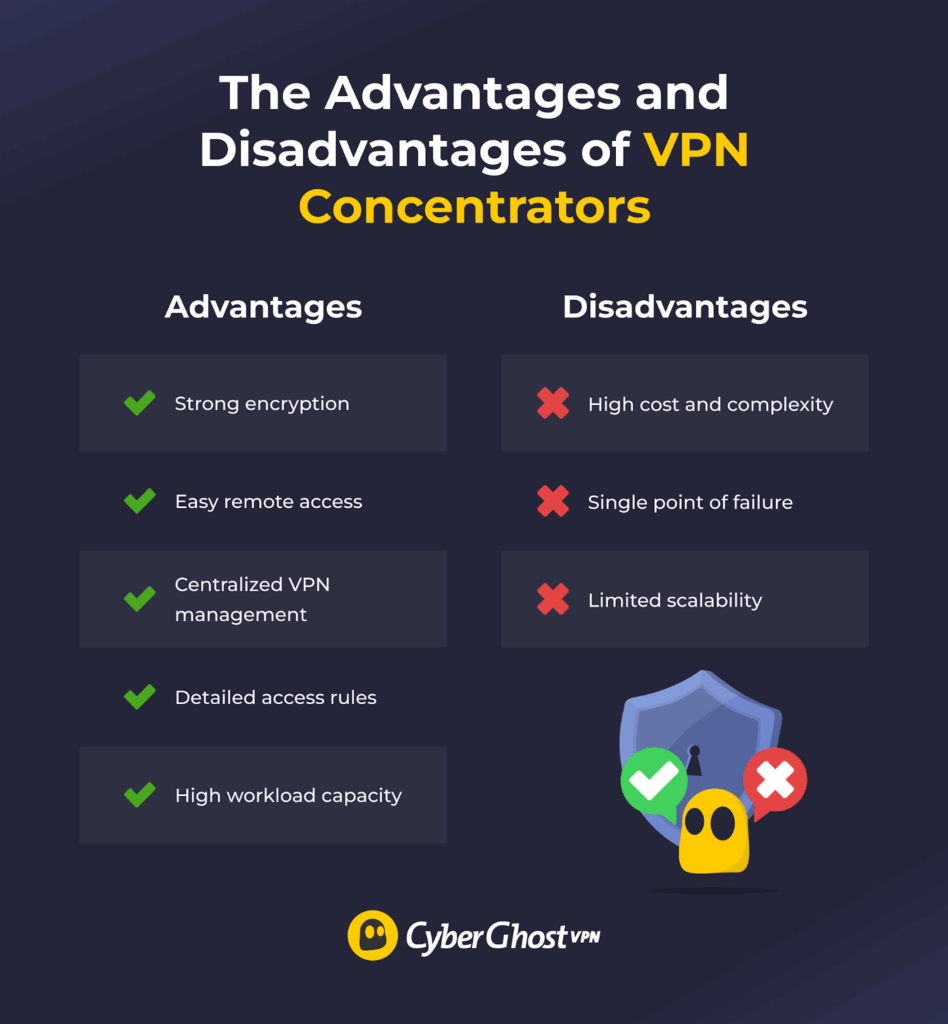
Before making a decision, you should consider the pros and cons that come with using VPN concentrators. Here’s a quick look at the most important ones.
VPN Concentrator Benefits
- Strong encryption: A VPN concentrator encrypts all data exchanged between remote users and the company’s network, making it harder for snoops to monitor connections or steal company data.
- Easy remote access: Once the admin sets up the VPN client on an employee’s device, the user only needs to launch it and log in to start working.
- Centralized VPN management: IT teams can easily monitor connections, apply policies, and manage user access.
- Authentication rules: Administrators can set rules for who can connect to the company network and what resources they can access.
- High workload capacity: VPN concentrators can handle thousands of simultaneous VPN connections, making them ideal for large companies with many remote workers.
Examples of Popular VPN Concentrators
Some of the most popular vendors of VPN concentrators (both standalone and bundled) include:
- Cisco Meraki: Sells hardware devices that double as VPN concentrators (like Meraki MX), offering networking and remote access from one place.
- Juniper Networks: Offers hardware firewalls that act as VPN concentrators, like the SRX5400, which supports IPsec connections.
- NetGate: Has the TNSR software router that can run as a VPN concentrator, supporting both IPsec and WireGuard® setups.
When Do You Need a VPN Concentrator?
VPN concentrators are usually chosen when an organization’s remote workforce grows significantly. They’re useful if you need to manage thousands of VPN connections or if your network has more traffic than a standard VPN server can handle.
Up to a few hundred connections, though, you can use a regular enterprise VPN instead. They’re often more affordable because they’re more limited when it comes to workload and often don’t offer the same advanced traffic management as concentrators.
