If you haven’t read my first piece on the rise of the Lapsus$ gang, you might want to head there first. This is an update on events connected to Lapsus$ since that article was published.
Since its major debut on the scene a few weeks ago, newbie hacking group Lapsus$ continues to make waves by targeting big names. The cybercrime syndicate has now added Microsoft, Okta, and Globant to its list of victims.
Notoriety comes at a cost, though, in the form of increased scrutiny by cybersecurity officials and from authorities. Lapsus$ possibly learned that lesson the hard way, as UK authorities reportedly arrested 7 Lapsus$ members at the end of March. Here’s the latest on everything Lapsus$ has been up to since after the Ubisoft hack news broke.
A Short Vacation
Flaunting privacy laws and targeting massive corporations is all fun and games until the authorities catch up with you. That day of reckoning came for (at least some) Lapsus$ members when the UK police arrested 7 suspected hackers, aged between 16 and 21. The police mentioned that a potential connection to Lapsus$ sparked the arrest.
A 16- and 17-year-old have since appeared in court in London and were charged with various offenses relating to unauthorized access. At that time, Bloomberg also reported that cybersecurity researchers possibly discovered the identity of the gang’s ringleader — a 16-year-old Oxford teen.
Lapsus$ took to its Telegram channel to deny that any of its members had been arrested. Yet shortly after, the group also posted that some of its members were going on a vacation, then went silent for a few days.
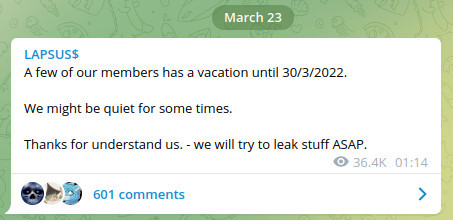
No one knows how large the Lapsus$ gang is or whether they’re all based in the same country. It’s more likely the group is spread out, but these UK arrests could still be a big blow to the syndicate. The FBI has reportedly requested that UK authorities share information about the arrests. That could also broaden the investigation and lead to more captures in the future.
The Lapsus$ Target List Keeps Growing
Despite already having bragging rights about high-profile victims like Nvidia, Ubisoft, and Samsung, Lapsus$ gets more brazen by the day. The group continues to target massive companies, especially in the technology sector. Here are the most prominent companies Lapsus$ recently hacked:
January 2022: The Okta Hack
Back in January, Okta became aware that the account of a customer support engineer from one of its third-party vendors, Sitel, was compromised. Apparently, someone had gotten access to the computer via a Remote Desktop takeover. News of the breach only came to light after Lapsus$ posted screenshots of the stolen data on their Telegram channel in March.

