Curiouser and curiouser…
Could Tor be the key to the wicked wonderland of the dark web?
Tor may be your portal to the internet’s furthest reaches, but you need your wits about you and a couple of extra items in your rucksack before you attempt such a perilous journey.
If you take the proper precautions and think before you leap, the Tor browser can take you anywhere you’d like to go.
In this guide, I’ll answer every question you may have about Tor. I’ll also show you how to travel safely with Tor, so you emerge from the rabbit hole with your security and privacy intact.
Tor Safety Precautions
- Download the official Tor browser.
- Use a robust antivirus.
- Pair with a reliable VPN, like CyberGhost VPN.
- Think before you click.
What Is Tor?
Tor (the Onion Router) is a long-standing privacy pioneer. Tor uses several encryptions, tunneling, and IP cloaking layers (hence the onion reference) to protect your privacy on the web.
The global Tor community involves thousands of volunteers who believe “everyone has the right to enjoy private access to an uncensored web”. The Tor Project has brought the world privacy-focused technologies, including the popular Tor Browser.
The Tor browser is free and open-source software running on Mozilla’s Firefox browser. It lets you search privately and visit any website you like. It’s also the only way to access the dark web.
Tor is a web browser much like Google Chrome and Microsoft Edge, but with one major difference. Tor makes it extremely difficult for anyone to track your browsing activity.
How, you ask? Well, Tor makes you look like any other user, so it’s difficult for trackers to ‘fingerprint’ you based on your browser and device information. Tor then encrypts your online traffic and reroutes it through several random servers around the world. It’s like how taking a zigzaggy route might help you lose anyone trailing you on the road.
When you connect to Tor’s network, anyone tracking your Internet connection can’t see what sites you visit, and the sites can’t track your physical location. Tor also has digital platforms, allowing you to share files and communicate without exposing your real IP address or location.
What Is Tor?
People use the Tor browser to access geo-restricted content, bypass censorship, and visit the dark web. Organizations, journalists, whistleblowers, and anyone who wants to keep their internet activity private rely on Tor to communicate online in complete confidence.
In countries with restrictions on free speech, activists like Edward Snowden use Tor to protect their information, sources, and identities. Tor helps people living under repressive regimes to bypass online censorship and gain access to blocked sites from anywhere in the world. For example, during the 2010 Arab Spring, Tor protected people’s identity online and gave them access to critical resources, social media, and blocked news websites.
Ordinary people who want to avoid someone watching their online activity browse the internet using Tor. Tor lets you post on websites without sharing your location, making it ideal for improving your privacy when discussing sensitive topics. Tor has also made it possible for domestic abuse and rape survivors, or people with illnesses, to get the support they need without exposing themselves to danger.
Developers looking to create more secure apps incorporate Tor since it offers built-in privacy features.
It’s important to remember this protection only applies to Tor browser traffic. It doesn’t protect any other application on your system (including other browsers), so you still need a good VPN when using Tor.
Is Tor Safe?
While Tor improves your online privacy, it’s certainly not sniper-proof. You still need to watch out for:
Surveillance Agencies
In the past, the FBI, CIA, and NSA have all been able to crack Tor’s security and expose Tor users’ identities and activities. To their credit, Tor’s people constantly work to patch up any weaknesses, but mistakes do happen.
Google’s All-Seeing Eye
As Tor works with the Mozilla Firefox browser, and Google is the default search engine on Firefox (and generates 95% of Mozilla’s revenue) you could still have cause to fear Google tracking you through your account and search activity. If so, log out of your Google account and switch to a more private search engine like DuckDuckGo or Startpage or protect yourself with other measures like using a VPN.
Snitching ISPs
Your ISP is another problem. Some ISPs stop your connection when they see you’re using Tor. They could even decide to report you to law enforcement. Several court cases have seen individual Tor users charged with engaging in illegal activities on the dark web. This means the law enforcement still has ways and means to get their hands on your data–even if you use Tor. Use a VPN to prevent your ISP from knowing you are using Tor and reporting you.
Cybercrooks
Tor won’t stop cybercriminals, viruses, and other malware from hiding in the sites you visit–especially on the dark web. You still need to use a good antivirus software and think before you click.