VPN Concentrator Alternatives
Many businesses have started favoring modern security platforms instead of VPN concentrators because they provide similar (or even better) protection. If you’re not sure that VPN concentrators are right for your business, here are some good alternatives to consider:
- ZTNA (Zero Trust Network Access): A Zero Trust security platform that runs strict checks on every user and device that connects to the company’s network. ZTNA only creates a secure connection between a device and the company app or service it needs. It doesn’t give connected devices access to the rest of the network.
- SD-WAN (Software-Defined Wide Area Networking): Hardware or software that lets companies securely connect branch offices with IPsec encryption. Enterprises have started using SD-WAN as a modern replacement for site-to-site VPN connections, which often rely on VPN concentrators.
- SASE (Secure Access Service Edge): A cloud security solution that combines multiple security tools, like a VPN, firewall, and malware scanning, into one platform. Some companies use it instead of VPN concentrators because it works without on-site hardware, making it more convenient and affordable.
VPN Concentrator vs Other VPN Solutions
The term “VPN concentrator” is sometimes used interchangeably with other VPN terms, causing confusion. Here’s a quick look at how it compares to and differs from other VPN solutions.
VPN Concentrator vs VPN Router
A VPN concentrator gives hundreds or thousands of remote employees secure access to a company’s network. A VPN router gives VPN access to on-site workers instead. All devices that use the router are safely connected to the private network via one secure tunnel. This allows workers in an office to access resources and share data without having to set up a VPN client on their devices.
VPN Concentrator vs VPN Client
A VPN client is software, like an app you download or a program built into your device, that allows you to connect to a VPN. Most VPNs require you to connect via a client, including business networks that use VPN concentrators.
On a work device, an IT administrator usually sets up and configures the VPN client for you. If you’re using a personal device (or a commercial VPN), you download and install the VPN app from an app store or the VPN’s site. After that, you launch the VPN client, log in, and use it to connect to a server or the company’s network.
VPN Concentrator vs Site-to-Site VPN
While a concentrator securely connects individual workers and whole offices to an organization’s VPN, a site-to-site VPN only links two or more offices. For example, it might connect the networks at a company’s headquarters and a branch office so they behave like one unified network. Site-to-site VPNs can still use VPN concentrators to establish and manage connections from multiple sites.
VPN Concentrator vs IPsec VPN
VPN concentrators manage connections and encryption using VPN protocols, and IPsec is one of those protocols. Most enterprise-grade concentrators support IPsec, and IT administrators often pair it with IKEv2 (another protocol) for smoother setup and stronger security.
Secure Your Internal Systems with a VPN Concentrator
For enterprises growing at scale, VPN concentrators offer a secure, flexible solution that enables the entire workforce to access a centralized network. They also add an extra layer of security to workplace systems, encrypting transmitted data to and from users’ devices. However, it’s rare to find them as standalone devices nowadays since many modern security platforms include concentrator functionality built in.
If you don’t employ hundreds of people needing access to the same internal network, you probably don’t need a VPN concentrator. A consumer VPN is more than enough for a small business and the average internet user. CyberGhost VPN offers advanced security and privacy features, ultra-fast servers in 100 countries, and intuitive apps for popular devices. You can try it out completely risk-free, as it backs all long-term purchases with a 45-day money-back guarantee.
FAQ
How does a VPN concentrator work?
A VPN concentrator creates, manages, and terminates large numbers of VPN connections at the same time, allowing remote users to securely connect to a company’s internal network. It also authenticates users, assigns them unique IP addresses, and sends traffic to the right part of the network.
Do I need a VPN concentrator?
If your organization has a large workforce that requires hundreds or thousands of secure remote connections, a VPN concentrator is a good option. If you only need to secure up to a few hundred connections and run a small- to mid-sized business, an enterprise VPN might be a better fit. It provides similar protection but is more affordable. Freelancers and individuals only looking for online privacy should use a consumer-grade VPN.
Where does a VPN concentrator go on the network?
A VPN concentrator is usually located at the edge of a company’s network, behind the perimeter firewall. The firewall acts as the first line of defense between the internet and the private network, filtering out threats before they can reach the VPN concentrator. Once traffic passes the firewall, the concentrator authenticates remote users, creates encrypted connections, and routes traffic inside the network.
What is the benefit of a VPN concentrator?
The main benefit of a VPN concentrator is its ability to handle thousands of encrypted connections at the same time. This helps large companies provide remote workers with secure access to internal networks. A concentrator also authenticates users to make sure no one is accessing the network without authorization.
How much does a VPN concentrator cost?