Okta didn’t release any information about the breach until after that announcement — even though the company had known for two months. After the hackers took to social media, Okta released a statement saying the breach had been contained to that device. The company also stated the damage was “minimal”, as only about 2.5% of its customers’ data may have been viewed or acted upon.
Shortly after, security researcher Bill Demirkapi got access to a report from security firm Mandiant, which investigated the breach. Bill tweeted a detailed explanation of the tactics Lapsus$ used to access Okta and also asked Okta about its apparent inaction.
He also indicated that the situation might be worse than Okta led on, as it seems admin credentials were compromised in the breach as well. Okta did not respond at the time of writing.
March 2022: The Microsoft Hack
On Monday, March 21st, Lapsus$ posted a 10GB compressed file (around 37GB uncompressed) filled with data stolen from Microsoft. That archive reportedly contains data related to Microsoft’s Bing search engine and Bing Maps, as well as source code for Cortana. The gang also announced that it was in the process of stealing more data.
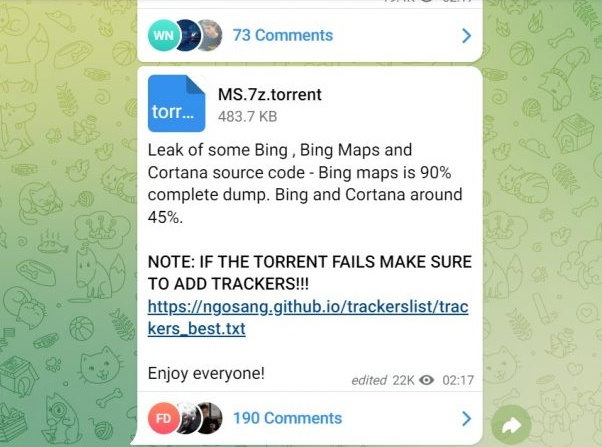
A day later, Microsoft confirmed that an employee’s account has been breached. Apparently, the incident provided Lapsus$ with limited access to company data. Microsoft also said Lapsus$ gained access to some source code, but no customer data. “Microsoft doesn’t rely on the secrecy of code as a security measure and viewing source code doesn’t lead to elevated risk,” the company said.
Lapsus$ wasn’t able to finish its expedition into Microsoft’s files either, as the company got wind of the hack and blocked further access. “Our team was already investigating the compromised account based on threat intelligence when the actor publicly disclosed their intrusion. This escalated our action, allowing our team to intervene and interrupt the actor mid-operation,” a Microsoft spokesperson said.
March 2022: The Globant Hack
After their return from “vacation”, Lapsus$ announced they had infiltrated Globant, a software development consultancy with clients like Apple, Slack, and Facebook. Lapsus$ posted a list of stolen credentials (it’s unclear whether this included client passwords) and 70GB of internal data.
Lapsus$ lambasted the company’s poor security practices and posted a list of all of Globant’s DevOps admin passwords. Many of these are weak and reused passwords that are easily guessable.
Globant confirmed the hack but said the damage looks to be minimal so far. “The information that was accessed was limited to certain source code and project-related documentation for a very limited number of clients. To date, we have not found any evidence that other areas of our infrastructure systems or those of our clients were affected,” a spokesperson said.
Ingenious Hacking or Lackluster Security?
In my previous article, I highlighted security researchers’ opinions of the Lapsus$ group. Researchers mainly speculated on the group’s amateurish appearance, based on its communication tactics and group infighting. That has remained unchanged, with some companies even reporting the hackers are joining company Zoom calls to mock employees during meetings.
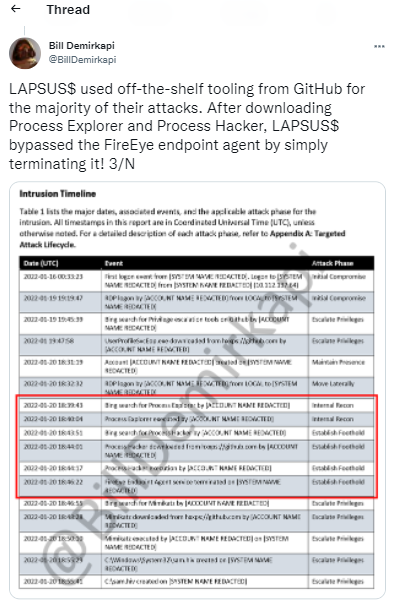
It seems that immaturity is also reflected in the group’s exploitation tactics. They employ simplistic methods and use readily accessible tools to access company systems.
In his tweets, security researcher Bill Demirkapi highlighted that Lapsus$ used “off-the-shelf tooling from GitHub for the majority of their attacks.” The group also mainly uses phishing techniques to gain access to an employee’s device and then steals any data it can find.
In a recent blog post, Microsoft described Lapsus$ (which it’s named DEV-0537): “Unlike most activity groups that stay under the radar, DEV-0537 doesn’t seem to cover its tracks. They go as far as announcing their attacks on social media or advertising their intent to buy credentials from employees of target organizations.”
The group’s habit of publicly sharing their exploits has hurt them in the past. For example, when they posted about their ongoing Microsoft attack. Microsoft got wind of the act and cut the group off mid-access. If Lapsus$ hadn’t bragged about the hack on Telegram, they might have been able to finish their download.
A Hard Lesson (For Everyone)
Regardless of the group’s amateur tactics and brazen attention-seeking, Lapsus$ has still managed to infiltrate a long list of high-profile companies.
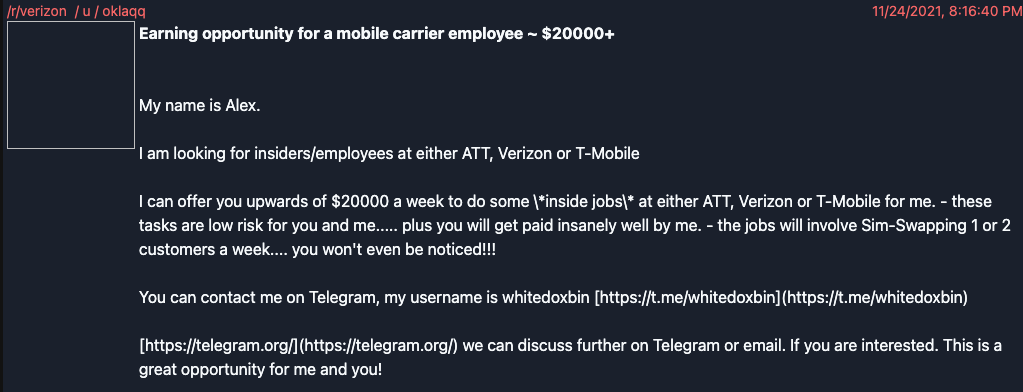
Lapsus$’s success may actually lay in the simplicity of their approach. They openly target people at companies or third-party vendors that can provide access to the data they want. Some members have even gone so far as to advertise on Reddit.
At the end of the day, this is a lesson of 3 parts:
1. Cyberattack tools are easy to come by.
The internet is full of websites where hackers (both white-hat and black-hat) openly share trade techniques and tools. Even young and relatively inexperienced people can start hacking into systems with these (often free) tools.
2. Companies are still vulnerable to cyberattacks, especially due to human error.
Security officers have known for a long time that a system is only as secure as its weakest link, which is most often people. This is an important lesson for companies about their own internal security as well as in relation to the partnerships and tools they use. If they’re willing to listen.
The revelations we’ve learned here aren’t exactly new. It’s just that companies and employees still don’t follow recommended security practices, despite knowing better.

3. Data security is still complicated.
Okta both hid the breach from its customers and then lied about the severity of that breach. You can’t always keep companies from collecting some of your data, but you can improve your online privacy.
It’s unlikely Lapsus$ has learned their lesson after the recent arrests, seeing as they’re active on their Telegram channel again. You can’t trust that companies will learn their lesson and finally guard your data better either. That means it’s up to you to take this final lesson to heart.
Guard your data by being selective about the information you hand out online. Tools like two-factor authentication and VPNs for additional security also go a long way.
Keeping an Eye on Lapsus$
It’s hard to believe, but it’s only been a month since Lapsus$ first started dominating the news with their exploits. Since then, the syndicate has embarrassed a sizable list of massive companies and somehow continues to be incredibly successful at their exploits.
At the pace this group is going, we’ll likely see more big names added to their list of victims soon. Whether you’re the owner of a company, an employee, or a customer, Lapsus$ is teaching everyone that we’re not doing enough to protect our data.
CyberGhost VPN protects your privacy by encrypting your online traffic, turning it into an unreadable mess. When you connect to a VPN server, your IP address changes to the server’s IP. That also prevents third parties from tracking you across the web.



Leave a comment