As your network grows, so can the frustration of routing everything through one central VPN hub. Latency creeps up, traffic piles on, and performance dips. If you’ve run into this before, a Dynamic Multipoint VPN (DMVPN) might be a perfect solution for you. A DMVPN lets branch offices establish secure, direct tunnels on demand, so you don’t always have to rely on the main hub.
In this guide, we’ll walk through what a DMVPN is, how it works, and when it’s a smarter choice than a standard site-to-site VPN.
How Does a Dynamic Multipoint VPN Work?
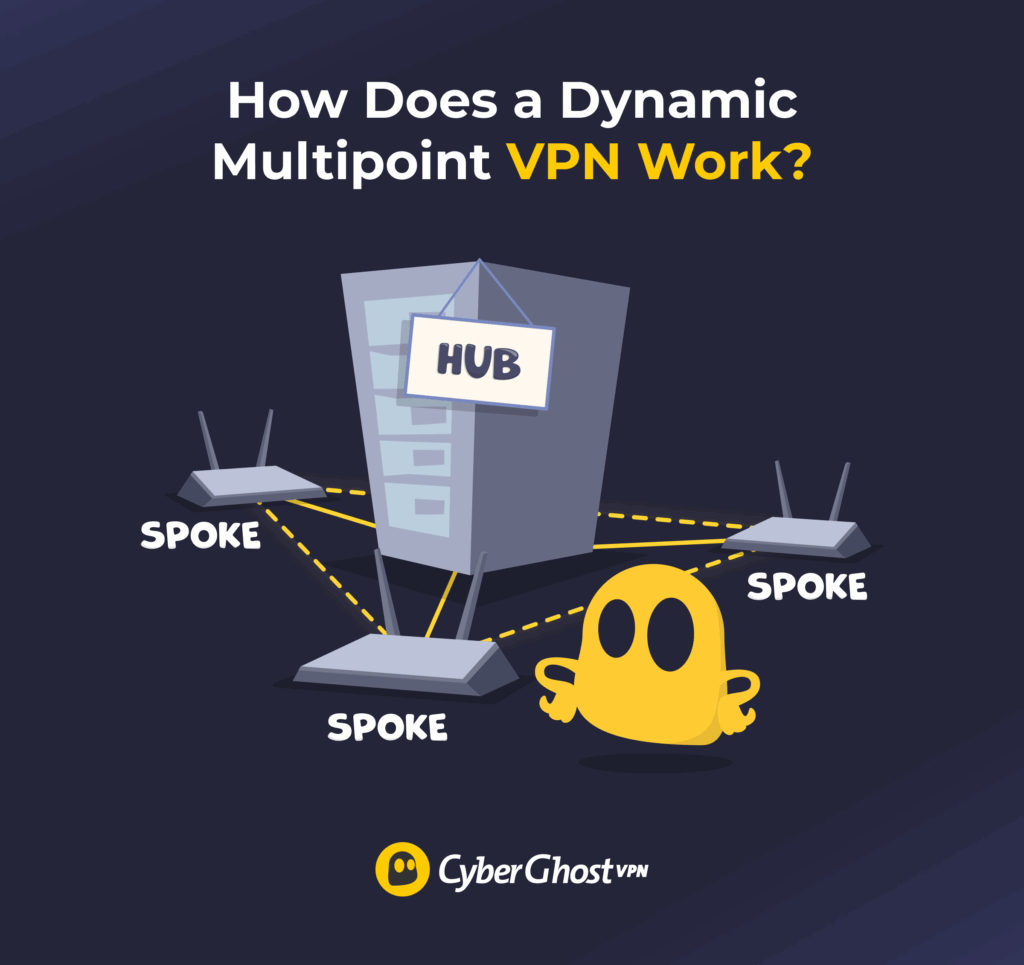
A DMVPN is a type of network configuration that lets multiple remote locations establish a virtual WAN (wide area network) and communicate through an internet connection. It’s an example of a hub and spoke network. Each of these remote locations (“spokes”) has its own router configured to connect to the central DMVPN server, or the “hub.”
The DMVPN’s central hub stores information about every site’s router. When one site wants to connect to another (for example, to transfer a file or start a VoIP call), it first connects to the hub. It asks the hub for the recipient site’s information, like its dynamic IP address. The first spoke then uses this information to create its own secure VPN tunnel directly to the recipient spoke.
Components of a Dynamic Multipoint VPN
MGRE
Multipoint Generic Routing Encapsulation (mGRE) is a tunnel interface that uses the Generic Routing Encapsulation tunneling protocol. It essentially allows a DMVPN’s hub and spokes to create secure tunnels between each other. However, instead of creating a separate GRE tunnel interface for every connection, mGRE creates one interface for the whole network. This makes the network simpler to manage because the router doesn’t have to keep track of lots of different interfaces. It also means new sites can be added without having to set up and configure a new interface every time.