Bad Nodes
Another Tor risk factor is a bad exit node, where the final node in the relay exposes your activity and IP. Malicious server hosts could record your data to sell it or use it to blackmail you. Surveillance agencies also run a number of Tor exit nodes to keep tabs on users.
You can protect yourself against these risks with CyberGhost VPN and a decent antivirus software.
6 Things to Remember About Tor
Now that we’ve covered the basics, here are 6 things you need to understand about Tor.
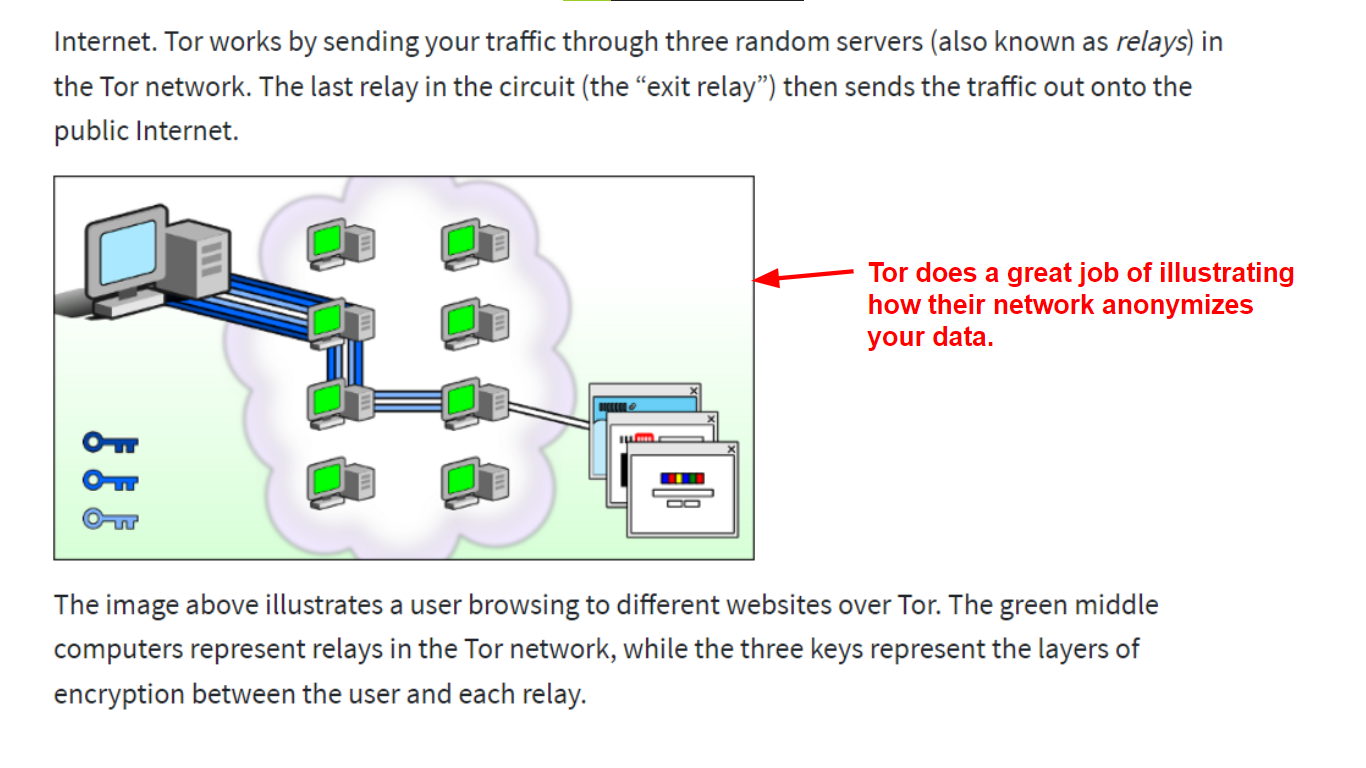
1. Tor’s Law of Threes
Tor Browser hides your identity and protects your privacy using 3 encryption layers and 3 IP address cloaking levels. Your IP address changes at every node as your traffic hops to different servers around the world.