Most enterprise-grade VPN concentrators cost several thousand dollars, with high-end models reaching $20,000 or more. You might sometimes find concentrators that cost around $200 and $500, but they’re rare and usually outdated.
What is a one-armed VPN concentrator?
A one-armed VPN concentrator is a setup where the concentrator authenticates and encrypts traffic but relies on another device, like a router or firewall, to forward traffic. This approach is cheaper and quicker to set up, but it can make it more complex to manage network rules.
What is the difference between a VPN concentrator and a regular VPN router?
A VPN concentrator creates and manages thousands of secure remote connections to a private network. A VPN router connects on-site devices to the VPN, so the employees working at the office can access network resources.
Is a VPN concentrator hardware or software?
A VPN concentrator can be either hardware or software. Enterprises normally use hardware concentrators for higher performance and compliance reasons. Mid-sized companies generally prefer software concentrators because they’re more affordable and easier to upgrade.
Do small businesses need a VPN concentrator?
Most small businesses don’t need a VPN concentrator unless they have a lot of remote workers. Smaller companies generally use enterprise VPNs, which provide the same level of protection and can handle up to a few hundred connections. For freelancers and individuals, consumer-grade VPNs are usually enough.
How do you configure a VPN concentrator?
That depends on the vendor you’re using. Typically, you add the concentrator to the network, adjust security settings, like encryption and user authentication, and define how the concentrator assigns IP addresses to users. Finally, you test and monitor the concentrator to make sure it works, and then set up its VPN client on employee devices.
What are some leading vendors of VPN concentrators?
Leading VPN concentrator vendors include Cisco Meraki, Juniper Networks, Palo Alto Networks, Fortinet, and NetGear. Most of them offer hardware or software VPN concentrators and also bundle concentrator functionality into their security platforms, like next-gen firewalls.
VPN Concentrator Drawbacks
- High cost and complexity: Enterprise-grade VPN concentrators are often expensive and require skilled IT staff to set up and manage.
- Single point of failure: If the VPN concentrator experiences issues, it affects all active connections unless the organization uses multiple units.
- Limited scalability: Rapid workforce growth can overload smaller concentrators, causing slow speeds or connectivity issues. Scaling requires costly upgrades or additional devices.
Examples of Popular VPN Concentrators
Some of the most popular vendors of VPN concentrators (both standalone and bundled) include:
- Cisco Meraki: Sells hardware devices that double as VPN concentrators (like Meraki MX), offering networking and remote access from one place.
- Juniper Networks: Offers hardware firewalls that act as VPN concentrators, like the SRX5400, which supports IPsec connections.
- NetGate: Has the TNSR software router that can run as a VPN concentrator, supporting both IPsec and WireGuard® setups.
When Do You Need a VPN Concentrator?
VPN concentrators are usually chosen when an organization’s remote workforce grows significantly. They’re useful if you need to manage thousands of VPN connections or if your network has more traffic than a standard VPN server can handle.
Up to a few hundred connections, though, you can use a regular enterprise VPN instead. They’re often more affordable because they’re more limited when it comes to workload and often don’t offer the same advanced traffic management as concentrators.
VPN Concentrator Alternatives
Many businesses have started favoring modern security platforms instead of VPN concentrators because they provide similar (or even better) protection. If you’re not sure that VPN concentrators are right for your business, here are some good alternatives to consider:
- ZTNA (Zero Trust Network Access): A Zero Trust security platform that runs strict checks on every user and device that connects to the company’s network. ZTNA only creates a secure connection between a device and the company app or service it needs. It doesn’t give connected devices access to the rest of the network.
- SD-WAN (Software-Defined Wide Area Networking): Hardware or software that lets companies securely connect branch offices with IPsec encryption. Enterprises have started using SD-WAN as a modern replacement for site-to-site VPN connections, which often rely on VPN concentrators.
- SASE (Secure Access Service Edge): A cloud security solution that combines multiple security tools, like a VPN, firewall, and malware scanning, into one platform. Some companies use it instead of VPN concentrators because it works without on-site hardware, making it more convenient and affordable.
VPN Concentrator vs Other VPN Solutions
The term “VPN concentrator” is sometimes used interchangeably with other VPN terms, causing confusion. Here’s a quick look at how it compares to and differs from other VPN solutions.
VPN Concentrator vs VPN Router
A VPN concentrator gives hundreds or thousands of remote employees secure access to a company’s network. A VPN router gives VPN access to on-site workers instead. All devices that use the router are safely connected to the private network via one secure tunnel. This allows workers in an office to access resources and share data without having to set up a VPN client on their devices.
VPN Concentrator vs VPN Client
A VPN client is software, like an app you download or a program built into your device, that allows you to connect to a VPN. Most VPNs require you to connect via a client, including business networks that use VPN concentrators.