NHRP
To exchange data with another site, a DMVPN spoke needs the target spoke’s public IP address. The Next Hop Resolution Protocol (NHRP) is the method a DMVPN uses to keep track of and communicate network address information. The DMVPN’s hub stores a database of every router’s public IP and its tunnel IP (a private address given to each router on the network). When one spoke wants to connect to another, it uses NHRP to ask the database for the public IP address that corresponds to the tunnel IP for the target spoke.
Routing Protocols
Routing protocols help the DMVPN find efficient routes for traffic between different spokes. DMVPNs typically support multiple protocols, depending on the size of the network. For example, OSPF works well with smaller networks because it’s simpler to set up and it updates routes quickly, as long as there aren’t too many. EIGRP and BGP are more suitable for bigger networks because they can handle large numbers of routes and give admins finer-tuned control over traffic.
IPsec
IPsec is a security protocol that encrypts data traveling between the hub and the spokes, as well as between the spokes themselves. This way, any sensitive information the spokes exchange remains secure as it goes through the internet connection. Even if that connection gets intercepted, snoopers will only see scrambled, encrypted data.
Phases of Dynamic Multipoint VPN
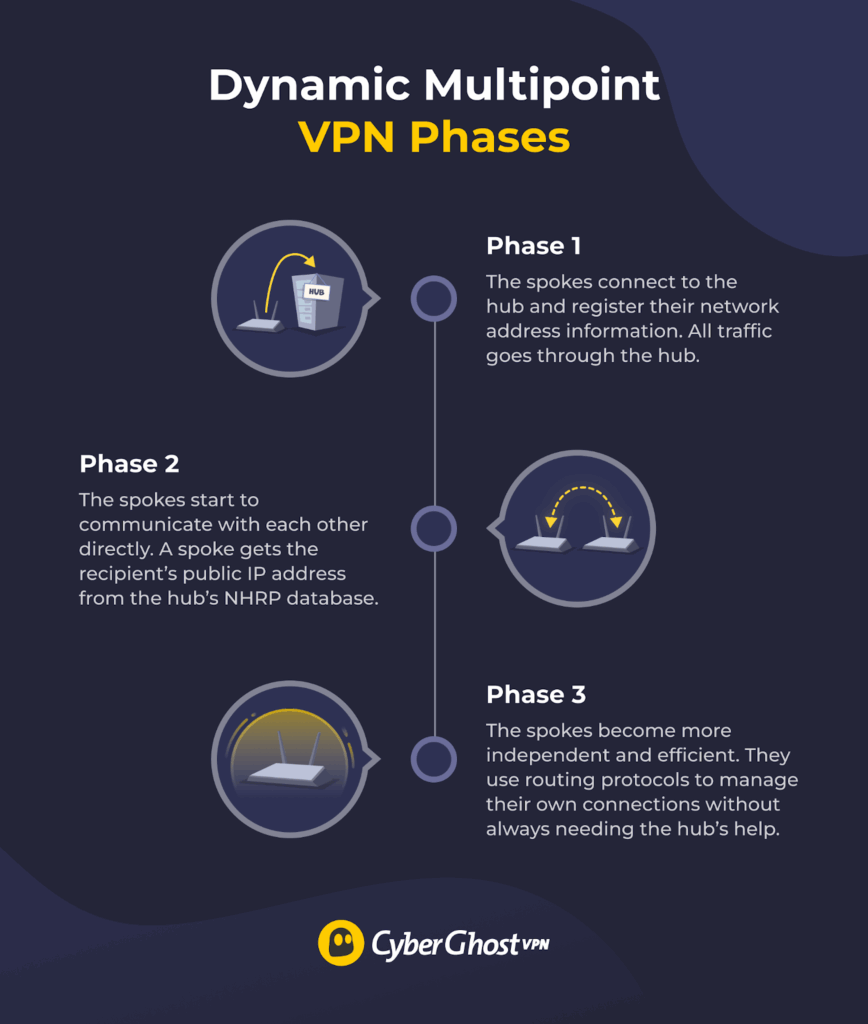
A DMVPN works by implementing its components in phases:
Phase 1
First, every spoke is securely connected to the hub using IPsec. The hub then uses NHRP to create a registry of the spokes’ IP addresses. The routing configuration in this phase is simple because there isn’t any direct communication between the spokes themselves; all traffic has to go through the hub first.
Phase 2
Next, the VPN routers on each spoke use mGRE, so the spokes can communicate with each other directly instead of through the hub. When a spoke wants to open a connection to another spoke, its router sends an NHRP request to the hub so it can get the recipient spoke’s IP address and create a spoke-to-spoke tunnel.
Phase 3
Lastly, once the hub sets up the initial connections, the spokes become more efficient and depend less on the hub. Using optimized routing protocols, the spokes can start sharing routing information directly with each other instead of always relying on the hub each time. They also use NHRP to keep track of the network’s layout, so it’s easy to integrate new spokes into the DMVPN.