At each stop, another encryption layer is peeled off (like an onion), making it difficult for websites to trace your online activity back to you.
2. Multilayered Security
Tor has more features designed to protect your online privacy than any other browser.
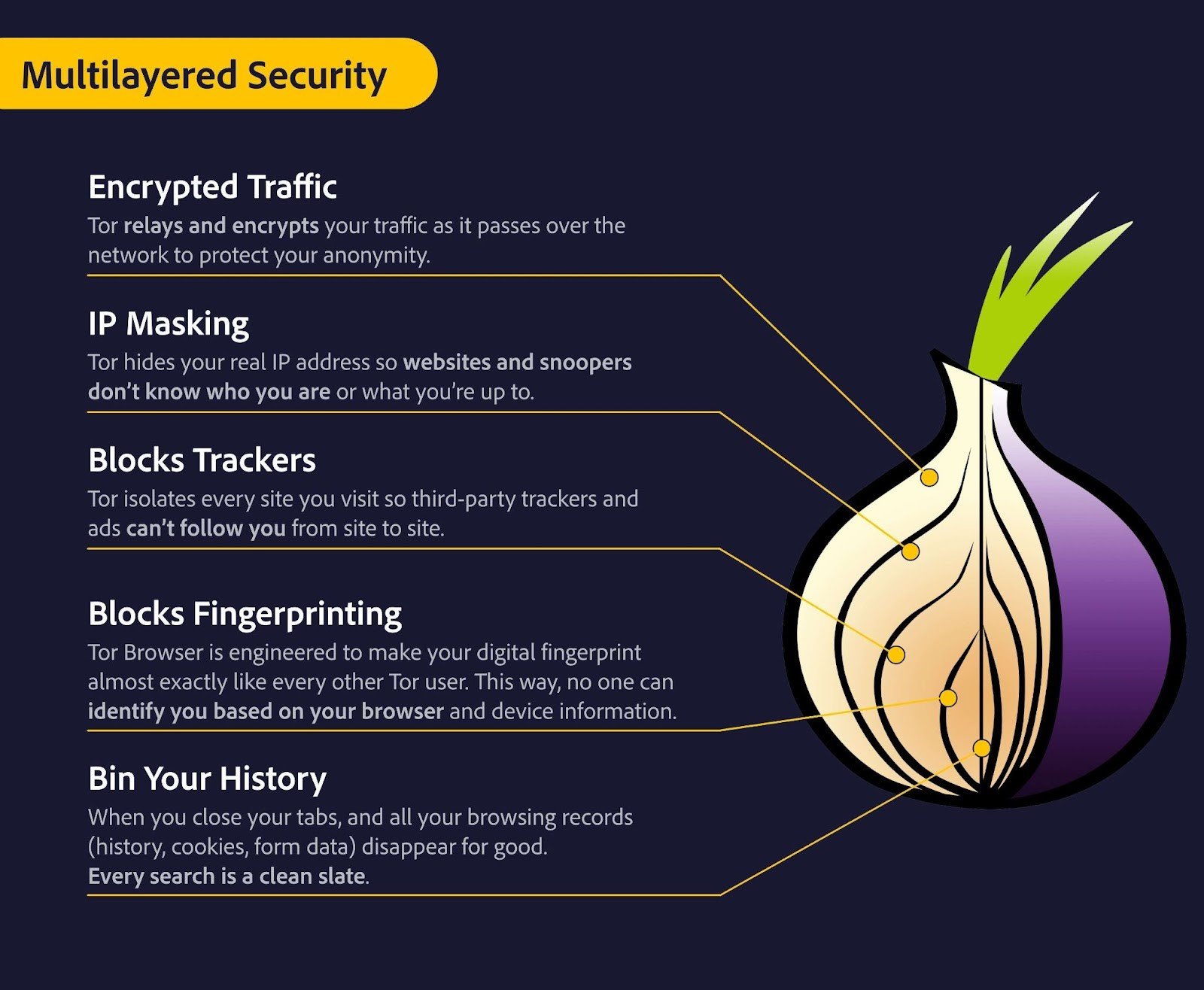
Encrypted Traffic
Tor relays and encrypts your traffic as it passes over the network to protect your identity.