On a work device, an IT administrator usually sets up and configures the VPN client for you. If you’re using a personal device (or a commercial VPN), you download and install the VPN app from an app store or the VPN’s site. After that, you launch the VPN client, log in, and use it to connect to a server or the company’s network.
VPN Concentrator vs Site-to-Site VPN
While a concentrator securely connects individual workers and whole offices to an organization’s VPN, a site-to-site VPN only links two or more offices. For example, it might connect the networks at a company’s headquarters and a branch office so they behave like one unified network. Site-to-site VPNs can still use VPN concentrators to establish and manage connections from multiple sites.
VPN Concentrator vs IPsec VPN
VPN concentrators manage connections and encryption using VPN protocols, and IPsec is one of those protocols. Most enterprise-grade concentrators support IPsec, and IT administrators often pair it with IKEv2 (another protocol) for smoother setup and stronger security.
Secure Your Internal Systems with a VPN Concentrator
For enterprises growing at scale, VPN concentrators offer a secure, flexible solution that enables the entire workforce to access a centralized network. They also add an extra layer of security to workplace systems, encrypting transmitted data to and from users’ devices. However, it’s rare to find them as standalone devices nowadays since many modern security platforms include concentrator functionality built in.
If you don’t employ hundreds of people needing access to the same internal network, you probably don’t need a VPN concentrator. A consumer VPN is more than enough for a small business and the average internet user. CyberGhost VPN offers advanced security and privacy features, ultra-fast servers in 100 countries, and intuitive apps for popular devices. You can try it out completely risk-free, as it backs all long-term purchases with a 45-day money-back guarantee.
FAQ
How does a VPN concentrator work?
A VPN concentrator creates, manages, and terminates large numbers of VPN connections at the same time, allowing remote users to securely connect to a company’s internal network. It also authenticates users, assigns them unique IP addresses, and sends traffic to the right part of the network.
Do I need a VPN concentrator?
If your organization has a large workforce that requires hundreds or thousands of secure remote connections, a VPN concentrator is a good option. If you only need to secure up to a few hundred connections and run a small- to mid-sized business, an enterprise VPN might be a better fit. It provides similar protection but is more affordable. Freelancers and individuals only looking for online privacy should use a consumer-grade VPN.
Where does a VPN concentrator go on the network?
A VPN concentrator is usually located at the edge of a company’s network, behind the perimeter firewall. The firewall acts as the first line of defense between the internet and the private network, filtering out threats before they can reach the VPN concentrator. Once traffic passes the firewall, the concentrator authenticates remote users, creates encrypted connections, and routes traffic inside the network.
What is the benefit of a VPN concentrator?
The main benefit of a VPN concentrator is its ability to handle thousands of encrypted connections at the same time. This helps large companies provide remote workers with secure access to internal networks. A concentrator also authenticates users to make sure no one is accessing the network without authorization.
How much does a VPN concentrator cost?
Most enterprise-grade VPN concentrators cost several thousand dollars, with high-end models reaching $20,000 or more. You might sometimes find concentrators that cost around $200 and $500, but they’re rare and usually outdated.
What is a one-armed VPN concentrator?
A one-armed VPN concentrator is a setup where the concentrator authenticates and encrypts traffic but relies on another device, like a router or firewall, to forward traffic. This approach is cheaper and quicker to set up, but it can make it more complex to manage network rules.
What is the difference between a VPN concentrator and a regular VPN router?
A VPN concentrator creates and manages thousands of secure remote connections to a private network. A VPN router connects on-site devices to the VPN, so the employees working at the office can access network resources.
Is a VPN concentrator hardware or software?
A VPN concentrator can be either hardware or software. Enterprises normally use hardware concentrators for higher performance and compliance reasons. Mid-sized companies generally prefer software concentrators because they’re more affordable and easier to upgrade.
Do small businesses need a VPN concentrator?
Most small businesses don’t need a VPN concentrator unless they have a lot of remote workers. Smaller companies generally use enterprise VPNs, which provide the same level of protection and can handle up to a few hundred connections. For freelancers and individuals, consumer-grade VPNs are usually enough.
How do you configure a VPN concentrator?
That depends on the vendor you’re using. Typically, you add the concentrator to the network, adjust security settings, like encryption and user authentication, and define how the concentrator assigns IP addresses to users. Finally, you test and monitor the concentrator to make sure it works, and then set up its VPN client on employee devices.
What are some leading vendors of VPN concentrators?
Leading VPN concentrator vendors include Cisco Meraki, Juniper Networks, Palo Alto Networks, Fortinet, and NetGear. Most of them offer hardware or software VPN concentrators and also bundle concentrator functionality into their security platforms, like next-gen firewalls.


Leave a comment