So much for the peace of mind most of us had each time we enabled 2FA! Cybercriminals bypassing MFA(Multi-Factor Authentication) isn’t exactly new, as researchers have reported similar events before. This time, the situation is worse because over 1,200 phishing toolkits were found on sale on the dark web. Now, whoever wants to learn and practice this new skill can easily do so. And one doesn’t have to be a math expert to realize that we’ll see the trend of cybercrooks bypassing 2FA more and more.
The question is can you do something to prevent it? There’s actually some good news. Check the details below.
The Inner Workings of a 2FA Bypass
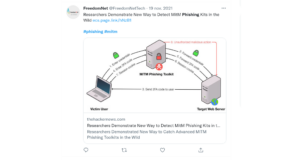
Cybercriminals’ first attempts to bypass 2FA relied on voice phishing (fraudulent phone calls) and tricking users into revealing the random code under a false pretext. This technique is still present but left in the background. Today’s more sophisticated method to bypass 2FA or MFA is with the help of stealing cookie sessions via a MiTM (Man-in-the-Middle) attack. Yet, a phishing site stands at the core of the method.
A session cookie is a way a server knows that a user has already authenticated. It’s usually valid for just that session or a very short period.
Here’s how a MiTM phishing attack unfolds using a phishing tool that can extract user session cookies:
- The attackers send a phishing email to the victim.
- When the victim clicks on the phishing link, the attacker can see and read the information the victim fills in (username and password). All data inserted in the phishing site is redirected to attackers’ server.
- The website requests the victim to identify using a 2FA method.
- The victim types the 2FA code on the phishing site.
- The attackers have now captured the username, password, and token, the latter representing the session cookie sent from the servers of the website to the browser.
- The attackers take that session cookie and place it in their web browser via a cookie editor browser app; this way, they impersonate the user, aka the victim.
- The attackers go to the legitimate website, and instead of typing a username and password, they simply use the captured session token.
A cookie editor browser app allows anyone to export and import cookies into different browsers. For instance, you can export Outlook session cookies from Chrome and import them into Firefox.
Other Popular Methods Cybercriminals Use to Bypass 2FA
Spoofing & Phishing
Cybercriminals combine old-fashioned spoofing with phishing to intercept and read your SMS messages.
SMS messages are in plain text, and they’re not encrypted between sender and receiver; if attackers can intercept the message, they can read the content.Bad actors can also apply phishing techniques and trick you into installing malware on your phone. They can craft malware that mimics one-time SMS passcodes and usernames and passwords for websites and apps. Once you install and start using the malicious software, the malware sends the information right back to the attacker.
Remote Desktop Protocol (RDP)
RDP attacks started to increase along with the pandemic and the rise of remote work. Most RDP schemes work exactly like typical brute-force attacks, but some involve SIM swapping. In this case, cybercrooks convince employees from a phone company to install or activate RDP software. After that, they connect remotely to the company’s phone network systems and SIM swap users of the phone company. They can capture phone numbers and SMS authentications.
Social Engineering
Attackers can impersonate you and call your phone company requesting a new SIM card. They usually come up with the story the old SIM got lost or was stolen. The new issued SIM will automatically make your initial phone SIM become inaccessible and out of service, so you can’t use it anymore.
The bad actors can pin down the new SIM they requested and fully control it, even requesting new SMS 2FA codes.
Another social engineering tactic is cybercriminals getting in touch with various companies claiming to help them with SMS marketing. After getting entire lists of phone numbers, they reroute SMS messages to themselves.
How to Avoid Becoming a Victim of a 2FA Bypass Attack
In an ideal world, cybersecurity experts would identify all these MiTM phishing toolkits within all networks and blocklist all phishing websites. Currently, researchers use several tools that work exactly for this purpose, but it’s a work in progress for the most part.
You can pull off a few tricks to overcome being a victim of a 2FA bypassing attack. This doesn’t mean you should forget about MFA. It still remains an important requirement within professional environments and a security step you shouldn’t skip.
Still, if you’re looking for an alternative to 2FA, here are some examples:
-
-
- Biometrics, like a fingerprint – it’s a more secure method as they’re harder to replicate and intercept.
- TOTP (Time-based One-Time Password) tokens – also known as app-based authentications or software tokens; TOTPs are unique numeric passwords based on a standardized algorithm. Because they have limited validity, making it harder for bad actors to exploit them.
- Hardware tokens like the YubiKey – similar to a USB stick, place the YubiKey into your computers’ USB port. With every login to a website or app, you just push a button on the YubiKey and get a one-time password to authenticate.
-
To boost your online security further, remember to always:
-
-
- Create strong passwords
- Use only genuine authenticator apps (e.g., Google authenticator, Microsoft authenticator, etc.).
- Avoid sharing your security codes with anyone.
- Beware of the betraying signs of phishing attacks; the rule of thumb: always scrutinize URL links!
- Secure your cookies with the HttpOnly Attribute in the Set-Cookie HTTP header section in your browser. This way, you stop your browser from revealing your session cookies to third parties.
- Clear your cookies with an ideal 3-in-1 cookie, history & cache cleaner from CyberGhost.
- Use a VPN on public Wi-Fi. Open hotspots are utterly convenient, but they’re attackers’ honey pot! They’re notorious for Man-in-the-Middle attacks and stealing session cookies. A VPN is your easy workaround to stay safe and protect yourself against these threats.
-
Have you ever been the victim of a session cookie attack?
Let me know in the comments below.



Leave a comment