IP Masking
Tor hides your real IP address so websites and snoopers don’t know who you are or what you’re up to.
Blocks Trackers
Tor isolates every site you visit so third-party trackers and ads can’t follow you from site to site.
Blocks Fingerprinting
Tor Browser is engineered to make your digital fingerprint almost exactly like every other Tor user. This way, no one can identify you based on your browser and device information.
Bin Your History
When you close your tabs, and all your browsing records (history, cookies, form data) disappear for good. Every search is a clean slate.
3. Tor’s Free
It’s easy to be suspicious of Tor Browser because it’s free. If it’s free, you’re the product, right? Tor is also partially US government-funded, which will raise some eyebrows. Tor was originally used as a tool to allow for anonymous communication within the US Navy. It has some people fearing the US government and if it still has secret backdoor access to Tor. If this were the case, volunteers who analyze the open-source code would surely pick it up.
After doing some digging myself, I’m convinced Tor is kosher. Though Tor started as a government-run project, today it’s entirely volunteer-operated and suitably transparent. I’d go as far as encouraging you to make a donation or volunteer to run a server for Tor to remain free.
4. Tor’s Legal (in Most Places)
Tor is perfectly legal in most Western countries. It only becomes illegal when you use it to access sites to trade in illegal materials. Though, you can still get flagged for dodgy activity if someone like your ISP spots you using it. It’s important to protect yourself by connecting to a VPN before using Tor. Enjoy safe and censorship-free browsing with CyberGhost VPN.
5. Tor can be Slow
Be aware that Tor Browser can run a bit slower than other browsers. That’s because your traffic, along with a million others’ traffic, has to pass through several nodes in Tor’s limited server network. It bounces back and forth between continents before it gets to its destination. Nevertheless, Tor’s developers claim it’s getting faster every day, and can only improve the more users donate servers.
6. Tor has a Dark Side
Tor has a bad reputation for being allied with the dark side because it allows anyone to access the dark web. This is the internet’s unregulated “Wild West” where other popular browsers and search engines fear to tread.
Falling within the bigger deep web, the dark web is home to every imaginable illegal activity and covert communication. The dark web isn’t all cloak and daggers though. It can be a haven for journalists, whistleblowers, and ordinary citizens. They can communicate free from censorship, surveillance, and prosecution.
If you’re tempted to take a walk on the wild side, you’ll need Tor as your trusty guard dog. Just watch your step. The dark web can be hazardous for you and your device.
Remember to:
-
- ✔️ Get out the second you suspect a site is trying to infect your computer with malware.
- ✔️ Steer clear of sites involved in illegal activities.
- ✔️ Keep an eye open for cybercriminals, they’re behind every bush in the dark web
- ✔️ Use a VPN to fully protect your privacy and keep network attacks at bay.
Pro tip: Travel safely on the dark web with CyberGhost VPN. We encrypt your internet traffic and reroute it through our private servers. This way, your data is wrapped in an invisibility cloak and kept safe from all prying eyes. We also shield you from many other cyber threats lurking on the dark web.