Advantages of a Dynamic Multipoint VPN
- Simplified management: Maintaining the network is fairly simple. Despite the complex setup, the DMVPN’s components are only configured once, and then the network itself dynamically handles opening and closing new tunnels.
- Scalability: Adding a new remote site as a spoke to the network is easy. Once the new spoke gets a configured VPN router, the network integrates it so it can immediately establish connections to any other spoke.
- Reduced bandwidth use: Communicating directly from spoke to spoke means the hub conserves its bandwidth. It also decreases latency on the network by preventing the hub from becoming a bottleneck.
Disadvantages of a Dynamic Multipoint VPN
- Complex setup: Establishing a DMVPN is significantly more complex than a simple IPsec VPN. It has a lot of dynamically interacting components, so one small misconfiguration can cause a lot of trouble down the line.
- Better for larger networks: If the network has a very small number of remote sites, using a simple centralized VPN is easier and cheaper.
- Complicated troubleshooting: The dynamic nature of the system can also make troubleshooting more difficult. Because the tunnels are opened and closed on demand, figuring out where a problem lies can be more difficult than with a “traditional” static or always-on VPN.
Differences Between a Dynamic Multipoint VPN and Other Enterprise VPN Types
| DMVPN | Traditional Site-to-Site VPN | Remote-Access VPN | |
| What it does | Dynamically connects multiple sites by creating direct tunnels between them on demand | Connects multiple sites with static VPN tunnels | Connects a single user’s device to a corporate network over the internet |
| Ease of setup | Complex initial setup with advanced configuration | Moderate, requires manual configuration at each site | Simple for small networks, typically involves configuring a central VPN server and downloading client software on user devices |
| Ease of management | Minimal admin after setup | Manageable for a few sites, but becomes more difficult with scale | Becomes more complex as the network grows |
| Scalability | Great, adding new sites is very simple | Poor, becomes hard to deploy and manage on a large number of sites | Moderate, adding large numbers of users requires specialized updates |
| Traffic path | Directly spoke-to-spoke | All traffic goes through a central VPN server | Traffic goes between the client device and the corporate network’s gateway |
| Topology | Dynamic, spoke-to-spoke | Static, hub-and-spoke | Static, user-to-network |
| Performance | Direct tunnels prevent bottlenecks | A central server can create bottlenecks | Performance can depend on the user’s internet connection |
| Best application | Large networks where spoke-to-spoke communication isn’t constant | A small number of sites that require constant direct connections | Providing remote access to shared applications and resources |
Looking for a personal VPN? Not to be confused with an enterprise VPN, a personal VPN is an online privacy app you can download on your device. CyberGhost VPN encrypts your internet connection, making it harder for anyone to snoop on your online activity. It also masks your real IP address, protecting your identity and allowing you to browse as though you’re in another country.
Is a DMVPN the Right Choice for Your Network?
A dynamic multipoint VPN (DMVPN) lets remote sites connect directly to each other instead of always routing traffic through a central server. This direct connection speeds up communication and reduces strain on the main hub. It’s also scalable, since adding new sites to the network is very easy.
However, the DMVPN model requires a complex initial setup. Its complexity can also make it harder to troubleshoot. Small networks are generally better off with a traditional site-to-site VPN, as it’s simpler to set up. DMVPNs are better suited for enterprises with a large number of remote sites in the network.
FAQ
What is a dynamic multipoint VPN?
A DMVPN is a type of network architecture that allows multiple remote sites to connect securely to each other. It dynamically creates direct tunnels between sites on demand, instead of forcing all traffic through a single central hub. It’s very scalable, so it’s an efficient model for large networks with lots of remote sites.
How does a multipoint VPN differ from a traditional VPN?
The primary difference is the way they handle remote sites. Traditional VPNs use a static model where all traffic goes through a central server. A multipoint VPN lets remote sites establish direct tunnels with each other. This removes the potential bottleneck point at the central server and helps conserve bandwidth.
What are the benefits of using a dynamic multipoint VPN in enterprise networks?
One of the main advantages is the DMVPN’s scalability, as adding new remote sites to the network requires very little configuration. It also reduces latency because the spokes communicate directly with one another and not through the hub. This makes network management much simpler for large enterprises.
Is a dynamic multipoint VPN secure for remote communication?
Yes, the DMVPN model is highly secure. It uses the IPsec protocol to encrypt all data transmitted between the spokes and the hub, as well as between the spokes themselves. This means they can exchange sensitive data securely.
Can I use DMVPN for cloud connectivity?
Yes, a cloud-based virtual router can serve as the central hub. All the remote sites can establish secure, encrypted tunnels to the cloud hub. This allows branches to access cloud applications and data, as well as communicate with each other directly.
What protocols are commonly used with multipoint VPNs?
DMVPN primarily uses a combination of three protocols. NHRP (Next Hop Resolution Protocol) manages the spokes’ network address information. mGRE (multipoint generic routing encapsulation) creates a single tunnel interface for multiple endpoints. Lastly, IPsec provides strong traffic encryption and security.


Leave a comment