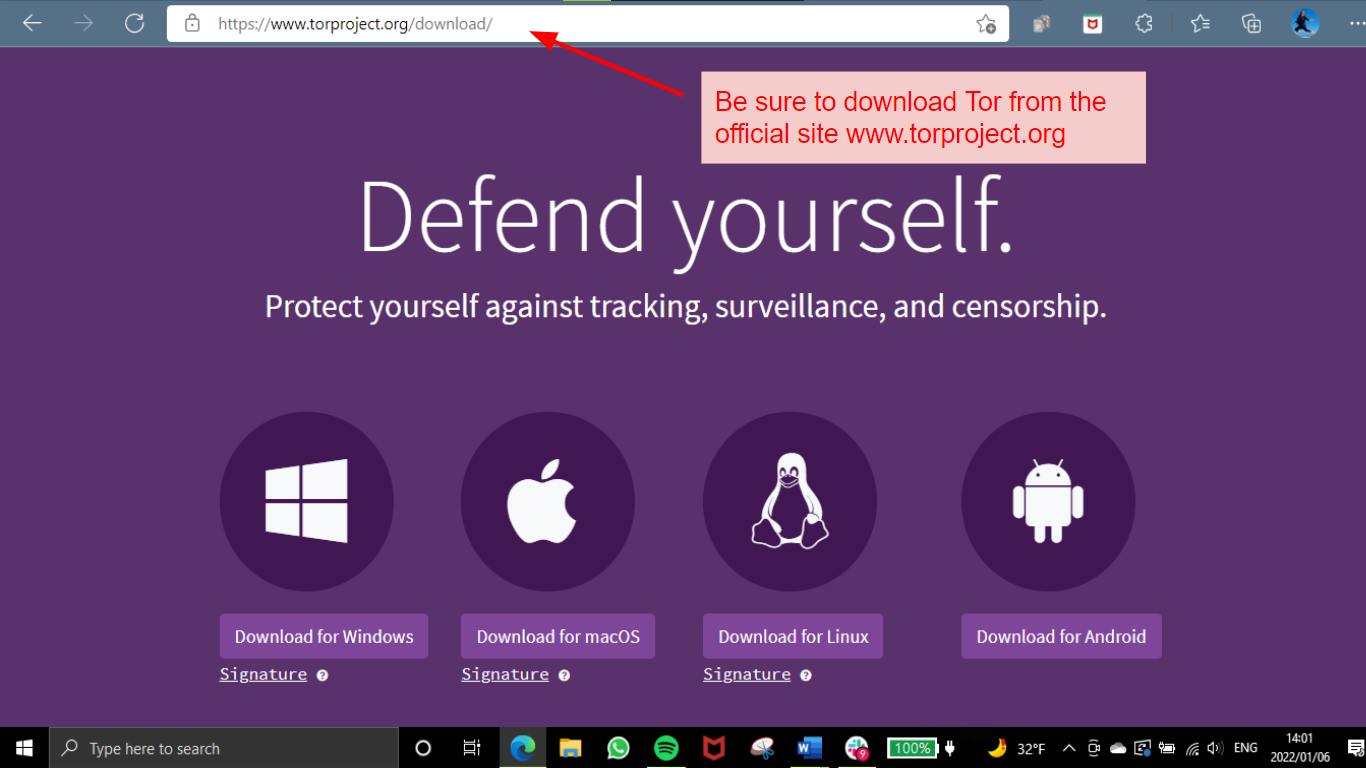
How to Download the Tor Browser
Tor browser is available on Microsoft Windows, macOS, Linux, and Android*. It’s easy to find and download the current version for your operating system from the official Tor site.
The installation process for Tor Browser works just like any other software. Once installed, the browser will open automatically and you can use it like any other web browser.
*Got an iPhone? Tor won’t work for you, but you can always try the Onion Browser app. This Tor alternative is open source, uses Tor routing, and people who work closely with the Tor Project developed it.
How to Explore with Tor Safely
Don’t Overshare
When you visit a website using Tor, the site doesn’t know who or where you are. Don’t fill in forms or sign in anywhere or you’ll give the game away. If you submit your name, email, phone number, or any other personal information, you’re no longer anonymous to the site.
Adjust Tor Settings
For maximum privacy and security, turn the settings up to ‘Safest.’ This will keep you safe if Tor gets hacked. It also helps to reduce online tracking to almost zero.
Some websites won’t work as well, but it’s the price you pay for privacy these days.
Update Your Antivirus
Even with your safety settings at their highest, bizarre things can and do happen on the dark web. You need a decent antivirus program to protect yourself and always make sure it’s up to date. The CyberGhost Security Suite comes with a cutting-edge antivirus.
Use HTTPS websites
Tor encrypts your traffic to and within the Tor network, but not from the exit node to the final destination site. While Tor Browser uses HTTPS Everywhere to force encryption, not all sites support it. You should still keep an eye on the URL bar to ensure the websites you visit are safe. Check if they have a padlock or onion icon in the address bar, start with https://, and the domain name looks correct.
Think Before You Click
Avoid clicking on links you don’t know. This is your best defense against the scams, malware, and viruses which dominate the dark web.
Use a VPN
Cover yourself with extra protection layers and use a VPN with Tor. A VPN encrypts and protects your traffic, even after it leaves the Tor network. This way, malicious exit nodes can’t expose you, and other third parties can’t track your location. It also prevents your ISP or anyone else from seeing what you’re up to. This is crucial in countries where just using Tor raises a flag.
A quality VPN like CyberGhost keeps all your online activity hidden from ISPs, cybercriminals, governments, and anyone else lurking in the cyber bushes.
How to Use Tor Browser with CyberGhost VPN
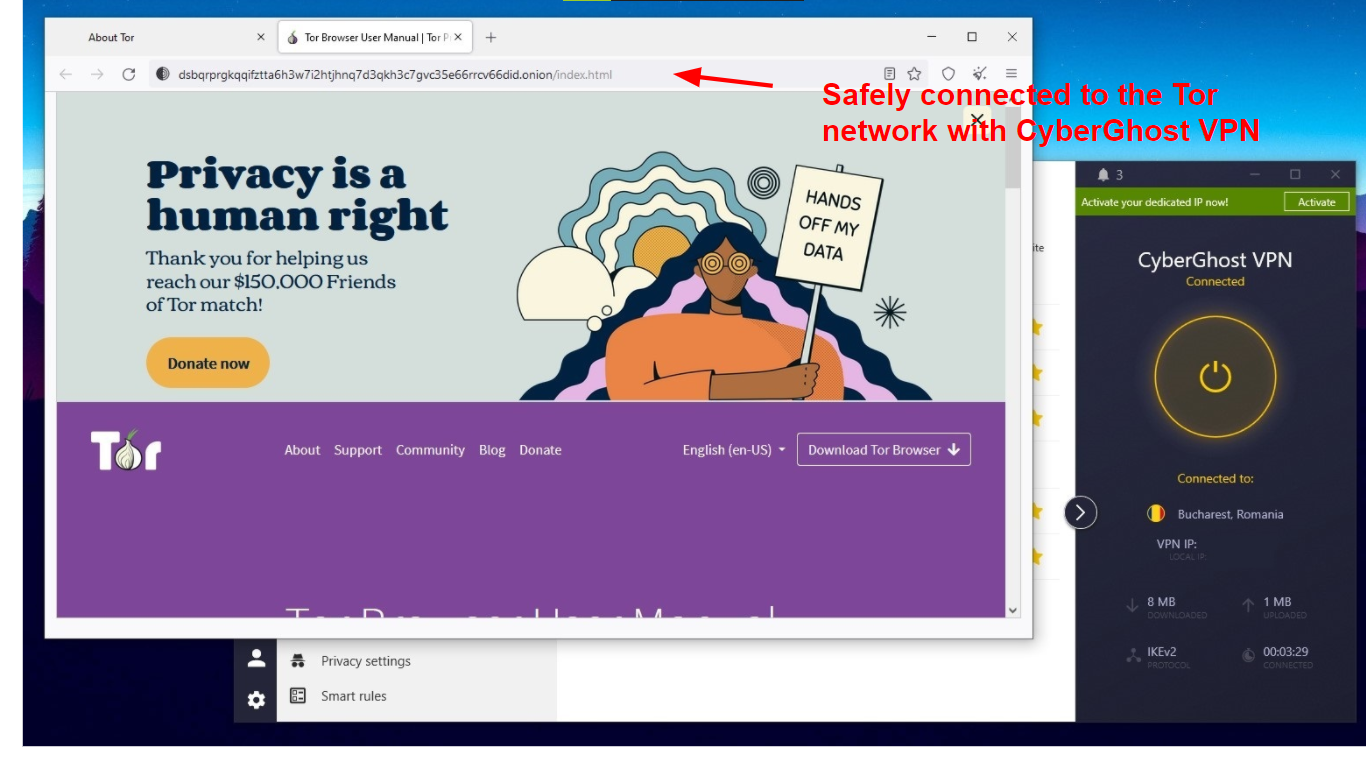
Tor-over-VPN
This is the most common way to use Tor with a VPN. First you connect to your VPN, then open Tor. Your VPN encrypts your entire connection and routes your traffic through its secure servers before sending any of it through Tor. This way, your ISP can’t see you’re using Tor and all of your data is private, not just your browsing data. Here’s how to do it:
- Subscribe to CyberGhost VPN. It’s fast & easy!
- Download and install the app on any device.
- Select a server in your desired location.
- Open Tor Browser and enjoy secure browsing!
Pro tip: For optimal speeds, connect to a server close to your physical location.
VPN-over-Tor
You could also opt for the VPN-over-Tor method, but currently this setup is not possible with CyberGhost, or with most VPNs for that matter. The reason for this is that it’s very complicated to configure and doesn’t add that much security over the above method.
For interest’s sake, though, here’s how VPN-over-Tor works:
First, you connect to the Tor network through the Tor browser, and only then activate your VPN. This reconnects you through the VPN’s adapter and network, which means your exit node will be an IP from the VPN network, not a Tor IP. As such, you don’t get access to the exclusive resources available to Tor users, such as access to the dark web.
To enable VPN-over-Tor, your VPN must have an active onion domain (VPN servers hosted in the Tor network) to work as intended. So, unless your VPN provider has a feature to enable VPN-over-Tor, this is not achievable.
It’s important to note that VPN-over-Tor is not as safe as the first option (Tor-over-VPN) and even Tor itself doesn’t recommend it. The main reason is because this setup exposes your Tor use to your ISP.
The only reason to try this setup is if you don’t trust your VPN with your secrets. In that case, my best advice would be to switch to a trustworthy VPN service like CyberGhost.
Here at CyberGhost, your privacy is our priority. We follow a strict No-Logs policy, which means we never collect, store or share any or your data. Based in Romania, we’re outside of any surveillance alliances and can happily ignore any legal requests to hand over your data. Just take a look at our recent Transparency Report to see how many requests we’ve declined – all of them!
For improved online security, rather go with the first (Tor-over-VPN) setup and use a trustworthy VPN like CyberGhost.
Why Choose CyberGhost VPN
Easy to Use
CyberGhost is a beginner-friendly, easy-to-use VPN with no fuss. Connect in a click to one of our 9000+ secure servers in 90+ countries and enjoy a high-speed ride to a restriction-free world wide web.
Take back your internet freedom, risk-free with our 45-day money-back guarantee.
Military-Grade Encryption
We’ll also hide your private data behind unbreakable AES 256-bit encryption before you connect to Tor. Your ISPs, search engine, Wi-Fi router, bad exit nodes, proxy servers, surveillance agencies, and cybercriminals won’t be able to touch you.
Leak-Proof
CyberGhost VPN shields your digital identity with DNS and IP leak protection. This stops your device from accidentally leaking your DNS requests or IP address, despite having a VPN on. We also have an automatic Kill Switch to protect you if your connection ever drops unexpectedly.
No Logs
Since we’re based in Romania, we’re exempt from any surveillance alliances and aren’t obligated to hand your data over to any authorities. We also follow a strict No-Logs policy, meaning we don’t monitor or record your activities.
A VPN for Every Device
If you can run Tor on your device, you can run CyberGhost VPN as well. We have dedicated apps for Android, Windows, macOS, and even iOS devices. You could even cover all your devices in one go with CyberGhost VPN on your router. However you want it, you’ve got it in a single CyberGhost VPN subscription, protecting up to 7 devices simultaneously.
Final Thoughts
Tor is without a doubt a godsend for privacy advocates everywhere. It’s a powerful private browser that lets you surf the web with a higher degree of security.
That said, you need a few more privacy essentials on your side to be safe online. Along with a powerful antivirus software, you need a quality VPN like CyberGhost. We’ll hide your Tor usage from your ISP (and anyone else spying on you) and improve your online privacy.
Download CyberGhost VPN now and find out why millions of Tor-ists never step foot into the dark web, or anywhere else online without additional protection.
FAQ
It’s highly unlikely for someone to track you on the Tor network. That said, ISPs and some governments monitor the Tor network’s major entry and exit nodes to block and spy on individual users. Any apps or sites you access without the Tor browser could expose you to tracking.
CyberGhost VPN will keep you invisible with end-to-end, system-wide military-grade encryption, no matter what application you use.
Yes, Tor is legal in most countries, but it does host illegal content. Simply connecting to Tor can make your ISP suspicious. Use a VPN like CyberGhost along with Tor to protect your digital identity and hide all your online activity from your ISP and others, including the fact you’re connecting to Tor. That way, you avoid raising any alarms.
Yes, The Tor Browser is free to download and use. It’s also free to distribute as long as you follow the Tor Project’s license. Watch out for fake sites trying to charge you to download Tor. Remember to first connect to a reliable VPN like CyberGhost before using Tor to stay safe online. Find out what others are saying about CyberGhost VPN.
Tor works on Android but not on iOS. You can use an app called the Onion Browser. It’s open-source and uses Tor routing, and the Tor Project recommends it. Just like Tor, Onion Browser is far safer when combined with CyberGhost VPN. You can get our iOS app here.
Tor is slower than your usual browser because it encrypts your traffic and relays it through several nodes before it reaches its final destination. This can cause some bottlenecks and latency issues. That’s why you’ll need a super-fast VPN like CyberGhost to browse with Tor without causing any further holdups.
A VPN can patch up some of Tor’s privacy gaps.
For example, even if Tor encrypts and anonymizes traffic running through its network, malicious actors could intercept your data at the entry or exit nodes to reveal who you are and what you’re doing.
A VPN prevents your ISP from seeing you’re connected to Tor to avoid any suspicion. With a good VPN like CyberGhost, you’ll also enjoy unlimited bandwidth, advanced AES-256-bit encryption, and automatic Wi-Fi protection on up to 7 devices simultaneously, all backed by our 45-day money-back guarantee.
Tor-over-VPN is easier and safer.
The Tor-over-VPN approach means you first connect to your VPN, then open Tor just like you’d open any other browser. The VPN encrypts your entire connection and routes your traffic through its secure servers before connecting to Tor.
It protects all your traffic and your ISP (or anyone else) can’t see you’re using Tor. The only drawback is your VPN can’t protect you from malicious exit nodes since your traffic becomes unencrypted once it reaches its destination.
If you don’t trust your VPN provider, you may want to go the VPN-over-Tor route. With the VPN-over-Tor approach, you first connect to Tor, then connect through your VPN. This method requires some manual configuration and an onion domain from your VPN. Most VPNs don’t have one, though.
Note: Tor’s developers don’t recommend this method and very few VPNs can be configured to work with Tor that way around.
Need help using Tor with CyberGhost VPN? Reach out to our friendly customer support team. They’re available 24/7 via email or live chat.
No, DuckDuckGo is a private search engine and the default search engine on Tor. It offers more security and privacy than most search engines because it doesn’t collect your data or track your searches. It also doesn’t personalize your search results based on previous searches.
Not sure what search engine to use? Here’s a run-down of the 10 best private search engines.
The deep web includes all websites you can’t access through a regular search engine. That means dark web sites, but also private sites like corporate intranets, databases, online banking platforms, and other sites you can only access with login credentials.
Within the deep web, you get the dark web–the part you can’t access without Tor. Dark web sites don’t have URLs ending in .com or .org, but rather .onion, which is why they’re called onion sites. Many organizations have their own onion sites to protect their users’ privacy and help get around censorship. The dark web teems with illegal activities, but it’s also a haven for free speech and dissent.
Download CyberGhost VPN and stay safe on the dark web. Give our powerful VPN a try, risk-free with our 45-day money-back guarantee.
You could, but we don’t recommend it. You have no guarantee a free VPN offers proper privacy protection, won’t log and sell your data to third parties, or can give you a decent connection. For only $2.15 a month for our 3-year plan, CyberGhost can set you up with an affordable and reliable VPN to keep you protected on all your devices.



Leave a comment